How to minimize Brute Force Attacks by hackers in Azure VM’s
In one of my post in June I have mentioned about the Microsoft Data Center Public IP address ranges and provided the URL to download them. Please note that this IP ranges are also well known to hackers and they are very popular in the hacker’s community. Hacker’s now a days generally uses the Brute force mechanism to attack this IP range. As per the calculations on an average hackers make 5 login attempt per minute to this IP address ranges on RDP and SSH ports and this is going to increase in future as more and more valuable data and information is moving to azure every day.
Picture Credit: FreeClipart.org
There are two ways to minimize or get rid of this attack.
First option is not to use the public IP address for the VM’s and setup all the VM’s in the local area network with private IP address. This is a common scenario which most of the large enterprises are following where they setup the site to site VPN or express route to their on premise data center and Azure and setup a DNS server on premise or azure which assign the private IP address to each VM’s. In this case when a VM is configured for private IP you can see the following thing in place for the public IP address. The public IP address field for this VM is blank.

The network settings of this type of VM will look like this
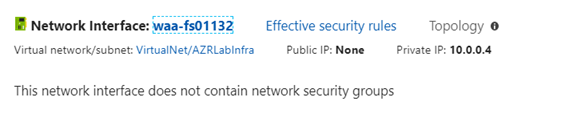
In this scenario best practice is that you should use a jump box which may be a terminal server in your local area network to login to this VM’s, once you login you can also able to ping the VM if ICMP is allowed on the azure VM’s as you can see below.
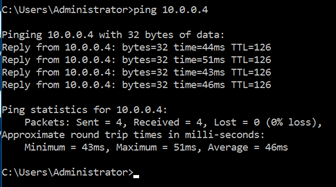
This above approach is very much acceptale for large or medium size organisation which also have multi layer firewall devices to protect their hybrid enviroment. However sometimes we require Azure VM’s which need the public IP address. In this scenario you need to follow the second option which will reduce the risk.
The second option is to reduce exposure to a brute force attack by limiting the amount of time that a port is open. The question is how to achieve this.
As you can see below I have another VM which does contain a Public IP address and is part of a public subnet

The best way to achieve this is to enable the JIT (Just in time access) for the Azure Virtual Machines. Now while I say this I should explain why NSG which is also capable to do this activity is not the right fit here. The main reason is that JITA is a combination of Azure RBAC (Role Based Access Control) and NSG.
What is Just in time access for the Azure VM?
Just in time VM access enables you to lock down your VMs in the network level by blocking inbound traffic to specific ports. It enables you to control the access and reduce the attack surface to your VMs, by allowing access only upon a specific need.
Similar to NSG here also we need to mention the ports on the VM where we need to lock down the inbound traffic. The below image will show what is actually going to happen in case of JITA.
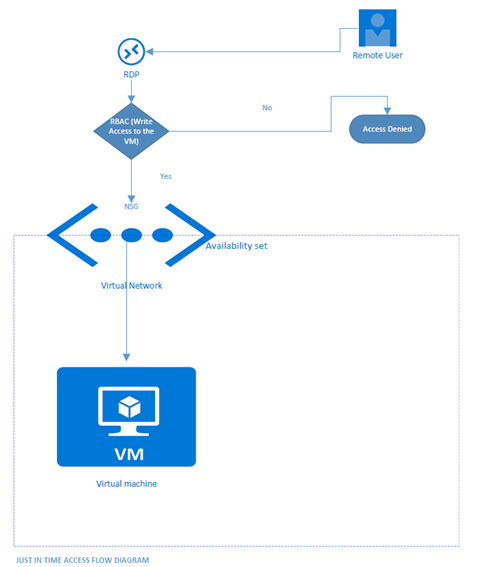
As you can see in the above diagram when a user requests access to a VM, Security Center checks in the RBAC(Role Based Access Control) whether the user has write Access to this VM. If the user have write permissions, the request is approved and Security Center automatically configures the Network Security Groups (NSGs) to allow inbound traffic to the management ports for the amount of time you specified. After the time has expired, Security Center restores the NSGs to their previous states.
JIT is a very good option since Azure network administrator don’t need to go again and again and change the NSG settings however it will incurr additional charges to your Azure subscription as it is the part of the Security Center Standard Pricing Tier. For more information on the Security Center Tier’s please click this URL.
