Best Practices for Azure Virtual Desktop (AVD)
Today I will publish the best practices for implementing the Azure Virtual Desktop (AVD). This is a very detailed article.
- Azure Virtual Desktop Enterprise Architecture
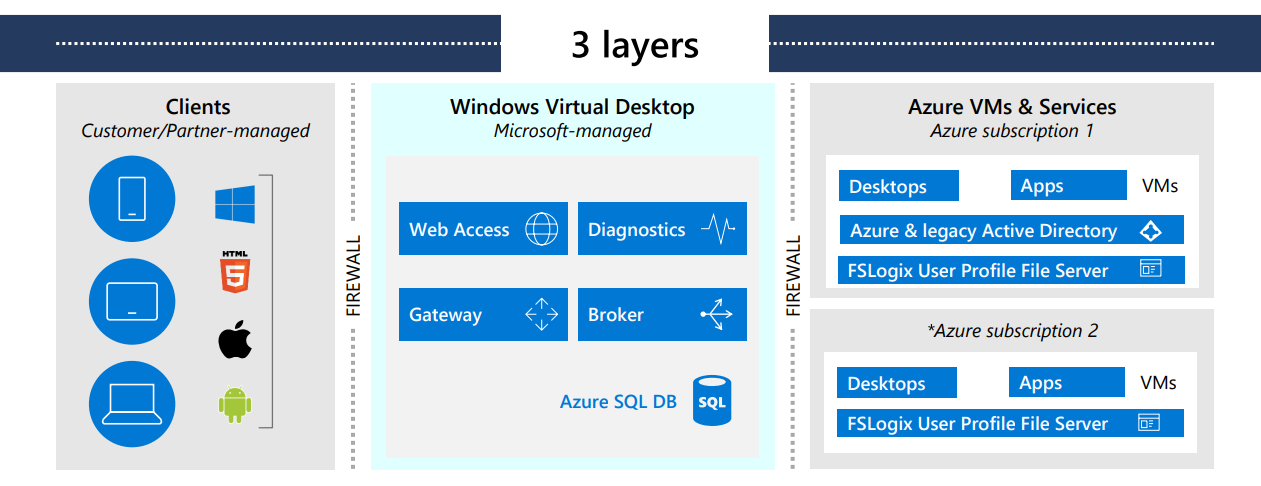
Link for reference:
Azure Virtual Desktop for the enterprise – Azure Architecture Center | Microsoft Learn
- Azure Virtual Desktop Limitations
| Azure Virtual Desktop object | Per Parent container object | Service limit |
| Workspace | Azure Active Directory tenant | 1300 |
| Host Pool | Host Pool | 400 |
| Application group | Azure Active Directory tenant | 500* |
| RemoteApp | Application group | 500 |
| Role assignment | Any Azure Virtual Desktop object | 200 |
| Session host | HostPool | 10,000 |
| Per Azure subscription Per region | 5000 VMs | |
| Automated session-host scaling tools | Per Azure subscription Per region | 2,500 VMs |
| Azure Resource Manager (ARM) | Subscription API throttling limits | 600 Azure VM reboots per hour via the Azure portal |
- Hub and spoke with hybrid connectivity.
Here are some general design considerations and recommendations for Azure Virtual Desktop network topology and connectivity:
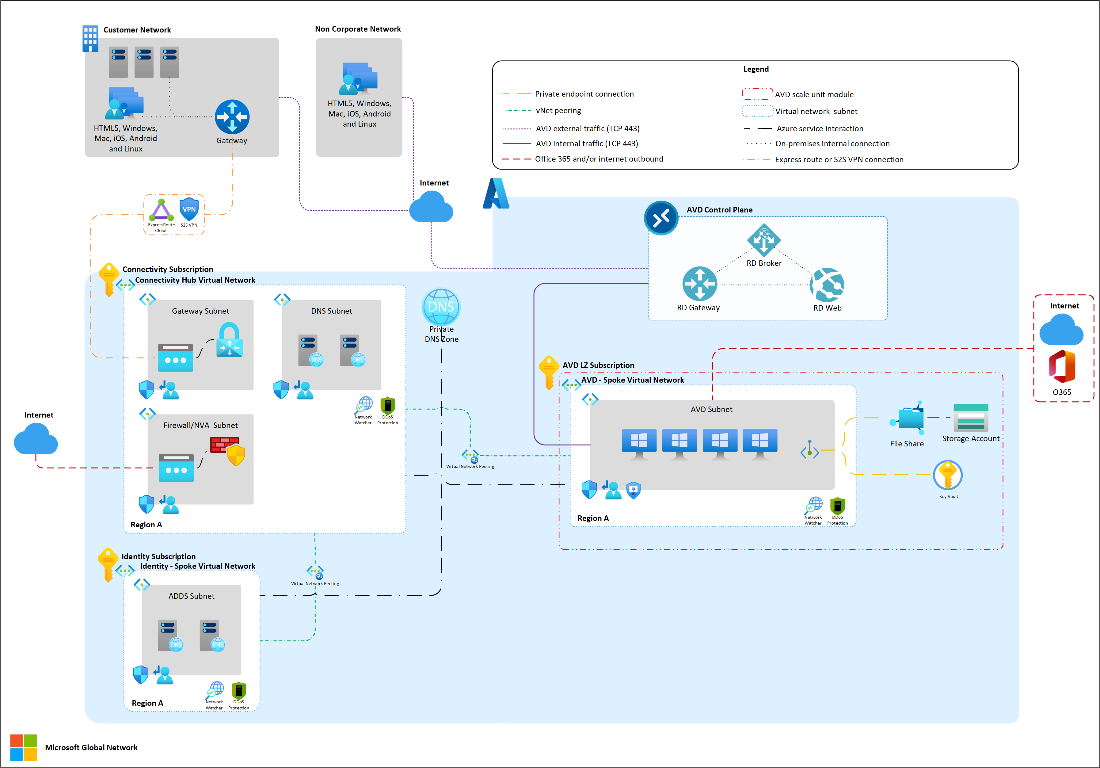
Considerations:
- This scenario doesn’t account for client direct network connectivity to session public or private (no RDP Shortpath) hosts.
