Step by Step Configure SSO (Single Sign-On) for Azure Virtual Desktop with ADFS from Scratch in a PoC environment Part 2
Hello All, welcome back, this post is a continuation of my last post where I have mentioned the first 8 steps which you should configure to test the SSO for AVD with ADFS.
- Purchase a domain from Azure
- Add the domain to Microsoft 365 Portal
- Buy a certificate from Azure Service Certificates for the ADFS
- Add the ADFS Server role
- Configure the first federation server in a new federation server farm
- Configure Azure AD Connect for TLS 1.2
- Install Azure AD Connect
- Configure Azure AD connect for ADFS
Now, I am going to show you the next 9 steps of the SSO configuration.
- Install & Configure On-Premises Certificate Authority Server
- Create the enrollment agent certificate template
- Create the Smartcard Logon certificate template
- Enable the newly created certificate template
- Configure the AD FS Servers to use the new certificate template
- Create a Key Vault in Azure and Set the Access Policy for WVD Application
- Configure your Azure Virtual Desktop host pool
Due to very long details, I have divided the blog into 2 Parts. This is the first part of the Blog.
Step 9: Install & Configure On-Premises Certificate Authority Server
Now I need to install Active Directory Certificate Services (AD CS) in my forest.
Log on as a member of both the Enterprise Admins group and the root domain’s Domain Admins group.
In Server Manager, click Manage, and then click Add Roles and Features. The Add Roles and Features Wizard opens.
In Before You Begin, click Next.
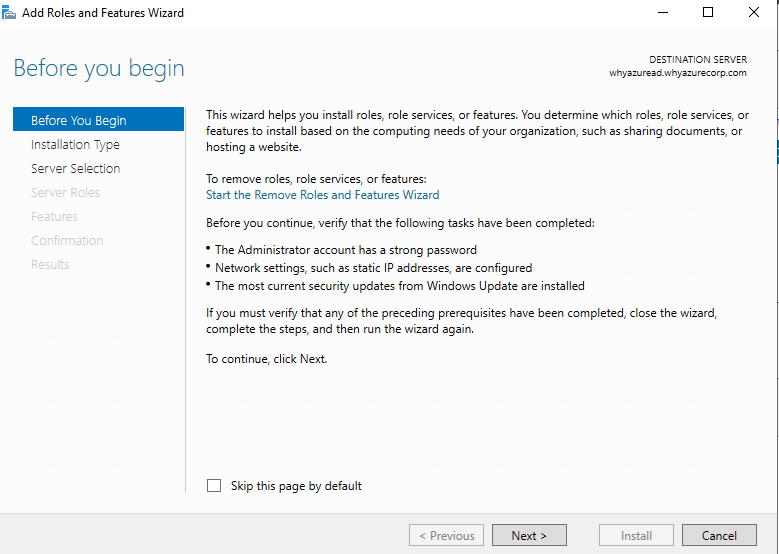
In Select Installation Type, ensure that Role-Based or feature-based installation is selected, and then click Next.
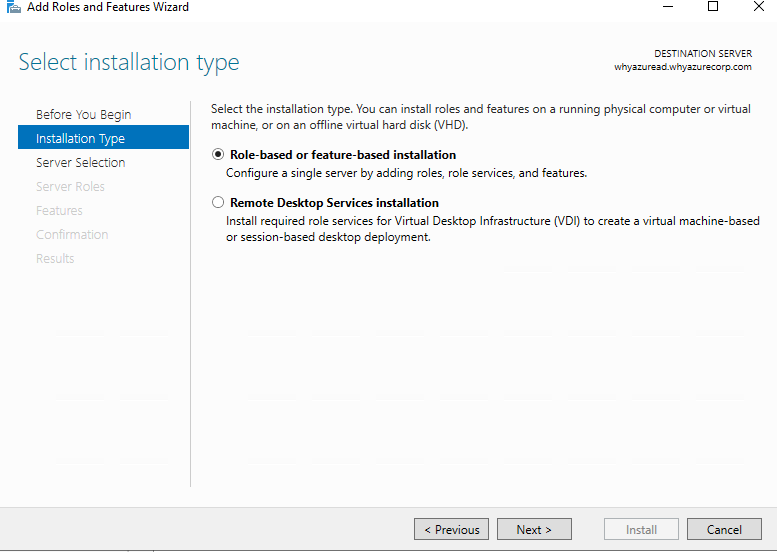
In Select destination server, ensure that Select a server from the server pool is selected. In Server Pool, ensure that the local computer is selected. Click Next.
