Step by Step Configure SSO (Single Sign-On) for Azure Virtual Desktop with ADFS from Scratch in a PoC environment part 1
One of my blogpost on SSO for O365 with ADFS which I have published in Sept. 6th 2017, is one of the most read post on ADFS and has received the views of 47216 till date, one of my close friend who is following my blog from 2017, and who is also the owner of the Azure Development Telegram Group (Please check the community section of this blog if you want to join that community) which has crossed 17k+ members recently, has requested me to write a post about the configuration of the Azure Virtual Desktop with ADFS. You may ask why a new post when already many posts are available in the internet about this topic, the reason behind that is although there are many posts available but none of the posts describe this process from scratch as per my understanding to deploy the SSO for AVD with ADFS you need at least 15 steps and all of them I have covered in this post.
Also at present, if you are planning for SSO for your Azure Virtual Desktop ADFS is the only option available since the SSO with Azure AD is yet to release. The people who are from the Citrix Community are already aware of the same SSO functionality for the Citrix VDI, which we can achieve with the help of the Citrix FAS server.
To deploy the ADFS SSO for the Azure Virtual Desktop, let’s see the prerequisite.
- Public registered DNS name for the domain
- Active directory certificate service
- Active Directory federation service
- Azure AD connect
- PowerShell with AVD modules
- Public SSL certificate
- An AVD host pool
- Azure key vault
To meet the above prerequisites we must have the following things deployed in a step-by-step manner. In my lab, I have performed the following steps to deploy the SSO with ADFS.
- Purchase a domain from Azure
- Add the domain to Microsoft 365 Portal
- Buy a certificate from Azure Service Certificates for the ADFS
- Add the ADFS Server role
- Configure the first federation server in a new federation server farm
- Configure Azure AD Connect for TLS 1.2
- Install Azure AD Connect
- Configure Azure AD connect for ADFS
- Install & Configure On-Premises Certificate Authority Server
- Create the enrollment agent certificate template
- Create the Smartcard Logon certificate template
- Enable the newly created certificate template
- Configure the AD FS Servers to use the new certificate template
- Create a Key Vault in Azure and Set the Access Policy for WVD Application
- Configure your Azure Virtual Desktop host pool
Due to very long details I have divided the blog in 2 Parts. This is the first part of the Blog.
Step 1: Purchase a domain from Azure.
Now, in the first step, we need to buy a public domain name. For this being a fond of Azure I don’t want to go outside to another 3rd party domain name sellers like Godaddy, I have purchased the domain from Microsoft Azure and to manage that domain I need to visit the DNS Zones in the Azure Portal. Once I open the DNS Zone in the Azure Portal it looks like the below.
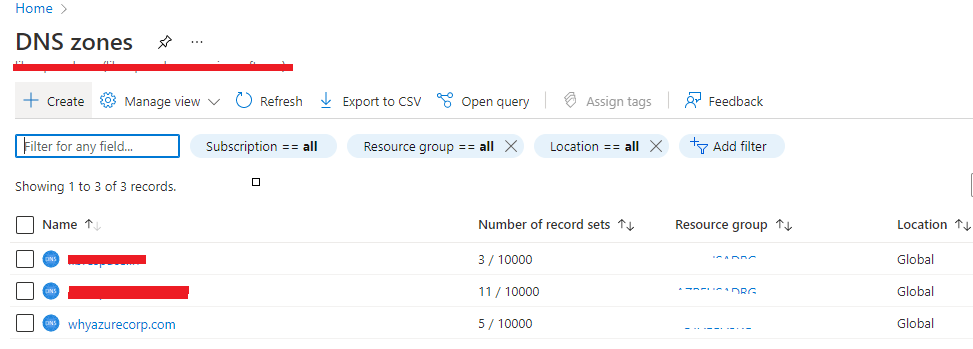
Whyazurecorp.com is the domain name of my lab where I am going to create everything.
Now, once the first step is completed, I need to go to the 2nd step where I wanted to add a domain to O365.
Step 2: Add a domain to Microsoft 365.
To add, modify, or remove domains, you must be a Domain Name Administrator or Global Administrator of a business or enterprise plan.
First, we need to add a domain in your Microsoft O365 Admin Center as shown below.
- Go to the admin center at https://admin.microsoft.com.
- Go to the Settings > Domains page.
- Select Add domain.
- Enter the name of the domain you want to add, then select Next.
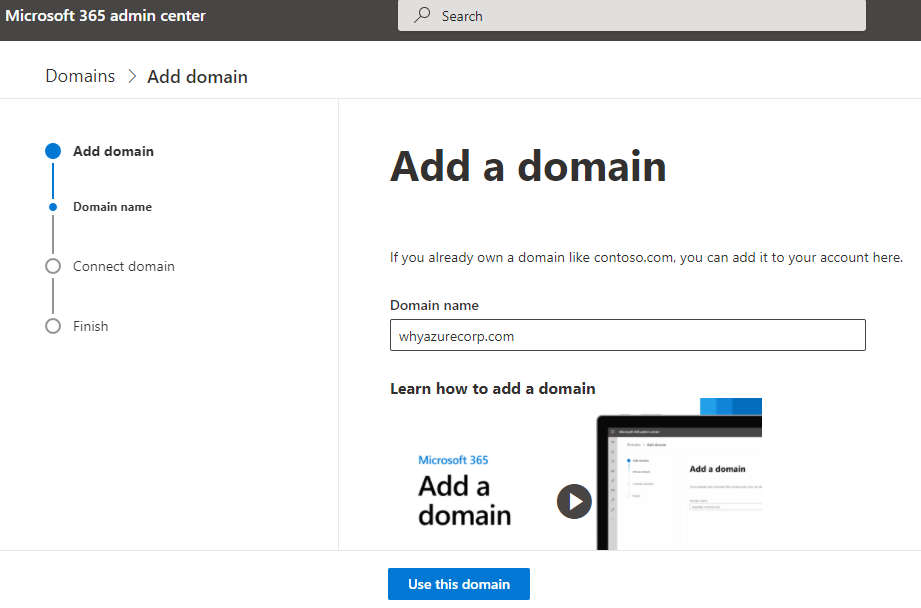
Step 2: You need to verify the domain. Choose how you want to verify that you own the domain.
There are multiple options available to verify the domain.
- If your domain registrar uses Domain Connect, Microsoft will set up your records automatically by having you sign in to your registrar and confirm the connection to Microsoft 365. You’ll be returned to the admin center and Microsoft will then automatically verify your domain.
- You can use a TXT record to verify your domain. Select this and select Next to see instructions for how to add this DNS record to your registrar’s website. This can take up to 30 minutes to verify after you’ve added the record.
- You can add a text file to your domain’s website. Select and download the .txt file from the setup wizard, then upload the file to your website’s top-level folder. The path to the file should look similar to: http://mydomain.com/ms39978200.txt. We’ll confirm you own the domain by finding the file on your website.
- If you chose to add DNS records yourself, select Next and you’ll see a page with all the records that you need to add to your registrar’s website to set up your domain.
- If the portal doesn’t recognize your registrar, you can follow these general instructions.
- If you don’t know the DNS hosting provider or domain registrar for your domain, see Find your domain registrar or DNS hosting, provider.
- If you want to wait for later, either unselect all the services and click Continue or in the previous domain connection step choose More Options and select Skip this for now.
- Now, I need to verify the domain.
