Azure Tips & Tricks: How you can easily isolate a broken VM from the Production or QA environment in Azure

Hello Friends, from this month onwards, I will write about the few interesting Tips & Ticks which may help you in your day to day Azure deployments.
I think you might have faced situation where you need to isolate the VM from the production or QA network for the troubleshooting purpose. This is mostly required when you need to troubleshoot VM’s in the DR site. During a DR scenario, although the DR VM will get a new IP address, however still you can’t boot the VM since it will have the same FQDN(Fully Qualified Domain Name) which is already registered in DNS server with a different IP.
Today I will show you how you can easily isolate this VM with the help of NSG (Network Security Group).
In the first step, you need to create a new network security group as shown below.
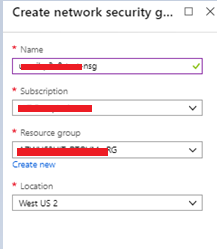
Once it’s created you can see the notification
Once it’s created you need to add a new rule to deny to all the connections to the VM both incoming and outbound and set the priority lower than existing default rules. However since you should be able to RDP to the VM over 3389, so you need to set up another new rule inbound rule with lower priority as shown below.
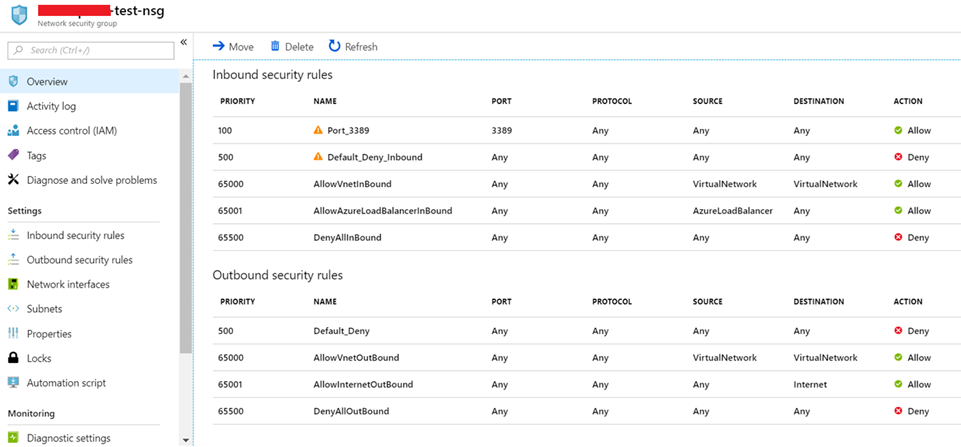
Once it’s created you can assign this NSG to the VM which you would like to troubleshoot. That’s all for today. I hope this will help you in a certain scenario in the future.
I’ll bring more tips in the future. Have a good day ahead.


