How to Configure Session Lock Behavior in Azure Virtual Desktop using Intune or GPO
Configuring session lock behavior in Azure Virtual Desktop (AVD) is critical for organizations to manage and secure remote access effectively. This new feature is released in August 2024. Azure Virtual Desktop provides users with a robust platform to access their virtual machines, while administrators ensure that these environments are secure and compliant with company policies. A primary concern with remote desktops is maintaining security during periods of inactivity or when users step away from their workstations. By configuring session lock behavior, administrators can control what happens when a session becomes idle, reducing the risk of unauthorized access.

This blog explores the nuances of configuring session lock behavior in Azure Virtual Desktop, offering insights into the available options, steps to configure session behavior, the importance of this feature in a security framework, and best practices for its implementation.
Why Session Lock Behavior Matters in Azure Virtual Desktop
Azure Virtual Desktop, as a cloud-based solution, allows users to access their virtual machines from anywhere with an internet connection. This flexibility has driven adoption in organizations looking to enable remote work. However, this flexibility also introduces new security challenges, particularly when it comes to securing remote sessions.
When a user leaves their virtual desktop session unattended or idle, the session remains open and potentially vulnerable to unauthorized access. Configuring session lock behavior ensures that these idle sessions are either locked or disconnected after a specified period of inactivity, safeguarding sensitive data and company resources.
Additionally, configuring session lock behavior enforces security policies such as multifactor authentication (MFA), ensuring that users must reauthenticate after a session lock, further protecting against unauthorized access.
Available Session Lock Options in Azure Virtual Desktop
Azure Virtual Desktop provides administrators with two primary options for managing session lock behavior:
1. Disconnect Session on Idle (Application to Single sign-on using Microsoft Entra ID): This option disconnects the user’s session after a defined period of inactivity. The session remains active on the server, but the user must reconnect to continue working. This option is ideal for users who frequently step away from their desks for short periods, as it keeps their session running without losing their progress.
2. Remote Lock Screen (Applicable to Legacy authentication protocols): In this configuration, the session locks and displays a remote lock screen, similar to what happens when a local machine is locked. The user must re-enter their credentials (or use SSO and MFA) to regain access. This option is useful for environments where user sessions must be tightly controlled to meet compliance requirements.
Configuring Session Lock Behavior
The configuration of session lock behavior in Azure Virtual Desktop can be done through two primary methods: Microsoft Intune and Group Policy. Both methods offer flexibility depending on the organization’s management tools and policies.
Using Microsoft Intune
Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM). It allows organizations to manage user devices and applications, ensuring security and compliance across the board.
Before configuring the session lock behavior, ensure you meet the following prerequisites:
Host Pool Requirements:
An existing host pool with session hosts.
Session Host Operating Systems:
Your session hosts must be running one of the following operating systems, with the specified cumulative update installed:
Windows 11 (single or multi-session):2024-05 Cumulative Updates for Windows 11 (KB5037770) or later.
Windows 10 (single or multi-session, versions 21H2 or later):2024-06 Cumulative Updates for Windows 10 (KB5039211) or later.
Windows Server 2022:2024-05 Cumulative Update for Microsoft Server OS (KB5037782) or later.
Intune Configuration Requirements:
A Microsoft Entra ID account assigned to the Policy and Profile Manager built-in RBAC role.
A group containing the devices you intend to configure.
To configure session lock behavior using Intune:
1. Create a Custom Configuration Profile: Intune allows administrators to create custom profiles for Azure Virtual Desktop sessions, which can be applied to users or groups. These profiles control the session lock settings.
2. Assign the Profile to Users or Devices: Once the configuration profile is created, it can be assigned to the relevant users or devices within the organization. This ensures that the session lock settings are enforced based on the organization’s security policies.
3. Test and Monitor: After applying the settings, it’s crucial to test the configuration to ensure it functions as expected. Administrators can also monitor the session behavior using Intune’s built-in reporting tools.
A detail Step by step guide to apply the policy:
Sign in to the Microsoft Intune admin center.
Create or edit a configuration profile for Windows 10 and later devices, with the Settings catalog profile type.
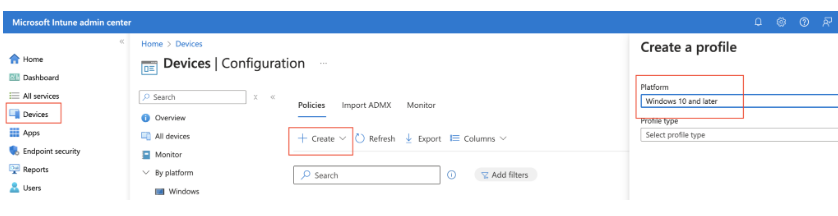
In the settings picker, browse to Administrative templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security.