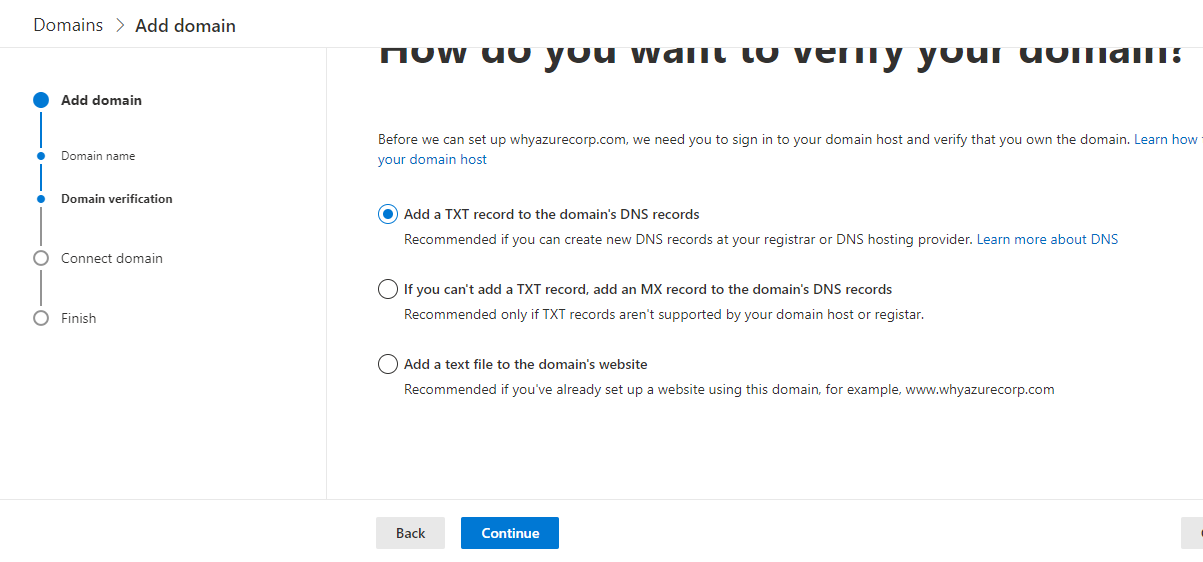
- In the next step click on verify button to verify but before you click the button you need make sure you have copied TXT and TTL details in the DNS zone in Azure
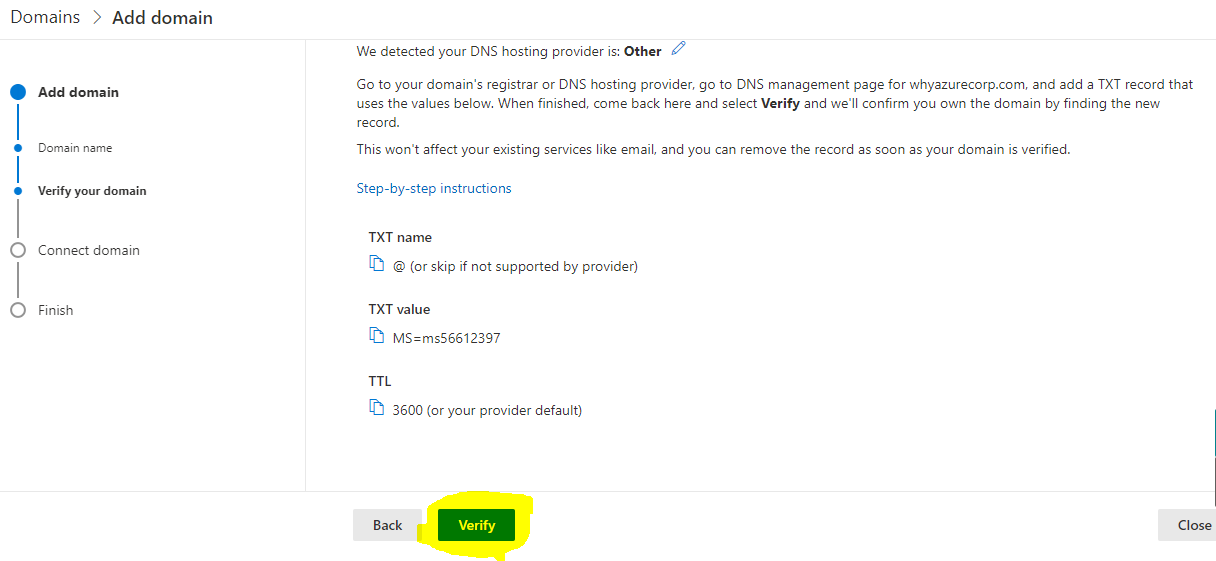
For our case we have chosen the 2nd option where we have manually added the text record to the Azure DNS zone.
- Sign in to the azure portal at https://portal.azure.com.
- Go to the DNS Zone page.

- On the Domains page, select a domain.
- Under DNS settings, select Custom Records (In the right side); then select Add record.
I have added the TXT record like below
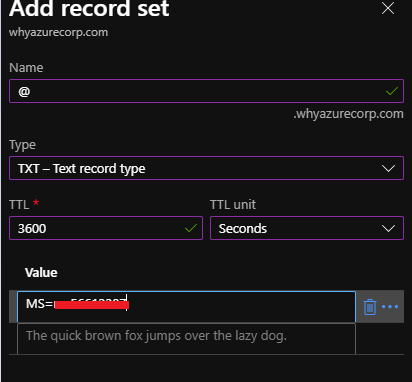
- Select the type of DNS record you want to add and type the information for the new record.
- Select Save.
Next is to add the records which you have just copied from o365 portal.
Once those records are added in the DNS zone you should be able to successfully validate the domain from O365 console.
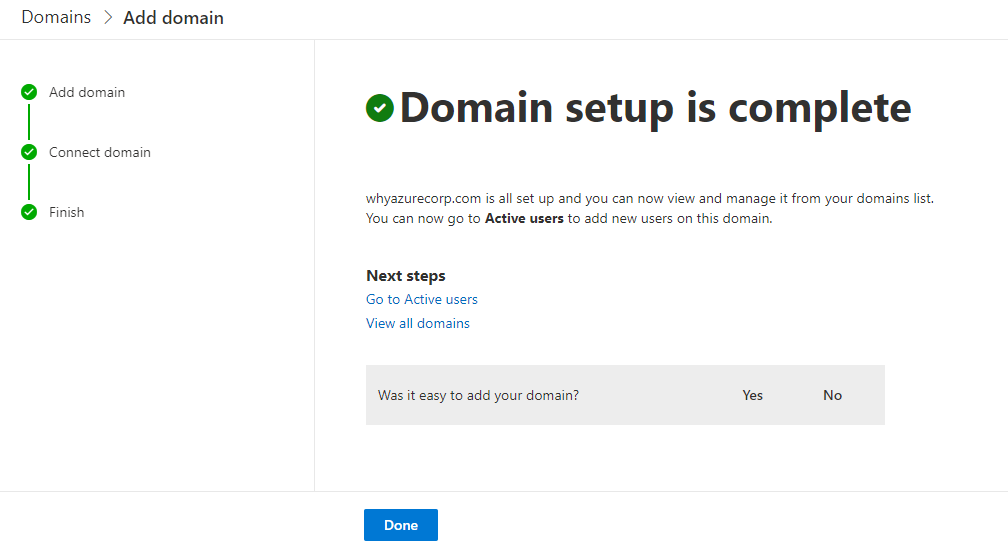
As you can now see the domain setup is completed.