Another thing which you can find here that if you upgrade the secuirty tier to standard it will apply to all the eligible resources in a particular resource group. As you can see below it will charge you USD 15 per Node per Month.
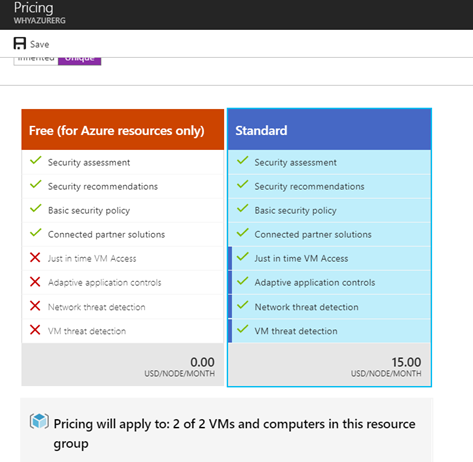
So it’s something you should keep in mind so that you will not be surprised after 90 days’s when you will receive your Azure bill and it will include these charges.
Steps to enable Just in Time Access to this VM
Go to Azure Security Center
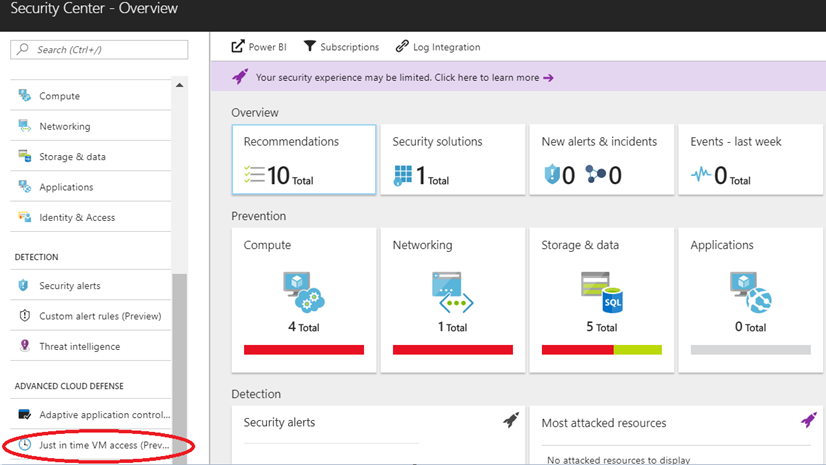
Go down to the JIT tab as you can see below
Go to the recommended tab in the JIT window
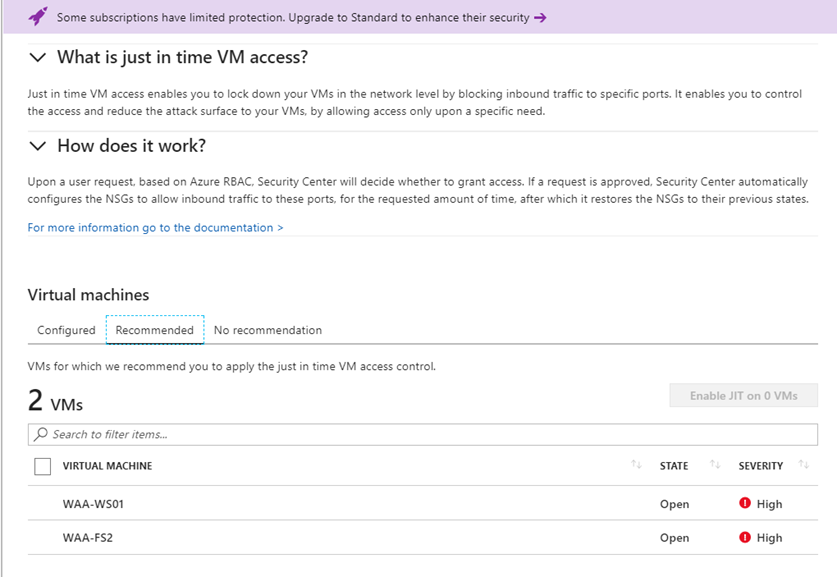
Select the VM where you want to enable JIT
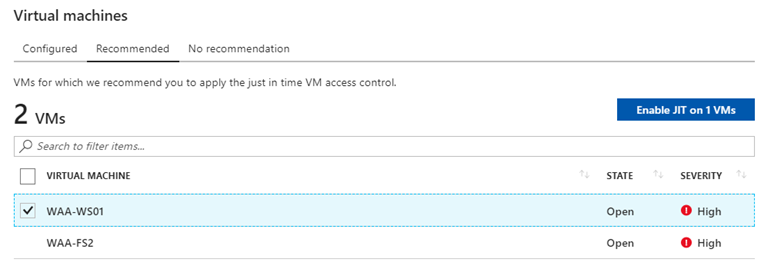
Click on enable JIT on 1 VM
And you can see the default configuration here
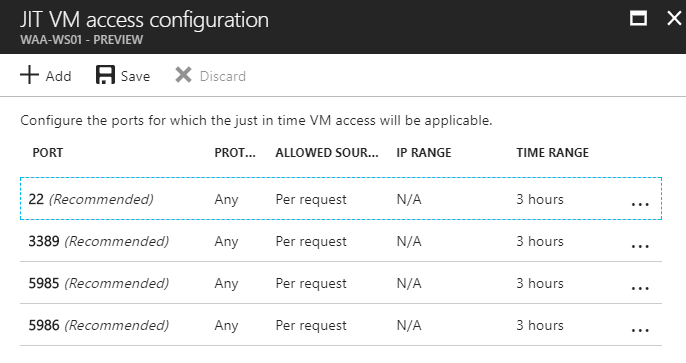