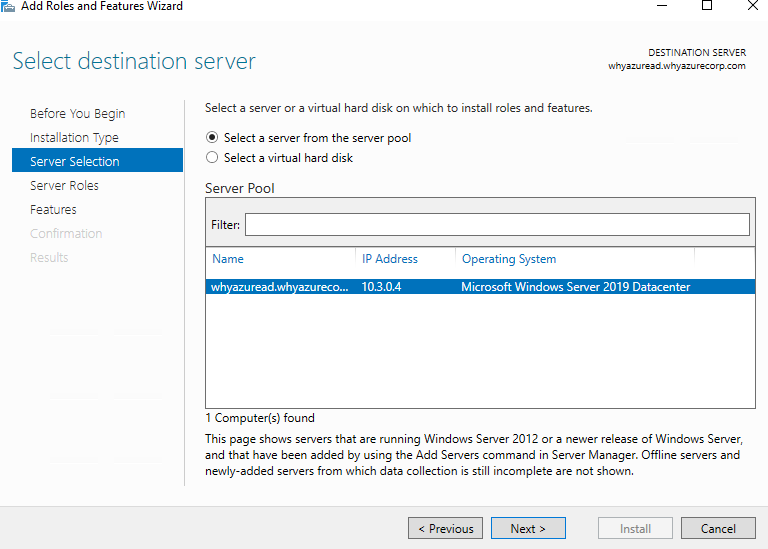
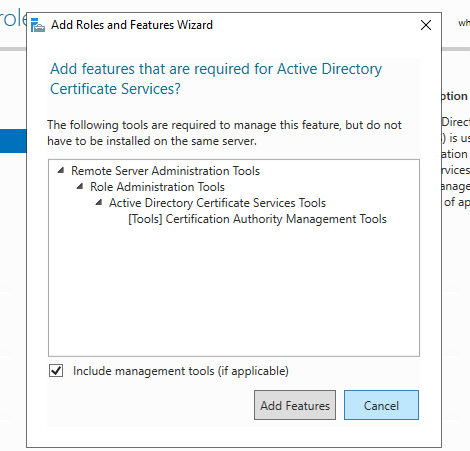
In Select Server Roles, in Roles, select Active Directory Certificate Services. When you are prompted to add required features, click Add Features, and then click Next.
In Select features, click Next.
In Active Directory Certificate Services, read the provided information, and then click Next.
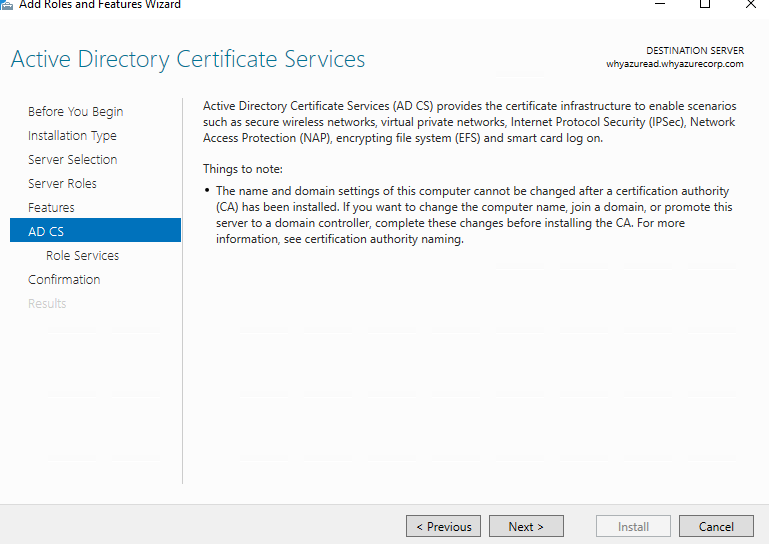
Select Certificate Authority Web Enrollment also
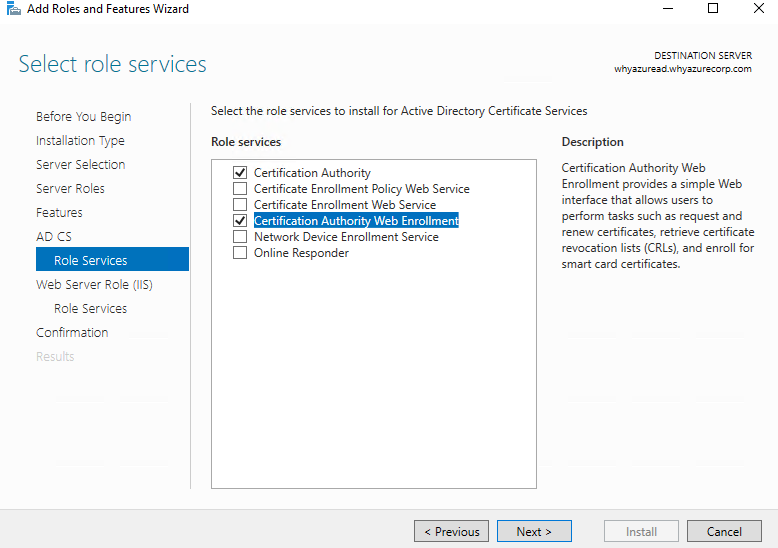
Add the IIS server role which is required for this
Select the below role services for IIS installation.