Step 3: Buy a certificate from Azure Service Certificates for the ADFS
Our target will be to Purchase a public SSL certificate and export it into a PFX file, for this I have gone to the App Service Certificate in Azure.
I have clicked on Create the App Service Certificate.
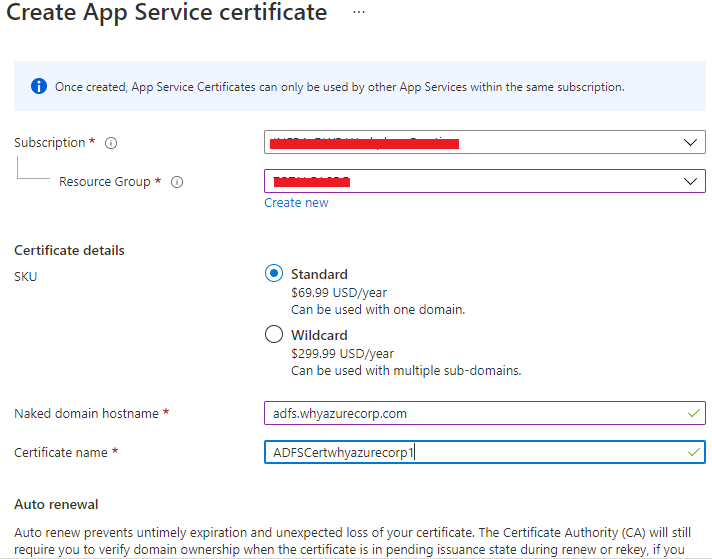
Once the purchase is done I can view the certificate as you can see here.
![]()
You have to store the certificate in an Azure Key Vault for the future use.
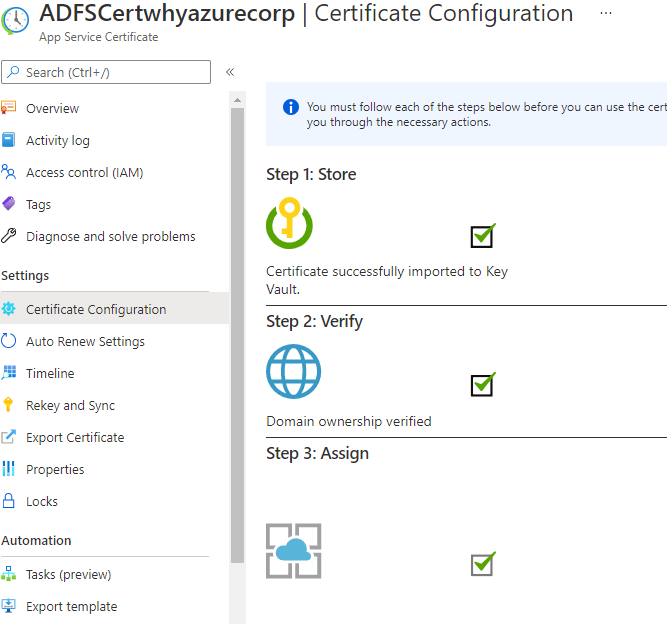
I have later downloaded the certificate from the Key Vault for future use. And installed the Certificate in the ADFS server.
Step 4: Add the ADFS Server role.
- Open Server Manager. To open Server Manager, click Server Manager on the Start screen, or Server Manager in the taskbar on the desktop. In the QuickStart tab of the Welcome tile on the Dashboard page, click Add roles and features. Alternatively, you can click Add Roles and Features on the Manage menu.
- On the Before you begin page, click Next.
- On the Select installation type page, click Role-based or feature-based installation and then click Next.
- On the Select destination server page, click Select a server from the server pool, verify that the target computer is selected, and then click Next.
- On the Select server roles page, click Active Directory Federation Services and then click Next.
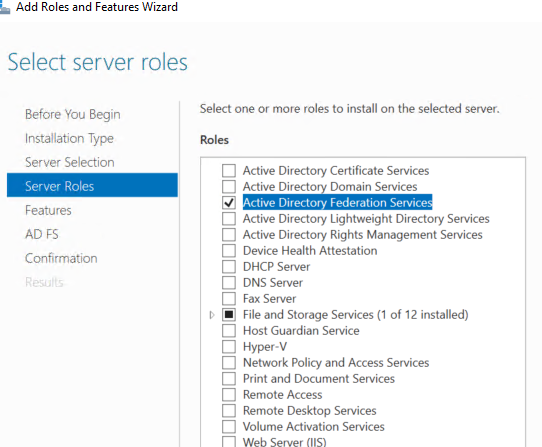
On the Select features page, click Next. The required prerequisites are preselected for you. You do not have to select any other features.
On the Active Directory Federation Service (AD FS) page, click Next.
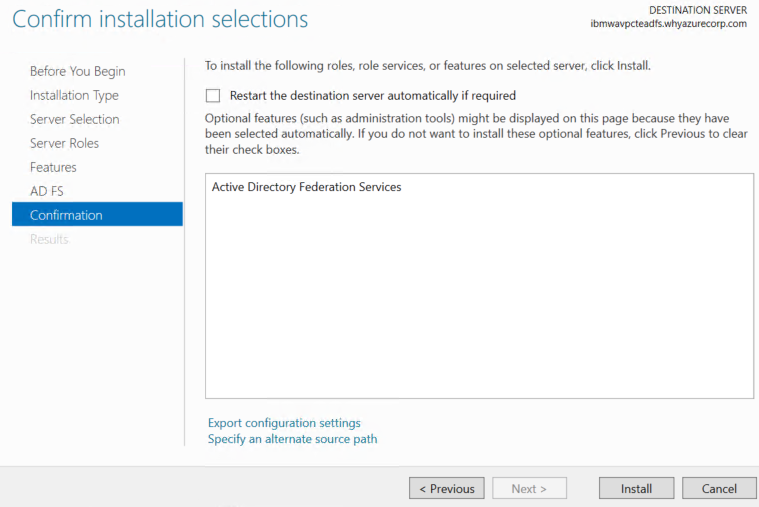
After you verify the information on the Confirm installation selections page, click Install.
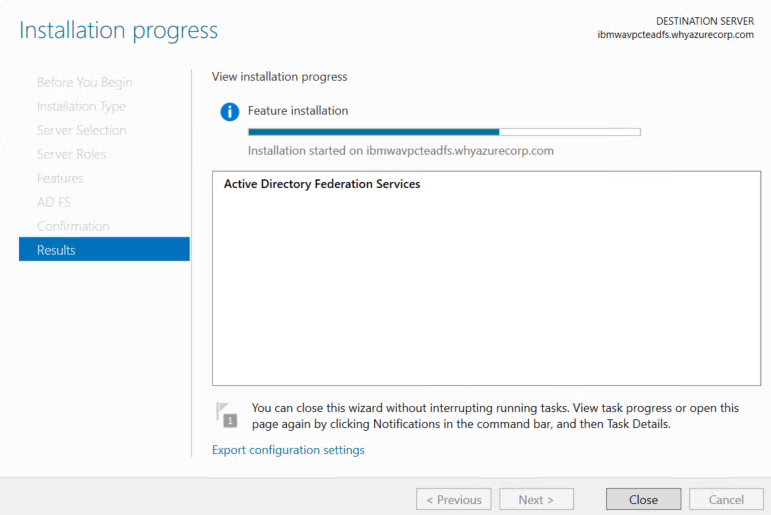
On the Installation progress page, verify that everything installed correctly, and then click Close.
Step 5: Configure the first federation server in a new federation server farm
To configure the first federation server in a new federation server farm by using the Active Directory Federation Service Configuration Wizard please follow the steps.