- Azure Virtual Desktop control plane gateway (public endpoint) and manages client connections. Therefore, Azure Virtual Desktop clients can create outbound connections to required Azure Virtual Desktop URLs. For more information, see Required URLs for Azure Virtual Desktop https://learn.microsoft.com/en-us/azure/virtual-desktop/safe-url-list?tabs=azure .
- No public IPs or any other public inbound path to session hosts is needed, traffic from clients to session hosts flows through Azure Virtual Desktop control plane gateway.
- No virtual network peering between Azure Virtual Desktop spokes, all the traffic goes through the connectivity hub.
- Outbound internet connection from Azure Virtual Desktop session hosts goes through the default Azure outbound NAT using dynamic Azure public IPs (no customer control on outbound public IPs used).
- Connections from session hosts to Azure Files (storage accounts) are established using private endpoints.
- Azure private DNS zones are used to resolve private endpoint namespaces:
- Storage account file service (privatelink.file.core.windows.net).
- Key vaults (privatelink.vaultcore.azure.net).
- Even though for this scenario network filtering is not enforced, NSGs are placed on all subnets to enable monitoring and insights by using network watcher NSG flow logs and traffic analytics.
3: Microsoft Recommended Workload/Users/Apps
Users are the types of users that might find each workload most helpful. Example apps are the kinds of apps that work best for each workload.
| Workload Type | Example Users | Example Apps |
| Light | Users doing basic data entry tasks | Database entry applications, command-line interfaces |
| Medium | Consultants and market researchers | Database entry applications, command-line interfaces, Microsoft Word, static web pages |
| Heavy | Software engineers, content creators | Database entry applications, command-line interfaces, Microsoft Word, static web pages, Microsoft Outlook, Microsoft PowerPoint, dynamic web pages, software development |
| Power | Graphic designers, 3D model makers, machine learning researchers | Database entry applications, command-line interfaces, Microsoft Word, static web pages, Microsoft Outlook, Microsoft PowerPoint, dynamic web pages, photo and video editing, computer-aided design (CAD), computer-aided manufacturing (CAM) |
Master Image Management
The master image can be managed by already existing process and technologies, including:
- Azure Update management
- Microsoft Endpoint Configuration Manager
- Azure Compute Galleries
- Azure Image Builder Automation
- Azure DevOps Pipelines
Microsoft Recommended VM Sizing
Multi-session sizing recommendations:
| Workload type | Maximum users per vCPU | Minimum vCPU/RAM/OS storage | Example Azure instances | Minimum profile storage |
| Light | 6 | 8 vCPUs, 16 GB RAM, 32 GB storage | D8s_v5, D8s_v4, F8s_v2, D8as_v4, D16s_v5, D16s_v4, F16s_v2, D16as_v4 | 30 GB |
| Medium | 4 | 8 vCPUs, 16 GB RAM, 32 GB storage | D8s_v5, D8s_v4, F8s_v2, D8as_v4, D16s_v5, D16s_v4, F16s_v2, D16as_v4 | 30 GB |
| Heavy | 2 | 8 vCPUs, 16 GB RAM, 32 GB storage | D8s_v5, D8s_v4, F8s_v2, D8as_v4, D16s_v5, D16s_v4, F16s_v2, D16as_v4 | 30 GB |
| Power | 1 | 6 vCPUs, 56 GB RAM, 340 GB storage | D16ds_v5, D16s_v4, D16as_v4, NV6, NV16as_v4 | 30 GB |
Single-session sizing recommendations:
| Workload type | vCPU/RAM/OS storage minimum | Example Azure instances | Profile container storage minimum |
| Light | 2 vCPUs, 8 GB RAM, 32 GB storage | D2s_v5, D2s_v4 | 30 GB |
| Medium | 4 vCPUs, 16 GB RAM, 32 GB storage | D4s_v5, D4s_v4 | 30 GB |
| Heavy | 8 vCPUs, 32 GB RAM, 32 GB storage | D8s_v5, D8s_v4 | 30 GB |
FSLogix Agent Architecture
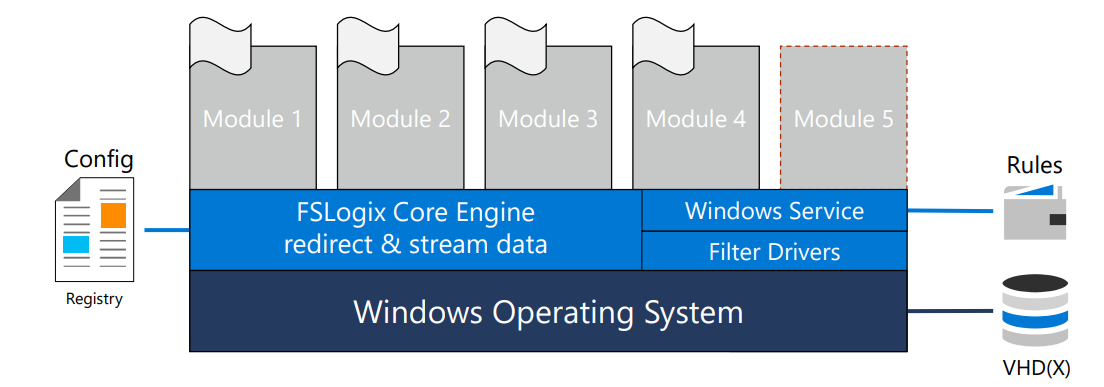
To the operating system, FSLogix Containers attach seamlessly as in-guest VHD(X)s and they are in distinguishable from local folders.
Managed Storage options for FSLogix
Storage options for FSLogix consideration in Azure virtual desktop. Please refer below table.
| Features | Azure Files | Azure NetApp Files | Storage Spaces Direct |
| Use case | General purpose | General purpose to enterprise scale | Cross-platform |
| Platform service | Yes, Azure-native solution | Yes, Azure-native solution | No, self-managed |