Click on Save and JIT has been activated in this VM.
Now you can click on Request Access Button as shown below.
Here you can find the list of default ports which security center recommend to enable the JIT. I have selected port number 3389 for the RDP.
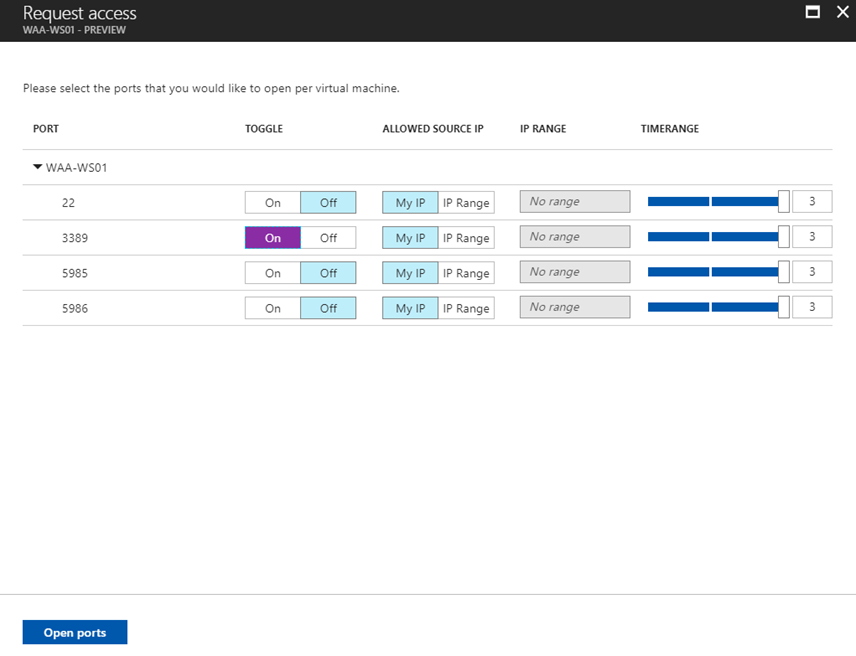
Now MyIP will automatically take the public IP address of your computer as the source IP and allow the RDP access to destination VM which is the Vm where JIT has been configured. Once it’s done you can check the Last User name below where it will show the username which have the access to this VM. For example my account which already have the write access to this VM has been granted RDP permissions in this VM for three hours.
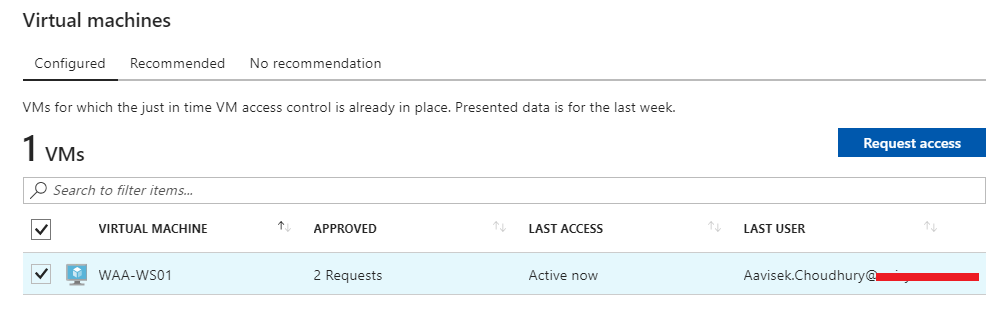
I have tried to RDP to this server and you can see that I can able to login without any problem.