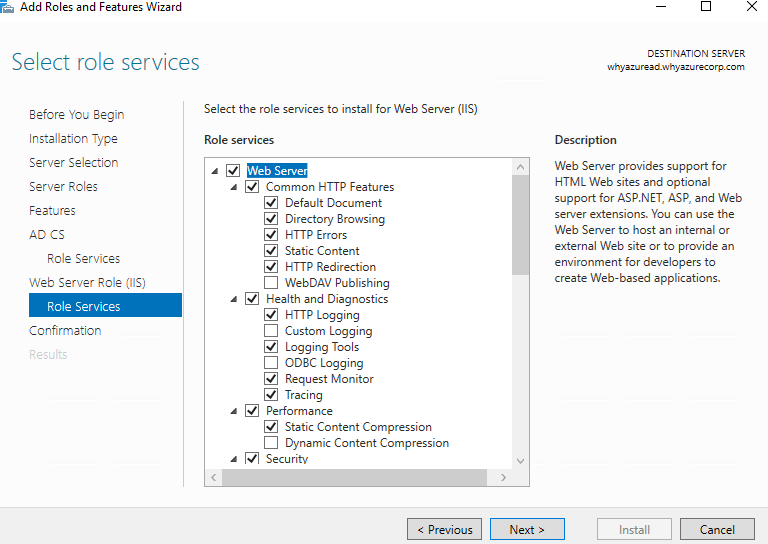
In Confirm installation selections, click Install. Do not close the wizard during the installation process.
Check the installation progress status
After sometime the installation will be completed as you can see below
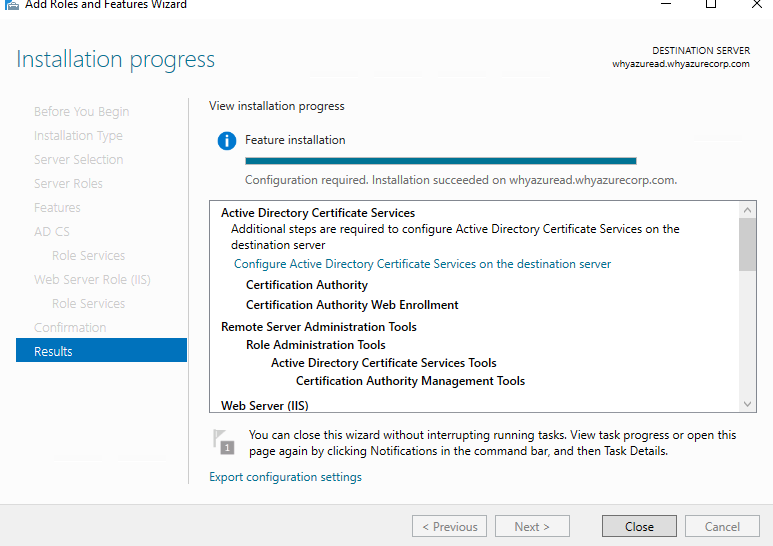
When installation is complete, click Configure Active Directory Certificate Services on the destination server. The AD CS Configuration wizard opens. Read the credentials information and, if needed, provide the credentials for an account that is a member of the Enterprise Admins group. Click Next.
In Role Services, click Certification Authority, and then click Next.
On the Setup Type page, verify that Enterprise CA is selected, and then click Next.
On the Specify the type of the CA page, verify that Root CA is selected, and then click Next.
On the Specify the type of the private key page, verify that Create a new private key is selected, and then click Next.
On the Cryptography for CA page, keep the default settings for CSP (RSA#Microsoft Software Key Storage Provider) and hash algorithm (SHA2), and determine the best key character length for your deployment. Large key character lengths provide optimal security; however, they can impact server performance and might not be compatible with legacy applications. It is recommended that you keep the default setting of 2048. Click Next.
On the CA Name page, keep the suggested common name for the CA or change the name according to your requirements. Ensure that you are certain the CA name is compatible with your naming conventions and purposes, because you cannot change the CA name after you have installed AD CS. Click Next.
On the Validity Period page, in Specify the validity period, type the number and select a time value (Years, Months, Weeks, or Days). The default setting of five years is recommended. Click Next.
On the CA Database page, in Specify the database locations, specify the folder location for the certificate database and the certificate database log. If you specify locations other than the default locations, ensure that the folders are secured with access control lists (ACLs) that prevent unauthorized users or computers from accessing the CA database and log files. Click Next.
In Confirmation, click Configure to apply your selections, and then click Close.
Once the configuration is done it will show the below screen.
Now, You must properly create the following certificate templates so that AD FS can use SSO:
First, you’ll need to create the Exchange Enrollment Agent (Offline Request) certificate template. AD FS uses the Exchange Enrollment Agent certificate template to request certificates on the user’s behalf.