On the Server Manager Dashboard page, click the Notifications flag, and then click Configure the federation service on the server.
The Active Directory Federation Service Configuration Wizard opens.
On the Welcome page, select Create the first federation server in a federation server farm, and then click Next.
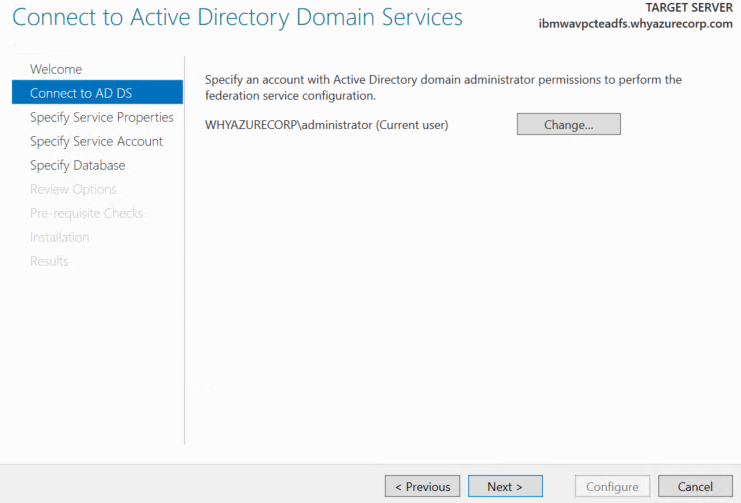
On the Connect to AD DS page, specify an account by using domain administrator permissions for the Active Directory (AD) domain to which this computer is joined, and then click Next.
On the Specify Service Properties page, do the following, and then click Next:
- Import the .pfx file that contains the Secure Socket Layer (SSL) certificate and key that you have obtained earlier in step 3, you have obtained this certificate and copied it onto the computer that you want to configure as a federation server. To import the .pfx file via the wizard, click Import, and then browse to the file’s location. Enter the password for the .pfx file when you are prompted.
- Provide a name for your federation service. For example, ibmwavpcteadfs.whyazurecorp.com. This name must match one of the subject or subject alternative names in the certificate.
- Provide a display name for your federation service. For example, WhyAzure Corp. Users see this name on the Active Directory Federation Services (AD FS) sign-in page.
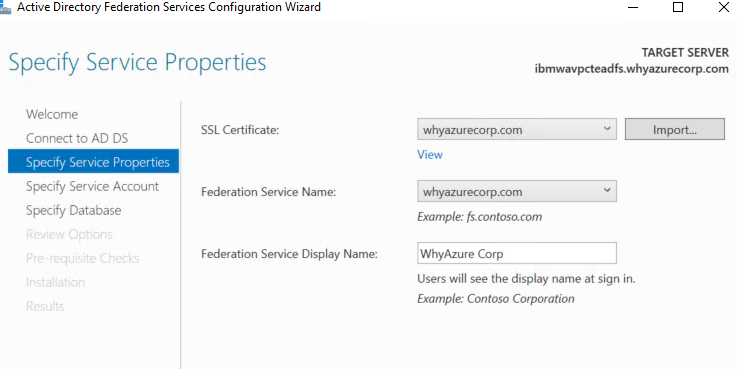
On the Specify Service Account page, specify a service account. You can either create or use an existing group Managed Service Account (gMSA) or use an existing domain user account. If you select the option to create a new gMSA account, specify a name for the new account. If you select the option to use an existing gMSA or domain account, click Select to select an account.
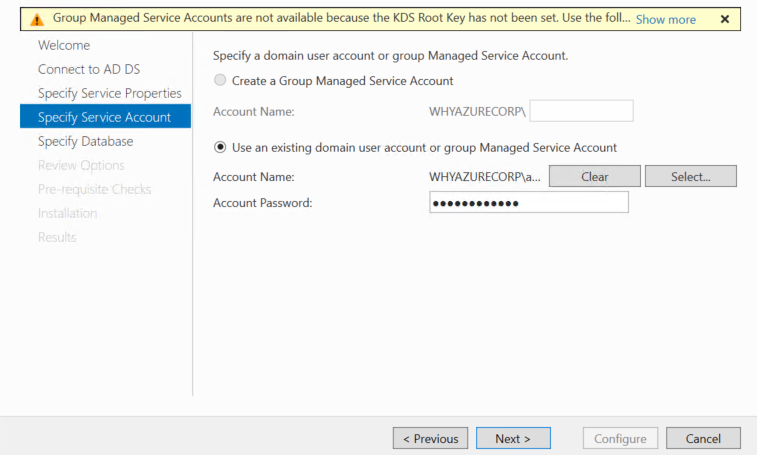
On the Specify Configuration Database page, specify an AD FS configuration database, and then click Next. You can either create a database on this computer by using Windows Internal Database (WID), or you can specify the location and the instance name of Microsoft SQL Server.
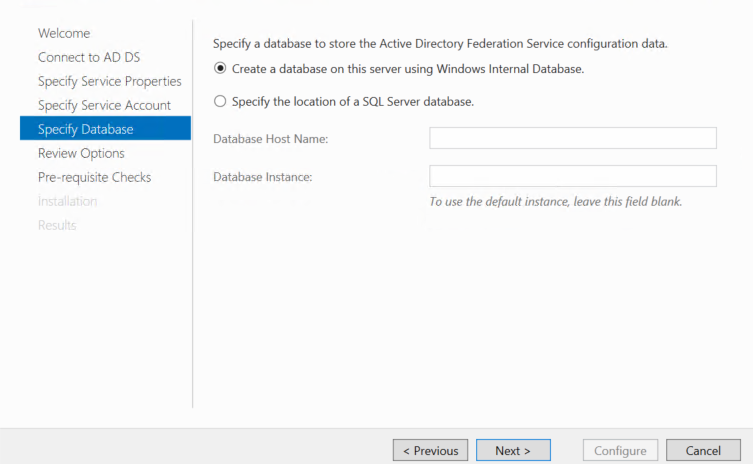
On the Review Options page, verify your configuration selections, and then click Next.
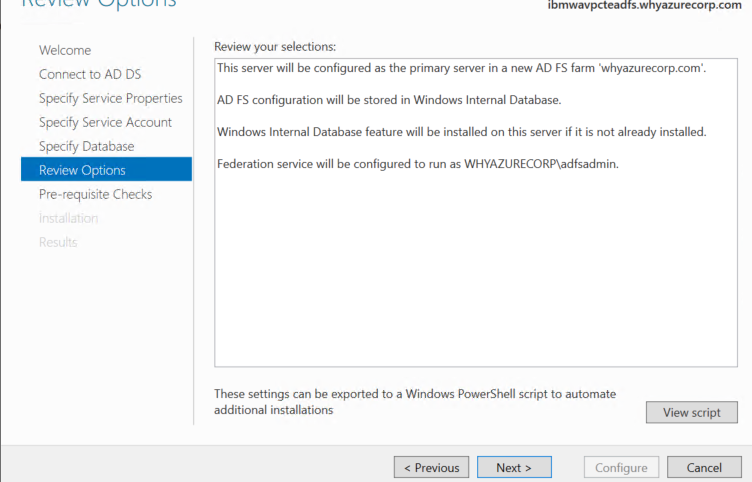
On the Pre-requisite Checks page, verify that all prerequisite checks are successfully completed, and then click Configure.