| Regional availability | All regions | Select regions | All regions |
| Redundancy | Locally redundant/zone-redundant/geo-redundant/geo-zone-redundant | Locally redundant/geo-redundant with cross-region replication | Locally redundant/zone-redundant/geo-redundant |
| Tiers and performance | Standard (Transaction optimized) Premium Up to max 100K IOPS per share with 10 GBps per share at about 3-ms latency | Standard Premium Ultra Up to max 460K IOPS per volume with 4.5 GBps per volume at about 1 ms latency. For IOPS and performance details, see Azure NetApp Files performance considerations and the FAQ. | Standard HDD: up to 500 IOPS per-disk limits Standard SSD: up to 4k IOPS per-disk limits Premium SSD: up to 20k IOPS per-disk limits We recommend Premium disks for Storage Spaces Direct |
| Capacity | 100 TiB per share, up to 5 PiB per general purpose account | 100 TiB per volume, up to 12.5 PiB per NetApp account | Maximum 32 TiB per disk |
| Required infrastructure | Minimum share size 1 GiB | Minimum capacity pool 2 TiB, min volume size 100 GiB | Two VMs on Azure IaaS (+ Cloud Witness) or at least three VMs without and costs for disks |
| Protocols | SMB 3.0/2.1, NFSv4.1 (preview), REST | NFSv3, NFSv4.1, SMB 3.x/2.x, dual-protocol | NFSv3, NFSv4.1, SMB 3.1 |
Azure Files – sizing recommendations
• Storage account name cannot be larger than 15 characters (AD/NETBIOS limit)
• Azure Files standard and Premium operate different
- • Azure Files standard à 10,000 IOPs
- • Premium Files à based on size – consumption – max. 100,000 IOPs
• The (internal) rule of the thumb is that one user consumes 10 IOPS in Steady state and 50 IOPS Sign in/sign out IOPS (depending on the type of workload)
| Workload type | File Tiers |
| Light | Standard file shares |
| Medium | Standard file shares Premium file shares |
| Heavy | Premium file shares |
| Power | Premium file shares |
FSLogix Configuration Settings Recommendations
Profile Container Settings:
| Decision Point | Recommended Settings | Justification |
| Profile Management Version | FSLogix Apps 2.9.8228.50276/2.9.8171.14983 | The latest version at the time of writing. The latest version should be assessed and utilised where appropriate. This agent is installed within the Azure marketplace image. The latest version available at time of deployment should be utilised. |
| Profile Container | Enabled | FSLogix will be used to manage profiles for the solution. |
| Office Container | Enabled (optional) | The Office container stores just the Microsoft Office portion of the profile and is utilised to spread storage load over various storage locations. |
| Note, Microsoft Office data is stored in the profile container when the Office container is not utilised, this can simplify the deployment. See Profile Container vs. Office Container. | ||
| Cloud Cache | Not configured | VHDLocations will be used in preference of Cloud Cache (CCDLocations) in this pattern due to the resilience and performance using NetApp Files or Azure files seen when appropriately configured for the size of the user base. |
| Agencies are encouraged to test CCDLocations if resilience and availability is a problem. | ||
| Profile Container Logging | Enabled (All logs enabled) | Logging is to be enabled for FSLogix. |
| Enable Search Roaming | Disabled | FSLogix search functionality is not compatible with Server 2019, Windows 10 multi-session and should be disabled, and subsequent multi-session operating systems with enhanced native search capabilities. |
| Search Database Configuration | Not applicable | FSLogix search functionality is not compatible with Server 2019, Windows 10 multi-session. |
| Outlook Cached Mode | Enabled | FSLogix Outlook Cached mode will be configured to provide the best user experience. |
| Dynamic VHD(X) Allocation | Enabled | Dynamic VHD(X) will be configured to provide storage cost savings where possible. |
| Profile Virtual Disk Location | Agency decision point: Azure Files or Azure NetApp Files for Storage Account. | Each user will have a FSLogix virtual disk stored to an Azure location in Australia with data geo-replicated to a secondary location for DR purposes. |