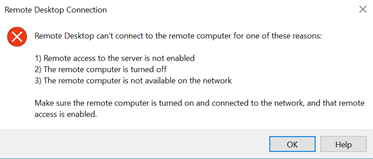
After 3 hours when I have tried again I was unable to RDP and was getting this error
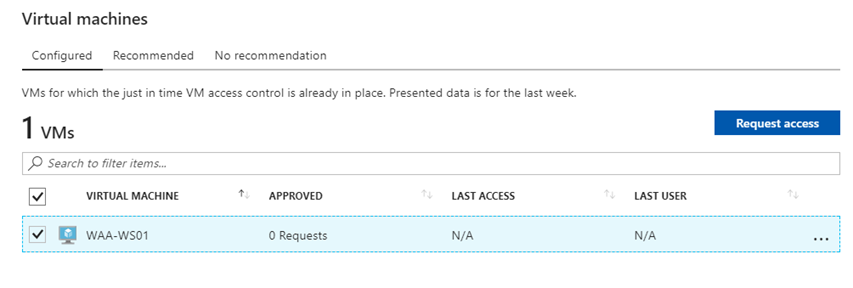
You can also able to edit the JIT policy by clicking on edit option in the configured tab
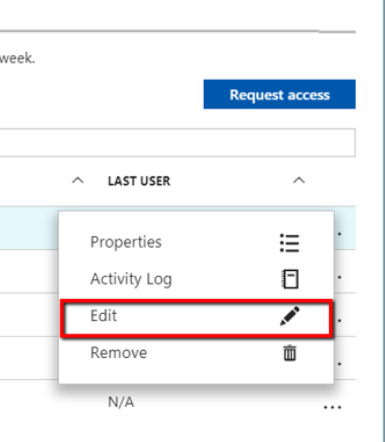
You can also audit the JIT Activity Log by going to the Activity Log Settings as shown below.
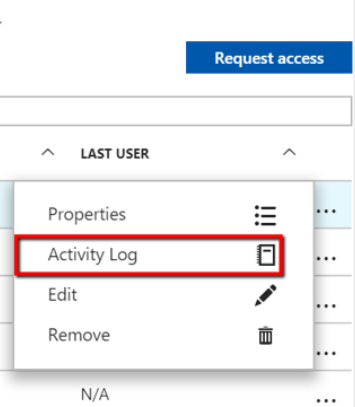
Activity log provides a filtered view of previous operations for that VM along with time, date, and subscription. You can download the log in the CSV format.
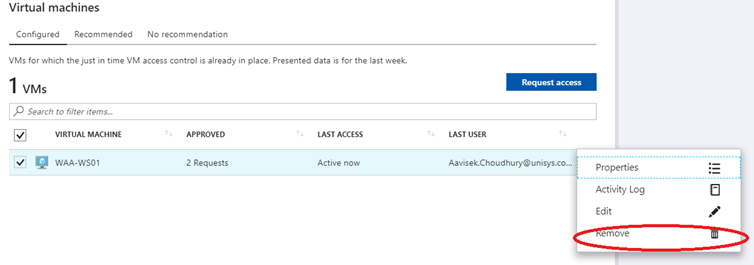
If you wanted to remove the JIT you can remove that by clicking the remove button as shown here.
Conclusion
Private IP address helps you to restrict the Azure VM access only two internal users and just in time VM access in Security Center helps you to control access to your Azure virtual machines when the VM’s are having public IP address and thus minimize the risk associated with Brute Force Attacks. I will bring more posts on Azure VM security on future.
Good luck with your Azure Assignment and enjoy your rest of the day/night.



Very Useful & well explained about it’s implementation. Cheers.
How do I allow others access to this. I have setup JIT, and works for me. I have granted owner role for another user over the VM we’re testing, however nothing appears for him in the Security Center.