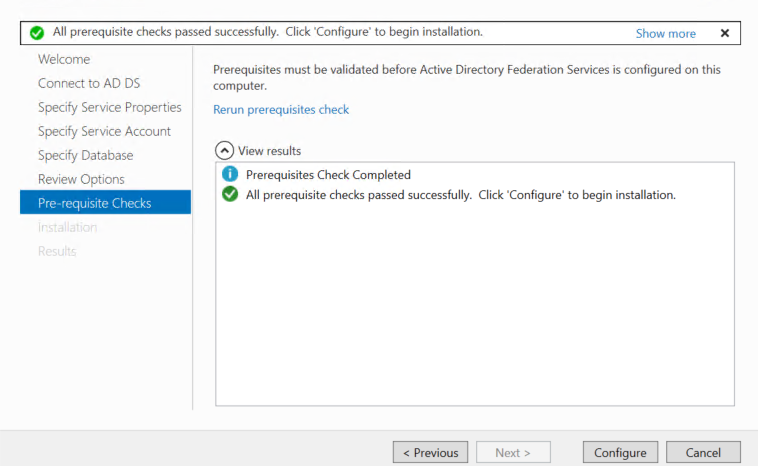
On the Results page, review the results and check whether the configuration is completed successfully, and then click Next steps required for completing your federation service deployment
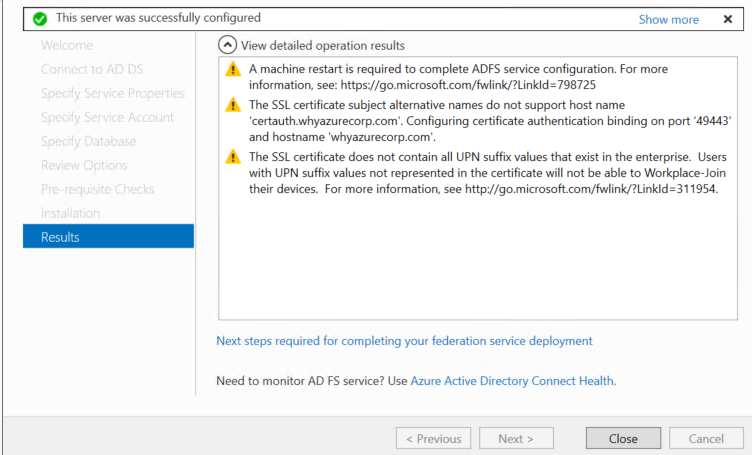
Step 6: Configure Azure AD Connect for TLS 1.2
Let’s see what are pre -requisite for this setup
Azure AD
For this lab you need an Azure AD tenant allows, by default, 50,000 objects. When you verify your domain, the limit increases to 300,000 objects. If you need even more objects in Azure AD, open a support case to have the limit increased even further. If you need more than 500,000 objects, you need a license, such as Microsoft 365, Azure AD Premium, or Enterprise Mobility + Security.
Active Directory
On-premises Active Directory
- The Active Directory schema version and forest functional level must be Windows Server 2003 or later. The domain controllers can run any version as long as the schema version and forest-level requirements are met.
- If you plan to use the feature password writeback, the domain controllers must be on Windows Server 2016 or later.
- The domain controller used by Azure AD must be writable. Using a read-only domain controller (RODC) isn’t supported, and Azure AD Connect doesn’t follow any write redirects.
- Using on-premises forests or domains by using “dotted” (name contains a period “.”) NetBIOS names isn’t supported.
I assume you already have an on-premise AD already deployed and now you need to configure the Azure AD Connect.
Azure AD Connect server
The Azure AD Connect server contains critical identity data. It’s important that administrative access to this server is properly secured. Follow the guidelines in Securing privileged access.
The Azure AD Connect server must be treated as a Tier 0 component as documented in the Active Directory administrative tier model
Pre-req for the Azure AD Connect Server
- Azure AD Connect must be installed on a domain-joined Windows Server 2016 or later.
- The minimum .Net Framework version required is 4.6.2, and newer versions of .Net are also supported.
- Azure AD Connect can’t be installed on Small Business Server or Windows Server Essentials before 2019 (Windows Server Essentials 2019 is supported). The server must be using Windows Server standard or better.
- The Azure AD Connect server must have a full GUI installed. Installing Azure AD Connect on Windows Server Core isn’t supported.
- The Azure AD Connect server must not have PowerShell Transcription Group Policy enabled if you use the Azure AD Connect wizard to manage Active Directory Federation Services (AD FS) configuration. You can enable PowerShell transcription if you use the Azure AD Connect wizard to manage sync configuration.
- If AD FS is being deployed:
- The servers where AD FS or Web Application Proxy are installed must be Windows Server 2012 R2 or later. Windows remote management must be enabled on these servers for remote installation.
- You must configure TLS/SSL certificates. For more information, see Managing SSL/TLS protocols and cipher suites for AD FS and Managing SSL certificates in AD FS.
- You must configure name resolution.
- It is not supported to break and analyze traffic between Azure AD Connect and Azure AD. Doing so may disrupt the service.
- If your global administrators have MFA enabled, the URL https://secure.aadcdn.microsoftonline-p.com must be in the trusted sites list. You’re prompted to add this site to the trusted sites list when you’re prompted for an MFA challenge and it hasn’t been added before. You can use Internet Explorer to add it to your trusted sites.
- If you plan to use Azure AD Connect Health for syncing, ensure that the prerequisites for Azure AD Connect Health are also met. For more information, see Azure AD Connect Health agent installation.
Download Azure AD Connect from a server joined to the domain. Enable TLS 1.2 for Azure AD Connect, in our server it was not present so we need to enable it.
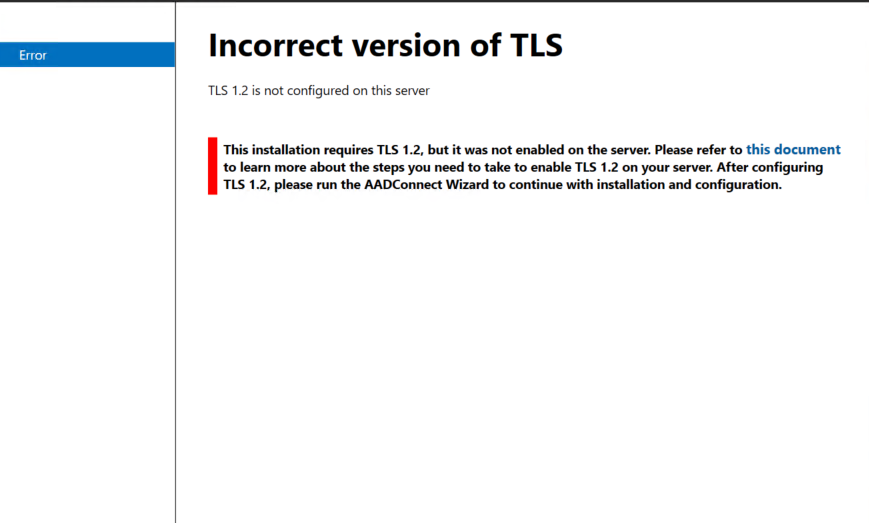
I have run the below PowerShell script to enable TLS 1.2, Prior to version 1.1.614.0, Azure AD Connect by default uses TLS 1.0 for encrypting the communication between the sync engine server and Azure AD. You can configure .NET applications to use TLS 1.2 by default on the server. For more information about TLS 1.2, see Microsoft Security Advisory 2960358.