| Storage Account Name/s: TBD – Share that will be used for profiles | Depending on required usage, performance and disaster recovery requirements, the agency must decide between Azure Files and Azure NetApp files depending on their requirements or consider the Cloud Cache option (out of scope for this blueprint). | |
| Virtual Disk Type | VHDX | VHDX is the latest available disk type and suitable for this solution. |
| Allow concurrent users sessions | Enabled | Concurrent user sessions must be enabled to allow multi-session desktop scenarios. |
| Delete local profile when FSLogix Profile should apply | Enabled | To provide the use a clean desktop session on each desktop launch, it is recommended to enable this setting. |
| Redirections File Path | Azure Storage account or other domain share | The redirections configuration XML will be hosted on a common share, to be determined by the agency. |
| Redirection Exclusions | Copy Redirections.xml file to [TBD-DOMAIN]\NETLOGON\FsLogix\ | It is recommended to use the redirections file with caution. Base configuration recommended initially. |
| See recommended crowd sourced redirections.xml for base inclusions. | Note, the folder path to the redirections.xml path is set through Group Policy and points to the folder where the file exists, not the full path of the file itself. | |
| For structure and creation of the file see Structure of redirections.xml file. | ||
| Swap directory name components | Enabled: Swap directory name components | This configuration allows for easier navigation of the user VHDX folders when troubleshooting and during maintenance. |
Office Container Settings:
| Decision Point | Recommended Settings | Justification |
| O365 Virtual Disk Location | Network Share: [TBD – Network Share to be used for Virtual Disks] | Each user will have a FSLogix virtual disk stored to an Azure location in other region with data geo-replicated to a secondary location for DR purposes. |
| Virtual Disk Access type | Unique disk per session | Required for this deployment type and provides support for OST and OneDrive. |
| Virtual Disk Type | VHDX | VHDX is the latest available disk type and suitable for this solution. |
| O365 Container Logging | Enabled | Logging is to be enabled for FSLogix. |
| Concurrent Users Sessions | Allowed | Concurrent user sessions must be enabled to allow multi-session desktop scenarios. |
| Office 365 Activation Data | Enabled | Office 365 activation data will be stored in the O365 container. |
| Office Cache Data | Enabled | Office 365 cache data will be stored in the O365 container. |
| OneDrive Data | Enabled | OneDrive data will be stored in the O365 container. |
| OneNote Data | Enabled | OneNote data will be stored in the O365 container. |
| Outlook Data | Enabled Outlook data will be stored in the O365 container. | Outlook data will be stored in the O365 container. |
| Outlook Personalisation Data | Enabled | Outlook personalisation data will be stored in the O365 container. |
| SharePoint Data | Not configured | Not configured |
| Teams Data | Disabled | Team’s data will not store in the O365 container. This allows optimisation of the profile size in the Profile container to avoid profile bloat. |
| Outlook Container Mode | Cached | Outlook cached mode will be enabled on successfully container attach. |
| Dynamic VHD(x) | Enabled | Dynamic VHD(x) will be utilised to save on required space. Disks will grow only as space is required. |
| Search Roaming | Disabled | FSLogix search functionality is not compatible with Server 2019, Windows 10 multi-session and should be disabled, and subsequent multi-session operating systems with enhanced native search capabilities. |
| Search Database | Not applicable | FSLogix search functionality is not compatible with Server 2019, Windows 10 multi-session. |
| Sync OST to VHD | Enabled: Move OST to VHD | Existing OST’s are sync’d to VHD/X when new VHD/X is created. |
| Swap directory name components | Enabled: Swap directory name components | This configuration allows for easier navigation of the user VHDX folders when troubleshooting and during maintenance. |
FSLogix AV Exclusions
Make sure to configure the following Antivirus exclusions for FSLogix Profile Container – virtual hard drives. Make sure to pass the following information against security team.