You’ll also need to create the Smartcard Logon certificate template, which AD FS will use to create the sign in certificate.
After you create these certificate templates, you’ll need to enable the templates on the certificate authority so AD FS can request them.
Step 10: Create the enrollment agent certificate template
On the certificate authority, run mmc.exe from the Start menu to launch the Microsoft Management Console, Select File… > Add/Remote Snap-in… > Certificate Templates > Add > > OK to view the list of certificate templates.
Expand the Certificate Templates
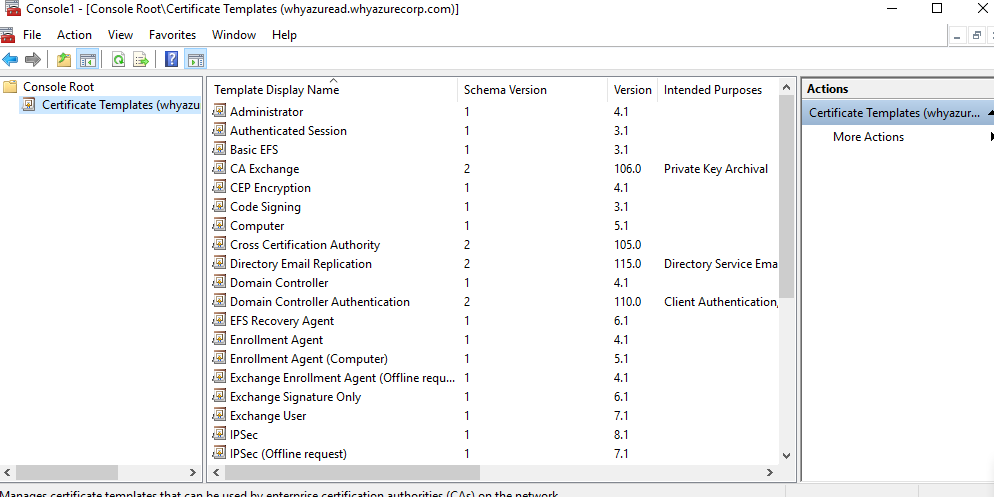
Right-click Exchange Enrollment Agent (Offline Request) and select Duplicate Template.
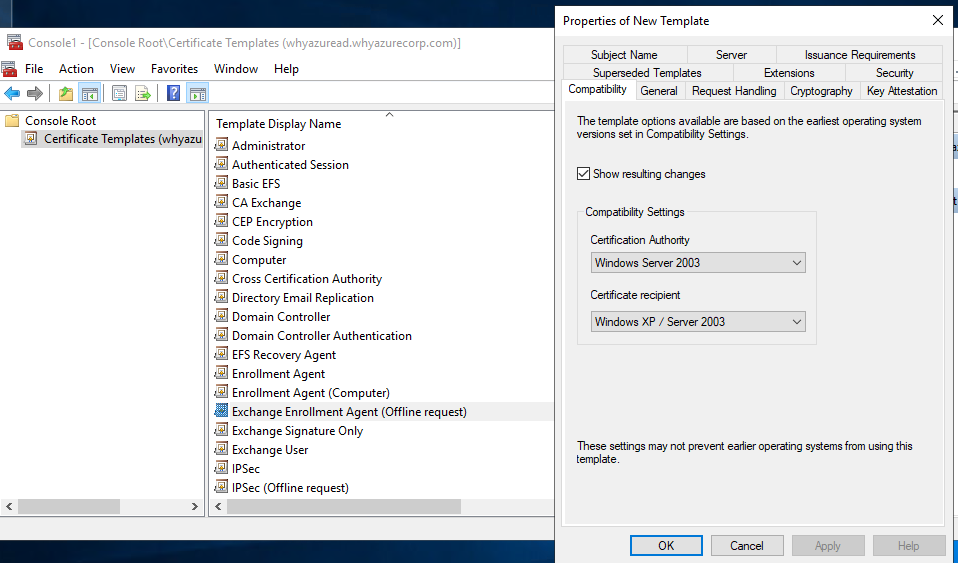
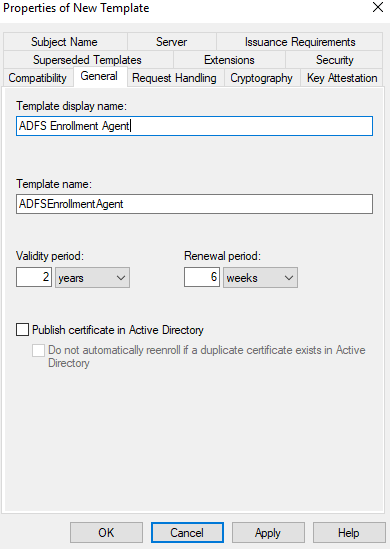
Select the General tab, then enter “ADFS Enrollment Agent” into the Template display name field. This will automatically set the template name to “ADFSEnrollmentAgent”.