New-Item ‘HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319’ -name ‘SystemDefaultTlsVersions’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319’ -name ‘SchUseStrongCrypto’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319’ -name ‘SystemDefaultTlsVersions’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319’ -name ‘SchUseStrongCrypto’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
Write-Host ‘TLS 1.2 has been enabled.’
Once it’s enabled you can run the Azure AD connect wizard. Azure AD Connect has two installation types for new installation: Express and customized. This topic helps you to decide which option to use during installation.
Step 7: Install Azure AD Connect
Express
Express is the most common option and is used by about 90% of all new installations. It was designed to provide a configuration that works for the most common customer scenarios.
It assumes:
- You have a single Active Directory forest on-premises.
- You have an enterprise administrator account you can use for the installation.
- You have less than 100,000 objects in your on-premises Active Directory.
You get:
- Password hash synchronization from on-premises to Azure AD for single sign-on.
- A configuration that synchronizes users, groups, contacts, and Windows 10 computers.
- Synchronization of all eligible objects in all domains and all OUs.
- Automatic upgrade is enabled to make sure you always use the latest available version.
Now, Sign in as a local administrator to the server you wish to install Azure AD Connect on. You should do this on the server you wish to be the sync server.
Navigate to and double-click AzureADConnect.msi.
On the Welcome screen, select the box agreeing to the licensing terms and click Continue.
On the Express settings screen, click Use express settings.
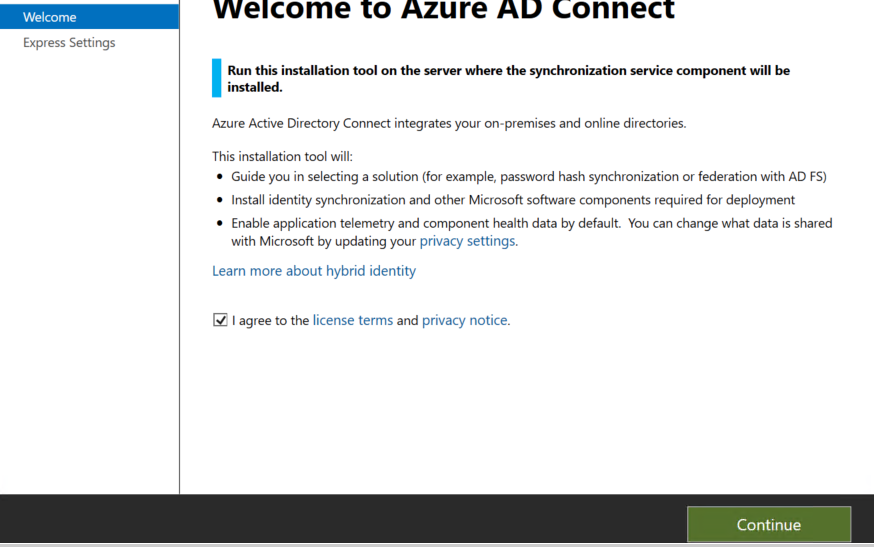
You can click on the express settings as this is the most common option.
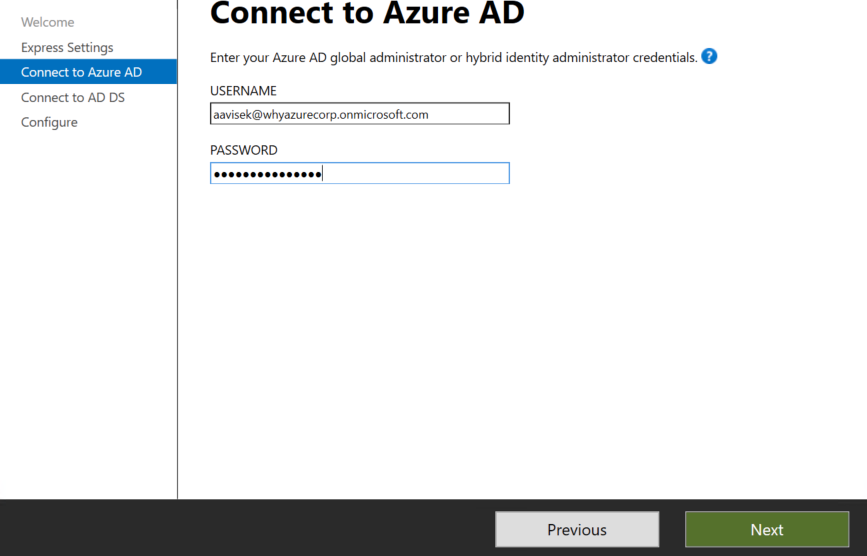
On the Connect to Azure AD screen, enter the username and password of a global administrator for your Azure AD. Click Next.
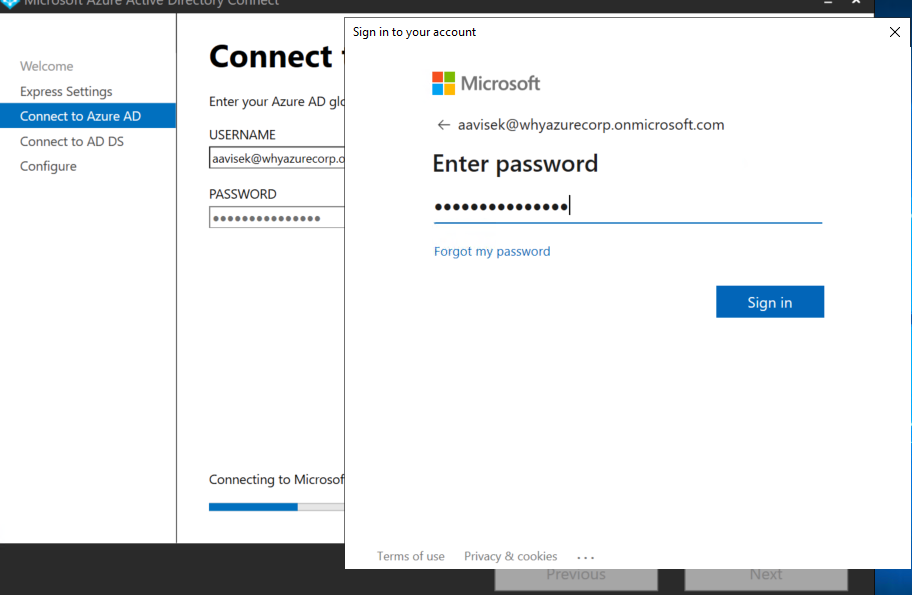
Enter the UPN and password to connect to Azure AD
You will see a screen that configuring is going on
After few seconds the configuration will be completed and you will see the below screen.
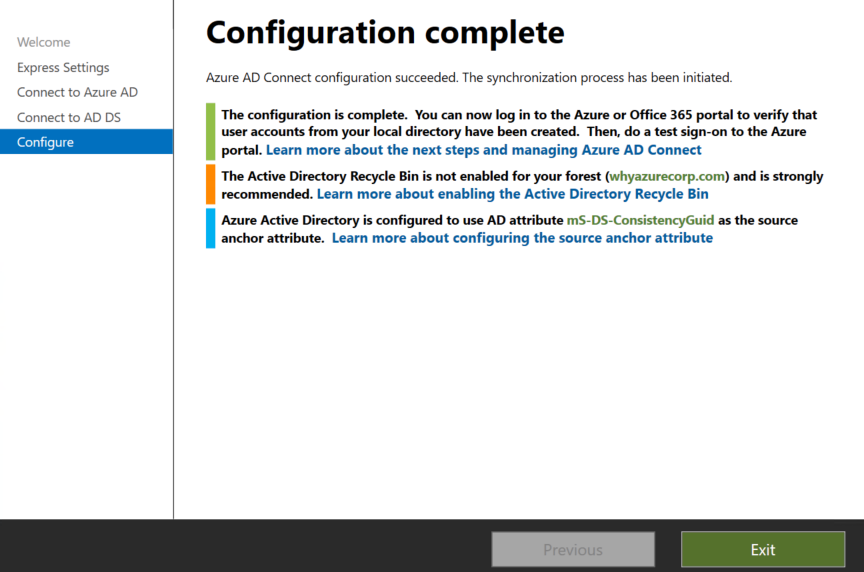
Step 8: Configure Azure AD connect for ADFS
On the Connect to Azure AD page, enter a global admin account and password. If you selected Federation with AD FS on the previous page, don’t sign in with an account that’s in a domain you plan to enable for federation.