- Exclude Files:
- %ProgramFiles%\FSLogix\Apps\frxdrv.sys
- %ProgramFiles%\FSLogix\Apps\frxdrvvt.sys
- %ProgramFiles%\FSLogix\Apps\frxccd.sys
- %TEMP%\*.VHD
- %TEMP%\*.VHDX
- %Windir%\TEMP\*.VHD
- %Windir%\TEMP\*.VHDX
- \\storageaccount.file.core.windows.net\share\*\*.VHD \\storageaccount.file.core.windows.net\share\*\*.VHDX
- Exclude Processes
- %ProgramFiles%\FSLogix\Apps\frxccd.exe
- %ProgramFiles%\FSLogix\Apps\frxccds.exe
- %ProgramFiles%\FSLogix\Apps\frxsvc.exe
Configure SMB Storage Permissions
FSLogix works with SMB storage systems to store Profile or ODFC containers. SMB storage is used in standard configurations where VHDLocations holds the UNC path to the storage locations. SMB storage permissions rely on traditional NTFS Access Control Lists (ACL) applied at file or folder levels to ensure the proper security of the data that is stored. When used with Azure Files, you must enable an Active Directory (AD) source, and then assign share-level permissions to the resource.
The table outlines the recommended ACL(s) to be configured.
| Principal | Access | Applies to | Description |
| CREATOR OWNER | Modify (Read / Write) | Subfolders and files only | Ensures the profile directory created by the user has the correct permissions only for that user. |
| Domain Admins | Full Control | This folder, subfolders and files | Replace with your organizations group used for administrative purposes. |
| Domain Users | Modify (Read / Write) | This folder only | Enables authorized users to create their profile directory. Replace with organizational users who need access to create profiles. |
Microsoft Teams and Azure Virtual Desktop
Prepare network:
Teams is designed to give the best audio, video, and content-sharing experience regardless of network conditions. That said, when bandwidth is insufficient, Teams prioritizes audio quality over video quality. Please refer to the table below:
| Bandwidth(up/down) | Scenarios |
| 30 kbps | Peer-to-peer audio calling |
| 130 kbps | Peer-to-peer audio calling and screen sharing |
| 500 kbps | Peer-to-peer quality video calling 360p at 30fps |
| 1.2 Mbps | Peer-to-peer HD quality video calling with resolution of HD 720p at 30fps |
| 1.5 Mbps | Peer-to-peer HD quality video calling with resolution of HD 1080p at 30fps |
| 500kbps/1Mbps | Group Video calling |
| 1Mbps/2Mbps | HD Group video calling (540p videos on 1080p screen) |
Team’s exclusions:
Make sure data in these two folders are synced:
- C:\Users\username\AppData\Local\Microsoft\IdentityCache (%localAppdata%\Microsoft\IdentityCache)
- C:\Users\username\AppData\Roaming\Microsoft\Teams (%appdata%\Microsoft\Teams)
Exclude the following from the Teams caching folder, %appdata%/Microsoft/Teams. Excluding these items helps reduce the user caching size to further optimize non-persistent setup.
- .txt files
- Media-stack folder
- meeting-addin\Cache (%appdata%\Microsoft\Teams\meeting-addin\Cache)
Note: For Teams optimization configuration, refer this URL: https://learn.microsoft.com/en-us/azure/virtual-desktop/teams-on-avd
Security Best Practices
End to end security for AVD infrastructure consideration
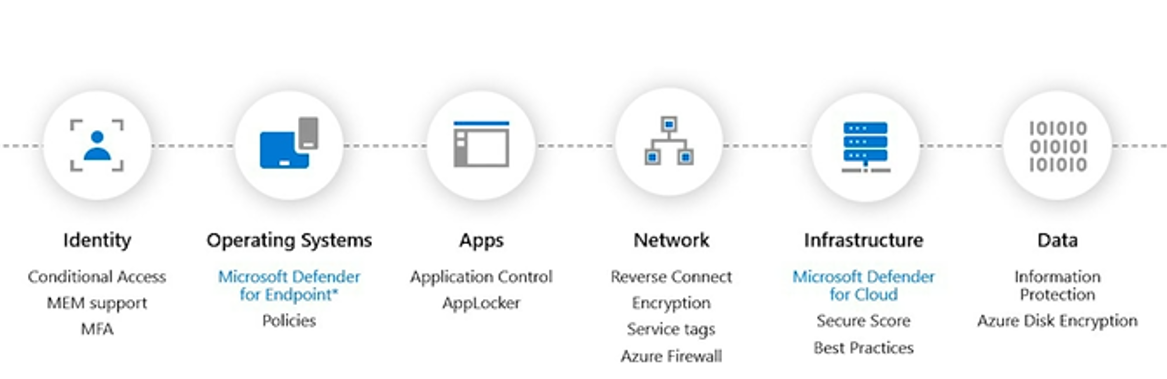
Security controls and best practices:
- Require Multifactor Authentication: Activate Azure MFA for Azure Active Directory (AD) accounts.
- Enable Conditional Access: Configure a conditional access policy and target Azure Virtual Desktop.
- MEM(Intune) support: Windows 10/11 Enterprise multi-session/single session support.