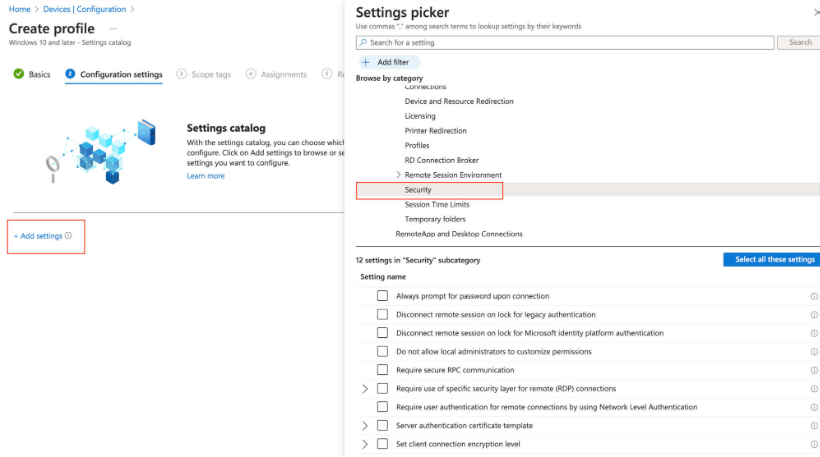
Check the box for one of the following settings, depending on your requirements:
For single sign-on using Microsoft Entra ID:
-
- Check the box for Disconnect remote session on lock for Microsoft identity platform authentication, then close the settings picker.
- Expand the Administrative templates category, then toggle the switch for Disconnect remote session on lock for Microsoft identity platform authentication to Enabled or Disabled:
- To disconnect the remote session when the session locks, toggle the switch to Enabled, then select OK.
- To show the remote lock screen when the session locks, toggle the switch to Disabled, then select OK.
You can review and apply the policy. Don’t forget to restart the session hosts once the policy is applied.

For legacy authentication protocols:
-
-
- Check the box for Disconnect remote session on lock for legacy authentication, then close the settings picker.
- Expand the Administrative templates category, then toggle the switch for Disconnect remote session on lock for legacy authentication to Enabled or Disabled:
- To disconnect the remote session when the session locks, toggle the switch to Enabled, then select OK.
- To show the remote lock screen when the session locks, toggle the switch to Disabled, then select OK.
-
- Select Next.
- Optional: On the Scope tags tab, select a scope tag to filter the profile. For more information about scope tags, see Use role-based access control (RBAC) and scope tags for distributed IT.
- On the Assignments tab, select the group containing the computers providing a remote session you want to configure, then select Next.
- On the Review + create tab, review the settings, then select Create.
- Once the policy applies to the session hosts, restart them for the settings to take effect.
- To test the configuration, connect to a remote session, then lock the remote session. Verify that the session either disconnects or the remote lock screen is shown, depending on your configuration.
Using Group Policy
For organizations using on-premises Active Directory or hybrid environments, Group Policy remains a popular method for managing security settings. Configuring session lock behavior via Group Policy involves the following steps:
1. Access Group Policy Management: Administrators can access the Group Policy Management Console (GPMC) to create or modify policies related to Azure Virtual Desktop.
2. Navigate to Session Lock Settings: Within the GPMC, administrators can navigate to the specific policy settings that control session lock behavior. These settings allow for the configuration of idle time before disconnecting the session or displaying the remote lock screen.