You might want to use an account in the default onmicrosoft.com domain, which comes with your Azure AD tenant. This account is used only to create a service account in Azure AD. It’s not used after the installation finishes.
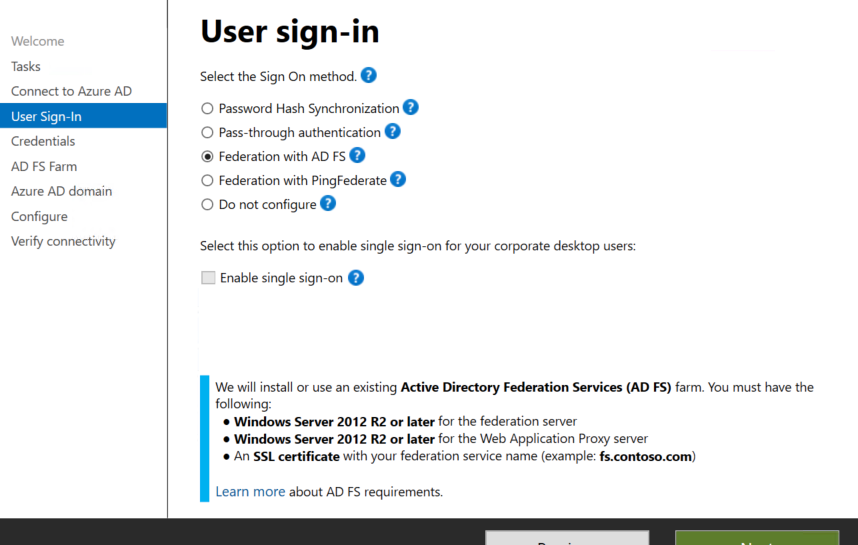
In the next screen you need to change the default sign in process.
Select the sign in option Federation with AD FS
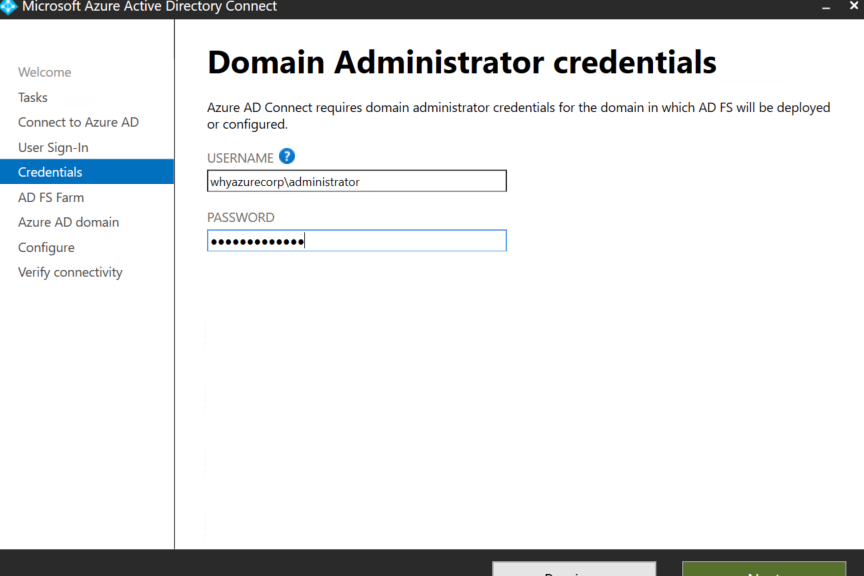
Enter Domain administrator credential for the ADFS on-premises domain
Click on Configure a new AD FS farm
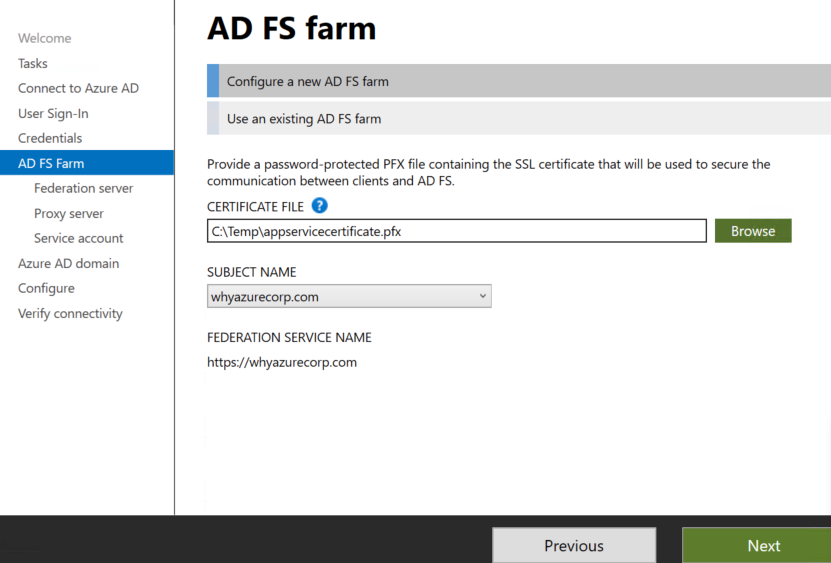
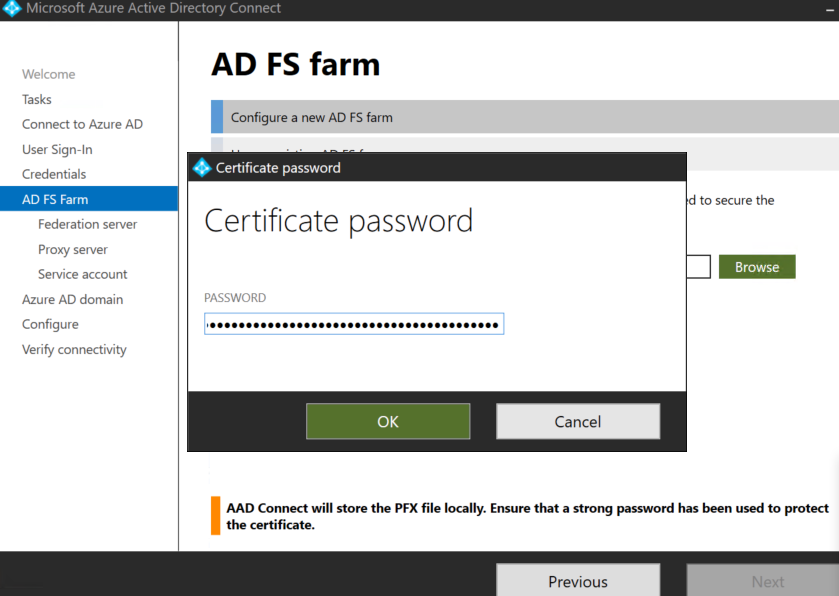
Browse the certificate you have used in Step 3 and enter the password of the certificate
In next step select the on-premises ADFS server.