- Hybrid AAD and native AADJ virtual machines – will bring end to end SSO and password-less authentication (Windows Hello, FIDO2)
- Patch software vulnerabilities: Update live host/redeploy using compute gallery images.
- Control device redirection: Look into disabling smart card, port, drives, camera redirection, USB restrictions, printer redirection etc.
- Windows security baseline: Apply windows 10/11 Enterprise security baselines.
- Define group policies: Set time limit for active but idle Remote desktop services sessions. Set time limit for disconnected sessions.
- Antivirus, Endpoint Detection and Response, Network protection, Web content filtering, Attack surface reduction and Threat vulnerability management.
- Reverse Connect – Disable all inbound traffic and Encryption: Secures all traffic.
- RDP Shortpath for managed networks and public networks.
- NSG/Firewall service tags – allow required service URLs.
- Screen Capture Protection – Prevent accidental or deliberate sharing of information via screen sharing apps of snipping tools.
- Enable Azure Defender and Microsoft Defender for Cloud – Provides threat and vulnerability management assessments.
- Operationalize Secure Score: Secure score provides recommendations and best practice advice for increasing security posture.
- Microsoft Information protection – Discover, classify, and protect sensitive information wherever it lives or travels.
- Azure Disk Encryption – Helps protect and safeguard data.
Disaster recovery methods Recommended by Microsoft
The disaster recovery methods we recommend are:
- Configure and deploy Azure resources across multiple availability zones.
- Configure and deploy Azure resources across multiple regions in either active-active or active-passive configurations. These configurations are typically found in shared host pools.
- For personal host pools with dedicated VMs, replicate VMs using Azure Site Recovery to another region.
- Configure a separate “disaster recovery” host pool in the secondary region. During a disaster, you can switch users over to the secondary region.
Pooled Host Pools:
For Shared host pools is recommended to configure “Active-Passive” strategy, where existing resources are split into a primary and secondary region. Normally, enterprise would conduct all of its business in the primary (or “active”) region, but in the event of an emergency, all that is necessary to transition to the secondary (or “passive”) region is to turn off the primary region’s resources (if possible, depending on the severity of the outage) and turn on those in the secondary region. The reference architecture for Active-Passive deployment.
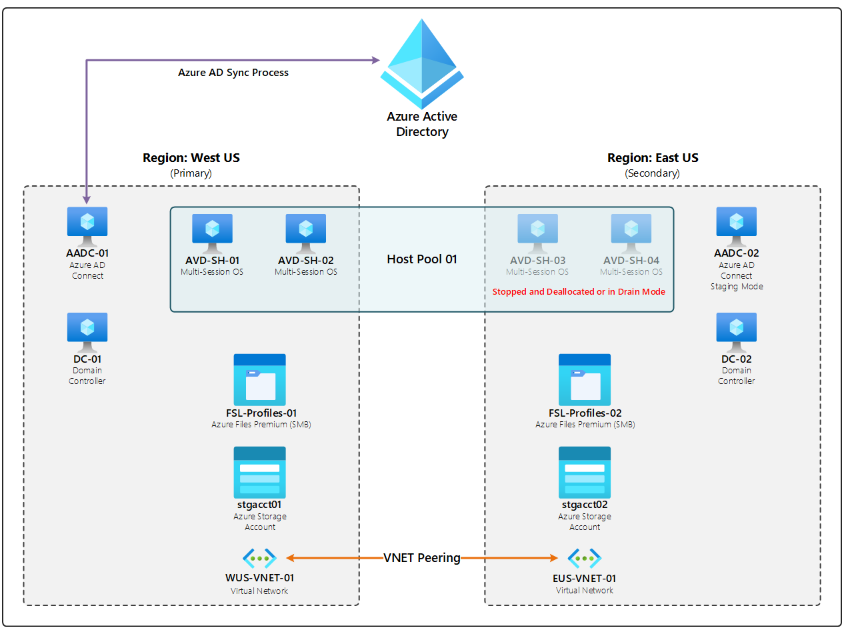
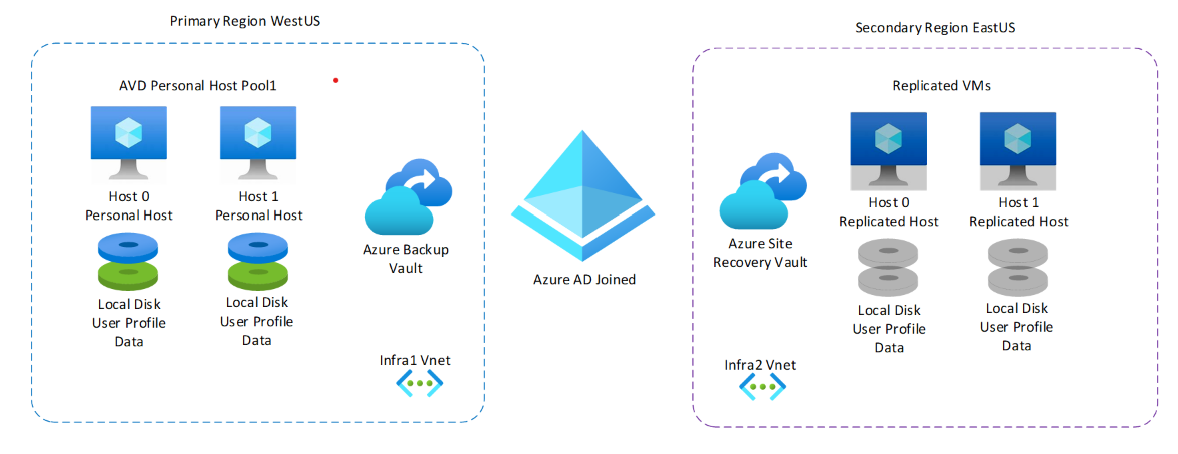
Personal Host Pools:
For personal host pools, the disaster recovery strategy should involve replicating resources to a secondary region using Azure Site Recovery Services Vault. If the primary region goes down during a disaster, Azure Site Recovery can fail over and turn on the resources in the secondary region. The reference architecture for personal host pools deployment.