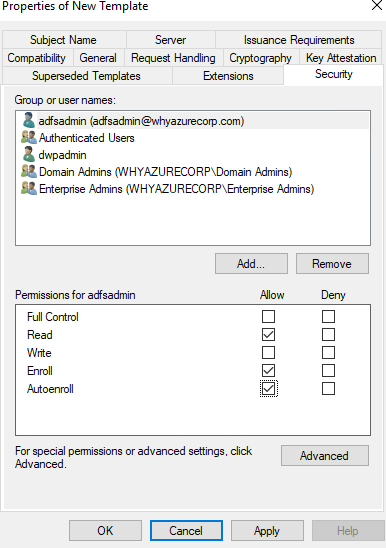
Select the Security tab, then select Add…. Next, select Object Types…, then Service Accounts, and then OK.
Enter the service account name for AD FS just like you did in the Create the enrollment agent certificate template section.
After the service account is added and is visible in the Security tab, select it in the Group or user names pane, select Allow for both “Enroll” and “Autoenroll”, then select OK to save.
Step 11: Create the Smartcard Logon certificate template
On the certificate authority, run mmc.exe from the Start menu to launch the Microsoft Management Console.
Select File… > Add/Remote Snap-in… > Certificate Templates > Add > OK to view the list of certificate templates.
Expand the Certificate Templates, right-click Smartcard Logon and select Duplicate Template.
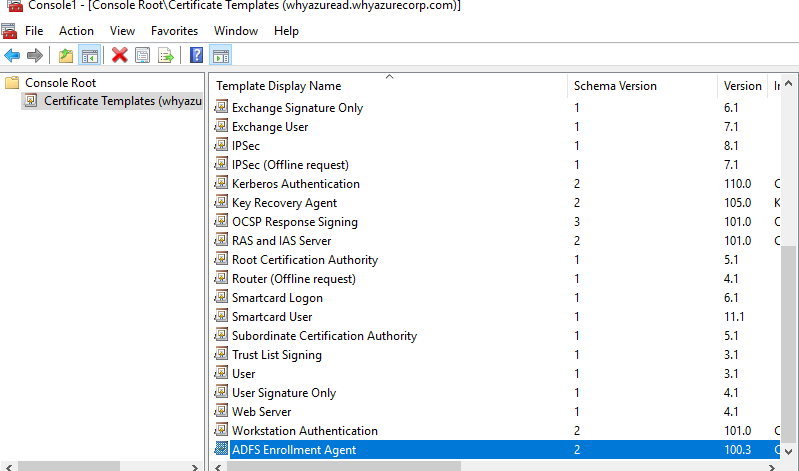
Select the General tab, then enter “ADFS SSO” into the Template display name field.
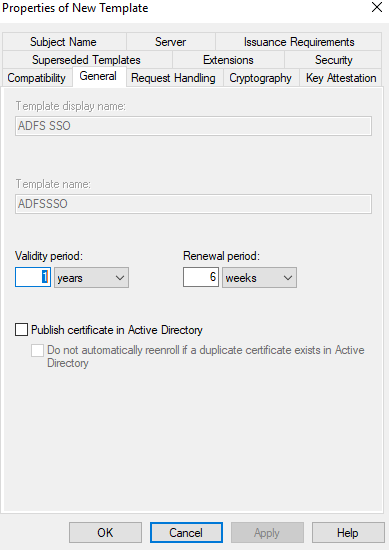
This will automatically set the template name to “ADFSSSO”.
For Application policy, select Certificate Request Agent.
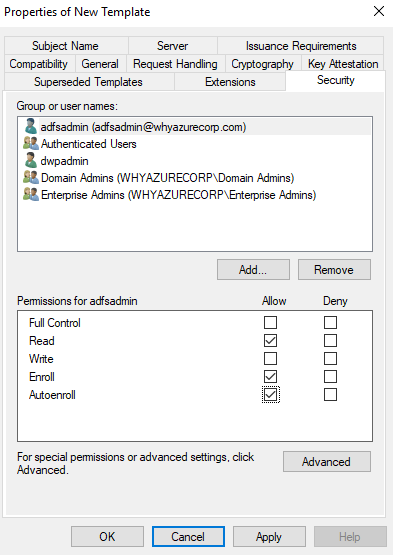
Select the Security tab, then select Add….
Select Object Types…, Service Accounts, and OK.
After the service account is added and is visible in the Security tab, select it in the Group or user names pane, select Allow for both “Enroll” and “Autoenroll”, then select OK to save.
Select the Subject name tab and then select Supply in the request. When you see a warning message, select OK.