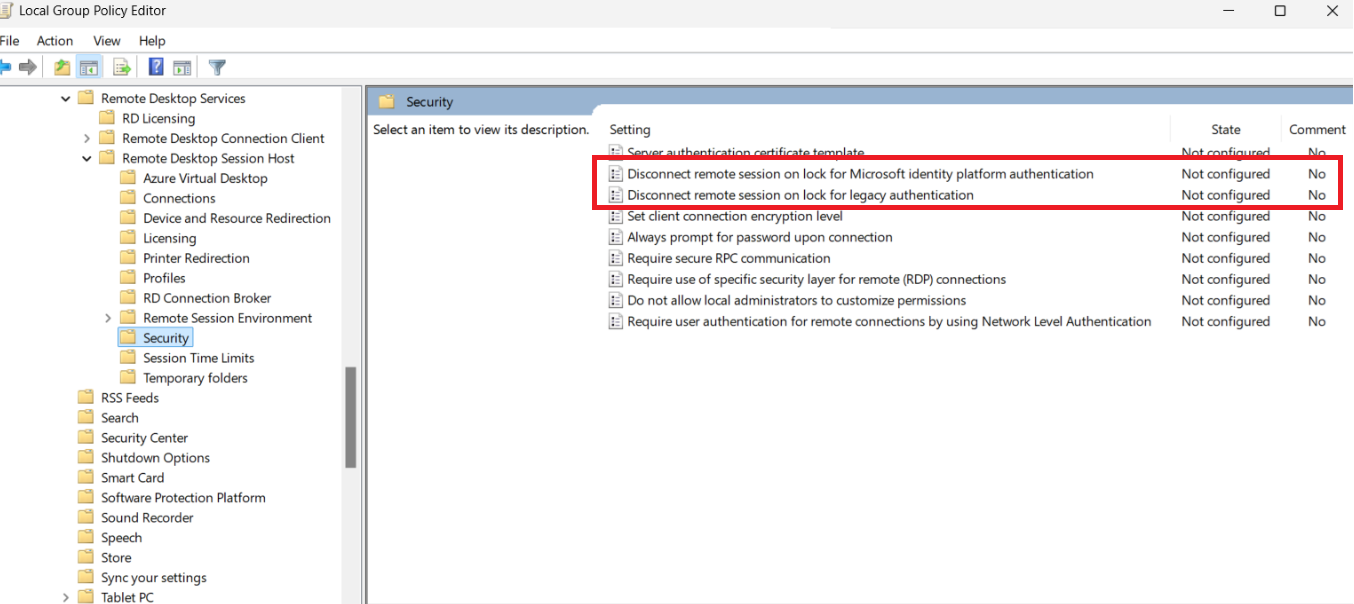
3. Apply the Policy: Once the policy is configured, it can be applied to specific user groups or organizational units (OUs), ensuring that the settings are enforced across the desired users or systems.
4. Monitor and Adjust: Like Intune, it’s important to monitor the policy’s effectiveness and adjust the settings if necessary based on user feedback or security requirements.
Enhancing Security with Single Sign-On (SSO) and Multifactor Authentication (MFA)
In conjunction with session lock behavior, Azure Virtual Desktop supports Single Sign-On (SSO) using Microsoft Entra ID (formerly known as Azure Active Directory). SSO enables seamless authentication for users, allowing them to reconnect to their sessions without repeatedly entering credentials. This reduces friction for users while maintaining strong security standards.
Moreover, Azure Virtual Desktop integrates with Multifactor Authentication (MFA), adding an additional layer of security. With MFA, users must provide two or more verification factors to gain access to their sessions after a lock or disconnection, ensuring that even if credentials are compromised, unauthorized access is prevented.
Benefits of Configuring Session Lock Behavior
Implementing session lock behavior in Azure Virtual Desktop brings several benefits to organizations, including:
Improved Security: By locking or disconnecting sessions after a period of inactivity, organizations reduce the risk of unauthorized access, protecting sensitive data and resources.
Compliance with Security Standards: Many industries, such as healthcare and finance, require strict adherence to security standards like HIPAA and PCI-DSS. Configuring session lock behavior helps meet these compliance requirements by enforcing session security policies.
User Convenience: With options like SSO and MFA, users can quickly regain access to their sessions without compromising security, improving their overall experience.
Reduced Risk of Data Breaches: Unattended sessions are a prime target for attackers. By enforcing session lock behavior, organizations mitigate the risk of data breaches resulting from unattended sessions.
Best Practices for Implementing Session Lock Behavior
To ensure that the configuration of session lock behavior in Azure Virtual Desktop is both effective and user-friendly, administrators should follow these best practices:
1. Tailor Settings to User Needs: Different users may have different needs. For example, customer support teams may require longer session timeouts, while finance teams may need stricter session locks due to the sensitive nature of their work.
2. Balance Security and Usability: While session locks enhance security, they can also disrupt workflows. Striking a balance between security and usability is crucial to ensure that users remain productive while the organization stays secure.
3. Use SSO and MFA for Seamless Security: Combining SSO and MFA with session lock behavior provides a seamless yet secure experience for users. Administrators should encourage the use of these features to enhance overall security.
4. Regularly Review and Adjust Policies: As organizational needs change, so too should the policies governing session lock behavior. Regular reviews ensure that the configuration remains relevant and effective in safeguarding the environment.
Final Thought
Configuring session lock behavior in Azure Virtual Desktop is essential for ensuring that remote work environments remain secure and compliant with organizational policies. Whether through Intune or Group Policy, administrators have flexible options for controlling session lock settings. By combining session lock behavior with advanced security features like SSO and MFA, organizations can protect sensitive data while delivering a seamless experience to users.