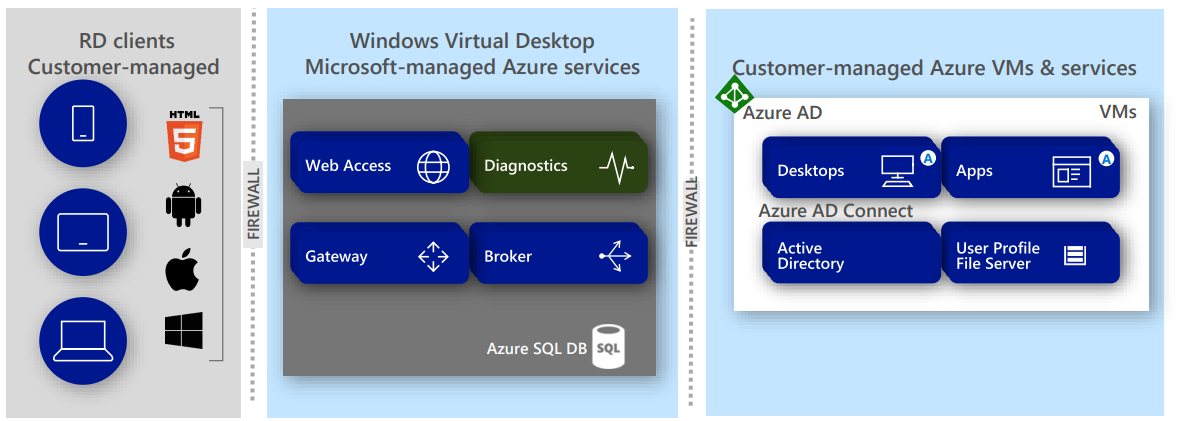
Azure Native Monitoring tool
Diagnostics is a feature of the managed Azure Service
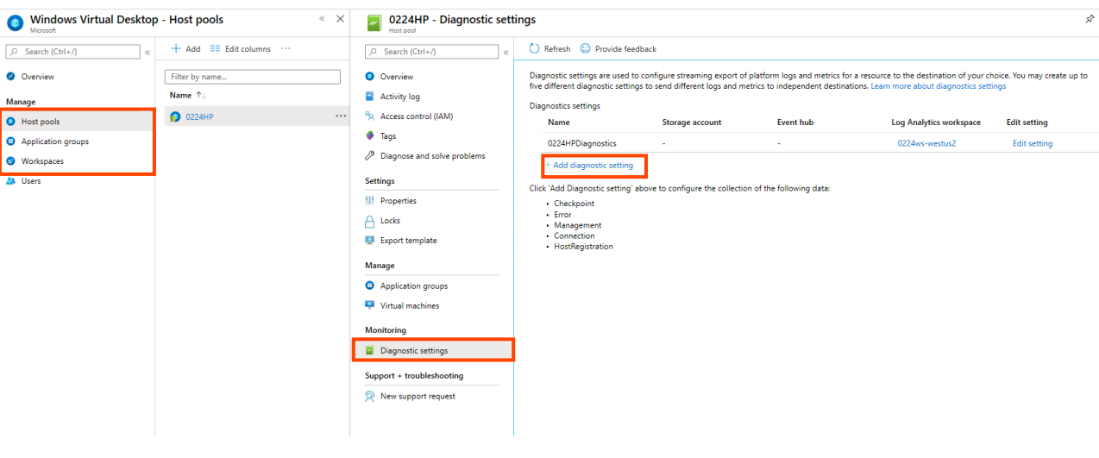
Enable Diagnostics (below Screenshots are samples taken from Microsoft documentation)
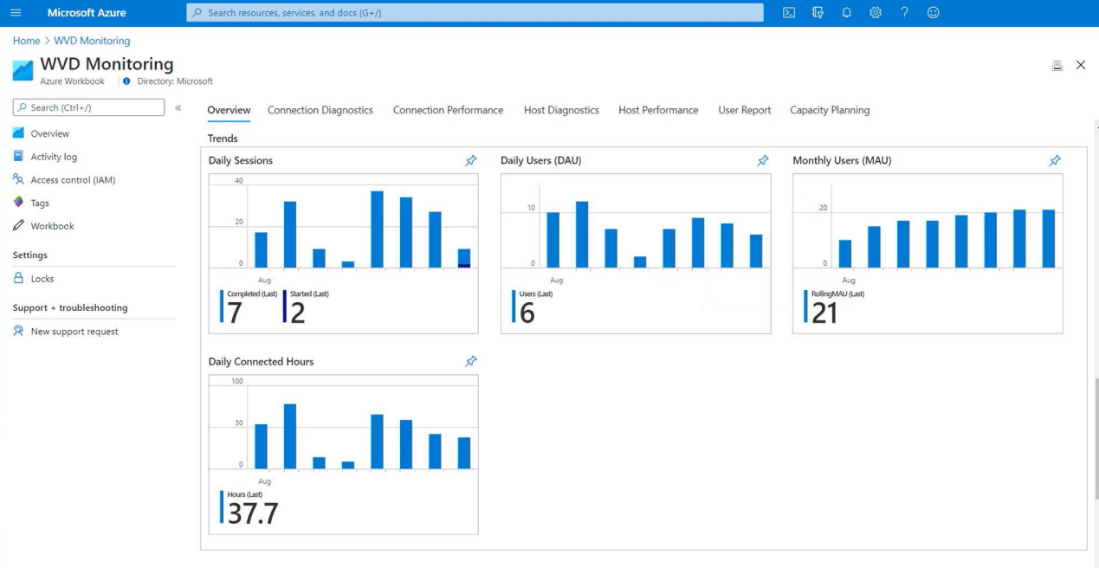
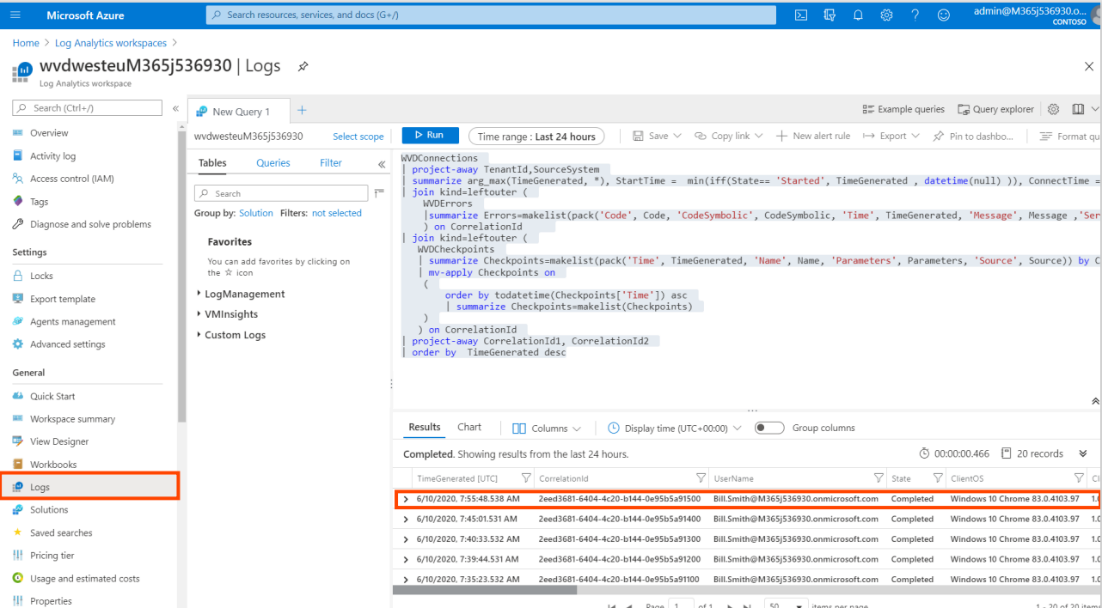
Links for reference:
| Category | Articles |
| Set up diagnostics to monitor agent updates | https://learn.microsoft.com/en-us/azure/virtual-desktop/agent-updates-diagnostics |
| Use Azure Virtual Desktop Insights to monitor your deployment | https://learn.microsoft.com/en-us/azure/virtual-desktop/insights |
| Use Log Analytics for the diagnostics feature | https://learn.microsoft.com/en-us/azure/virtual-desktop/diagnostics-log-analytics |
| Set up service alerts | https://learn.microsoft.com/en-us/azure/virtual-desktop/set-up-service-alerts |
| Resolve Azure Advisor recommendations | https://learn.microsoft.com/en-us/azure/virtual-desktop/azure-advisor-recommendations |
| Collect and query connection quality data | https://learn.microsoft.com/en-us/azure/virtual-desktop/connection-quality-monitoring |
This article discusses about the best practices of Azure Virtual Desktop and I hope you will like this.