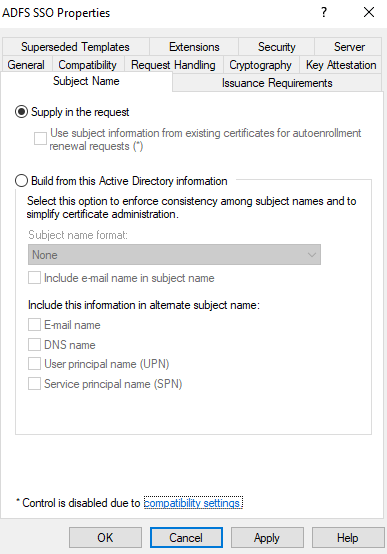
Issuance Requirements check this number of authorized signatures
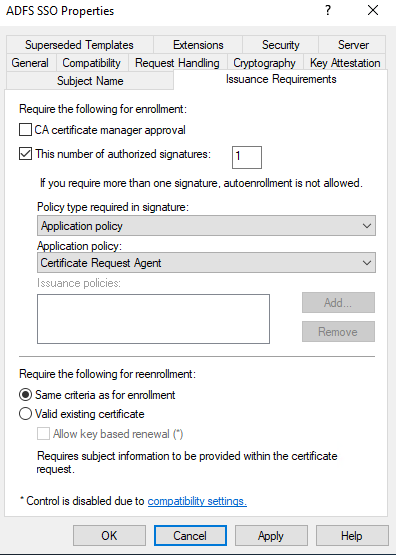
Step 12: Enable the new certificate template
On the certificate authority, run mmc.exe from the Start menu to launch the Microsoft Management Console.
Select File… > Add/Remove Snap-in… > Certification Authority > Add > > Finish > and OK to view the Certification Authority.
Expand the Certification Authority on the left-hand pane and open Certificate Templates.
Right-click in the middle pane that shows the list of certificate templates, select New, then select Certificate Template to Issue.
Select both ADFS Enrollment Agent and ADFS SSO, then select OK. You should see both templates in the middle pane.
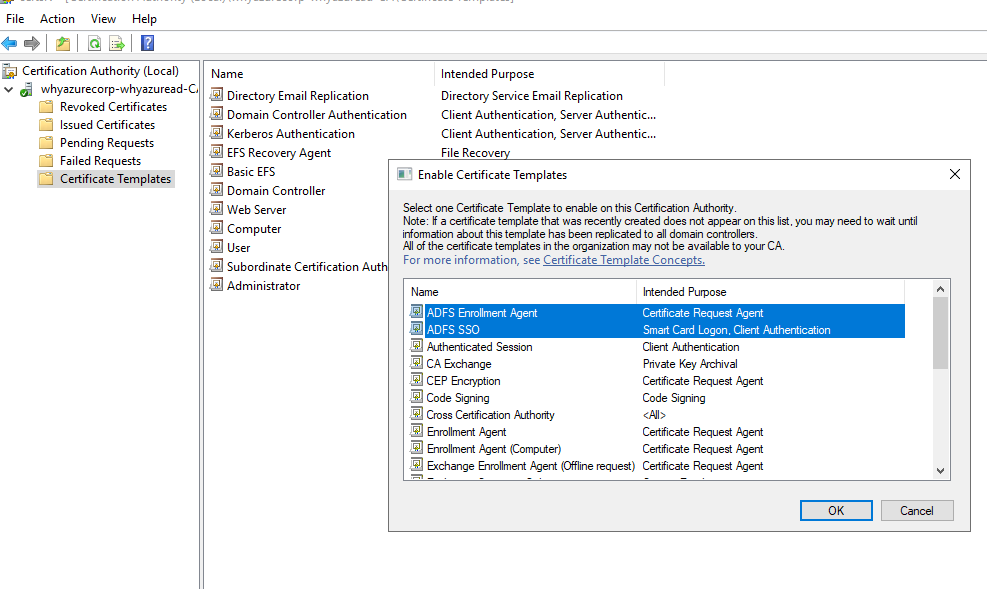
Step 13: Configure the AD FS Servers to use the new certificate template
You must configure the Active Directory Federation Services (AD FS) servers to use the new certificate templates and set the relying-party trust to support SSO.
The relying-party trust between your AD FS server and the Azure Virtual Desktop service allows single sign-on certificate requests to be forwarded correctly to your domain environment.
When configuring AD FS single sign-on you must choose shared key or certificate:
If you have a single AD FS server, you can choose shared key or certificate.
The shared key or certificate used to generate the token to sign in to Windows must be stored securely in Azure Key Vault.
On the AD FS VMs, import the ADFS module.
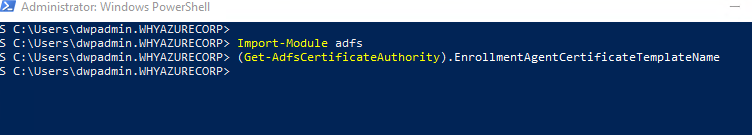
On the AD FS VMs, run the following PowerShell cmdlet to configure AD FS to use the certificate templates from the previous section:
Set-AdfsCertificateAuthority -EnrollmentAgentCertificateTemplate “ADFSEnrollmentAgent” -LogonCertificateTemplate “ADFSSSO” -EnrollmentAgent
![]()
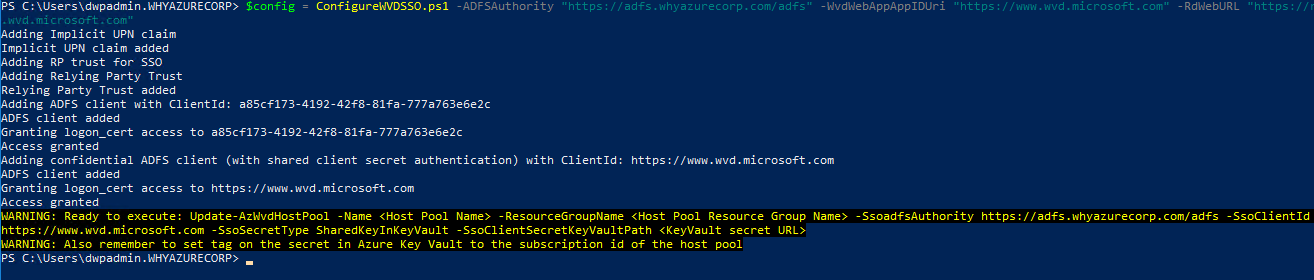
Run the ConfigureWVDSSO.ps1 script. The PowerShell script ConfigureWVDSSO.ps1 available in the PowerShell Gallery will configure your AD FS server for the relying-party trust and install the certificate if needed.
Install-Script -Name ConfigureWVDSSO

$config = ConfigureWVDSSO.ps1 -ADFSAuthority “https://adfs.whyazurecorp.com/adfs” -WvdWebAppAppIDUri “https://www.wvd.microsoft.com” -RdWebURL https://rdweb.wvd.microsoft.com
Step 14: Create a Key vault in Azure and Set the Access Policy for AVD Application
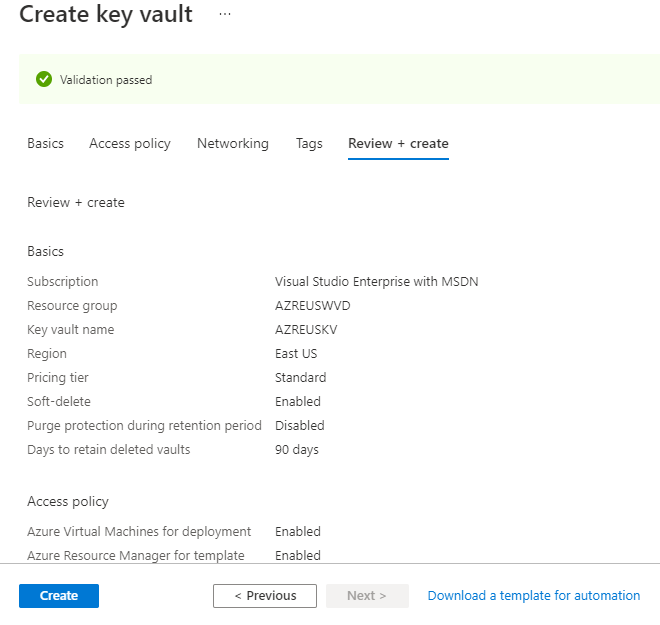
Set the access policy on the Azure Key Vault by running the following PowerShell cmdlet:
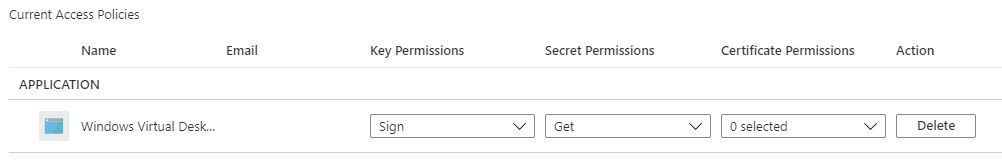
Set-AzKeyVaultAccessPolicy -VaultName “AZREUSKV” -ServicePrincipalName 9cdead84-a844-4324-93f2-XXXXXXXXX -PermissionsToSecrets get -PermissionsToKeys sign
Application ID: 9cdead84-a844-4324-93f2-b2e6bb768d07 (Windows Virtual Desktop)
![]()
You need to enable Azure AD Premium
The below screen shot shows the Application of Windows Virtual Desktop
Step 15: Configure your Azure Virtual Desktop host pool
It’s time to configure the AD FS SSO parameters on your Azure Virtual Desktop host pool. To do this, set up your PowerShell environment for Azure Virtual Desktop if you haven’t already and connect to your account.
After that, update the SSO information for your host pool by running one of the following two cmdlets in the same PowerShell window on the AD FS VM:
$config = ConfigureWVDSSO.ps1 -ADFSAuthority “https://adfs.whyazurecorp.com/adfs” -WvdWebAppAppIDUri “https://www.wvd.microsoft.com” -RdWebURL “https://rdweb.wvd.microsoft.com”
$hp = Get-AzWvdHostPool -Name “AZREUSPOOL” -ResourceGroupName “AZREUSWVD”
If you’re using a certificate in the Key Vault, run the following PowerShell cmdlet:
$secret = Set-AzKeyVaultSecret -VaultName “AZREUSKV” -Name “adfsssosecret” -SecretValue (ConvertTo-SecureString -String $config.SSOClientSecret -AsPlainText -Force) -Tag @{ ‘AllowedWVDSubscriptions’ = $hp.Id.Split(‘/’)[2]}
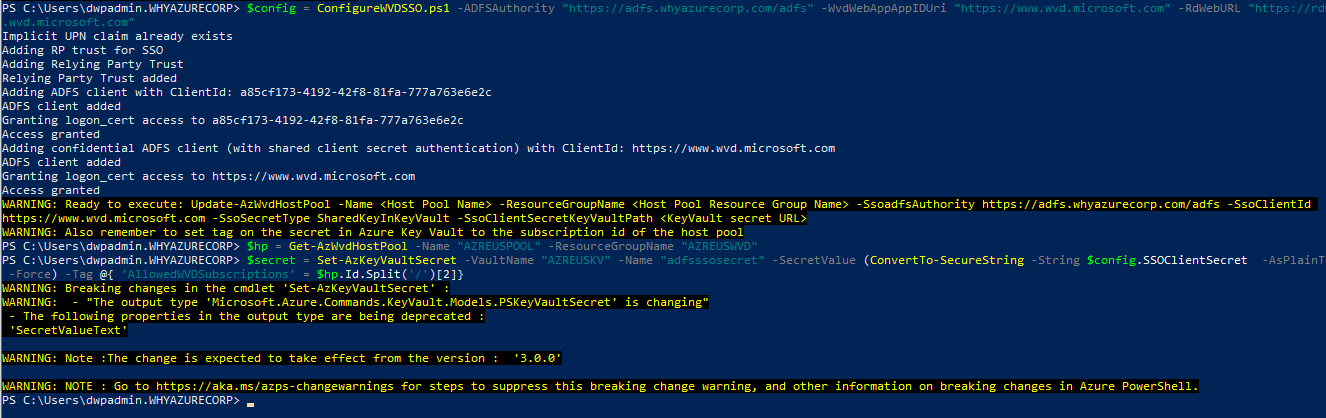
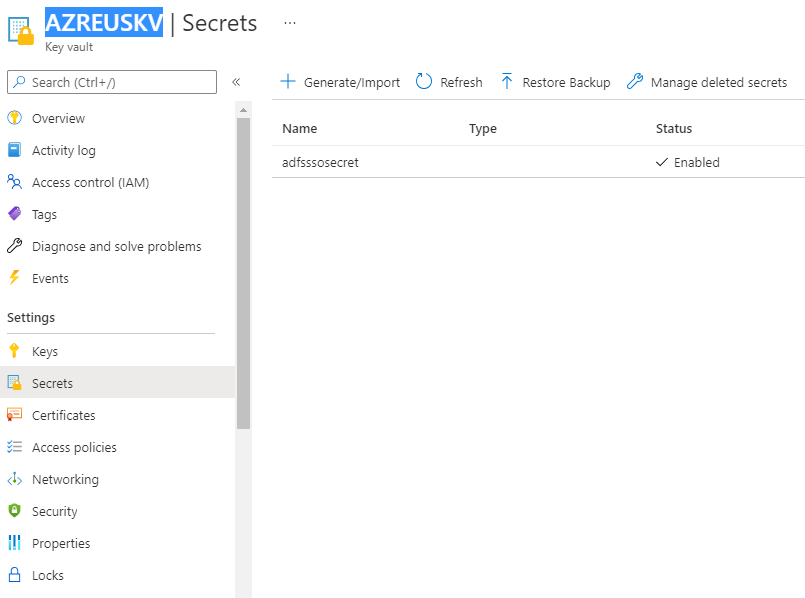
Update-AzWvdHostPool -Name “AZREUSPOOL” -ResourceGroupName “AZREUSWVD” -SsoadfsAuthority “https://adfs.whyazurecorp.com/adfs” -SsoClientId “https://www.wvd.microsoft.com” -SsoSecretType SharedKeyInKeyVault -SsoClientSecretKeyVaultPath $secret.Id
That’s all you are all set for ADFS SSO for AVD, I hope you have like this very detailed post which has total of 15 sections and covers everything from scratch about the configuration, I will bring more posts on AVD very soon, stay tuned and you have a great day ahead.