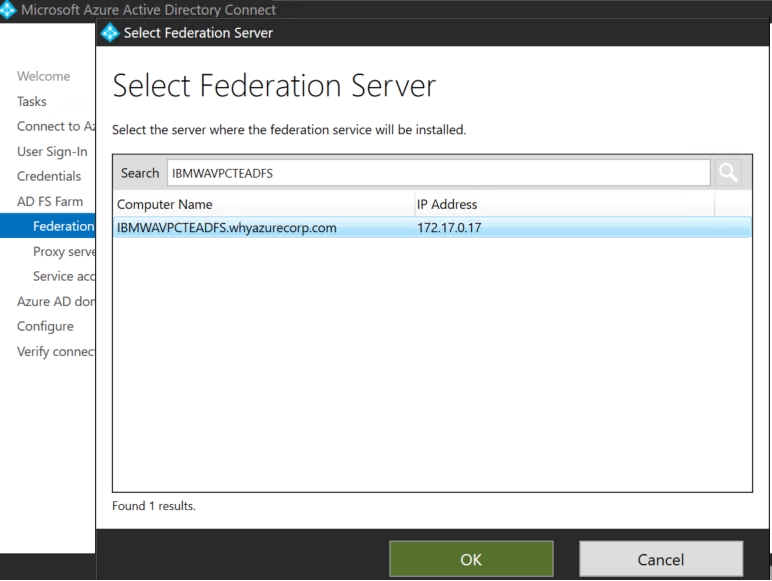
Click next
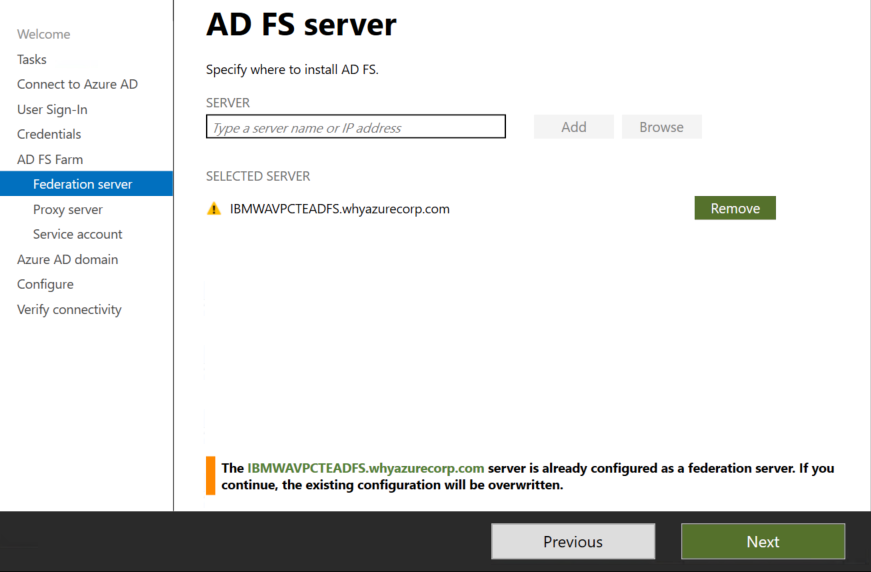
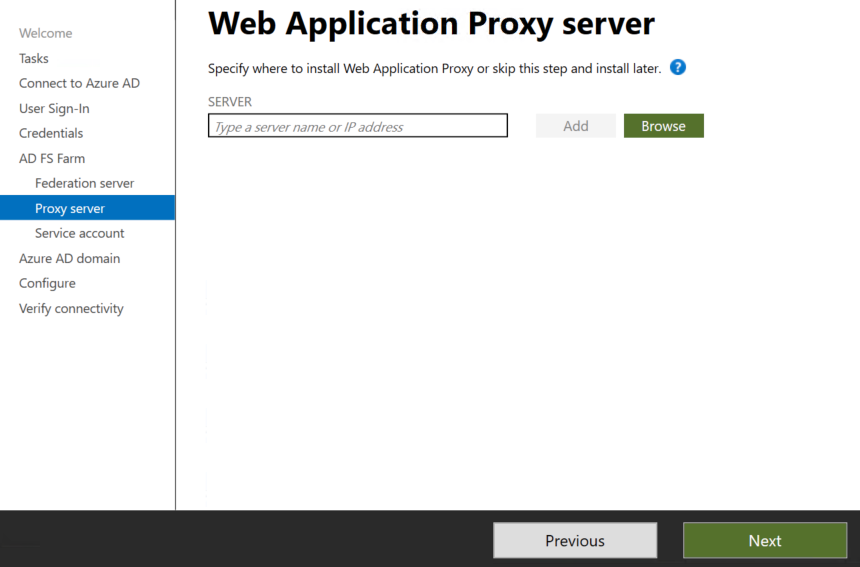
In next step you need to configure the ADFS Proxy which we don’t have in the lab environment so we have clicked next.
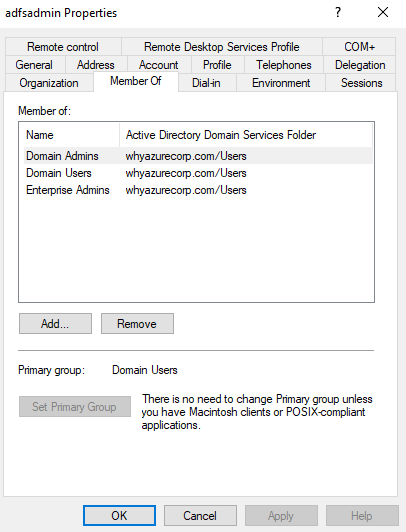
Now I have to create the service account which we will be using for this integration.
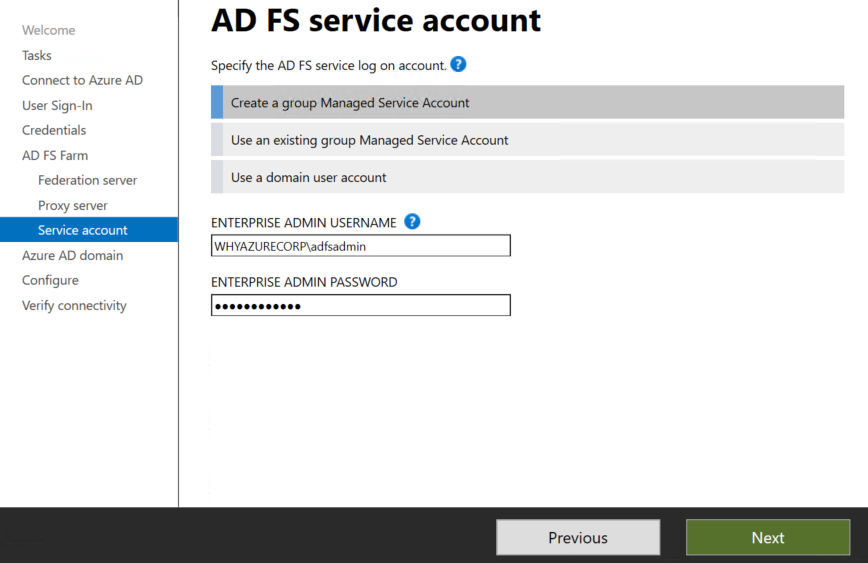
Now I will click on next after adding the account which I just have created
In next step it will fetch the Azure AD domain
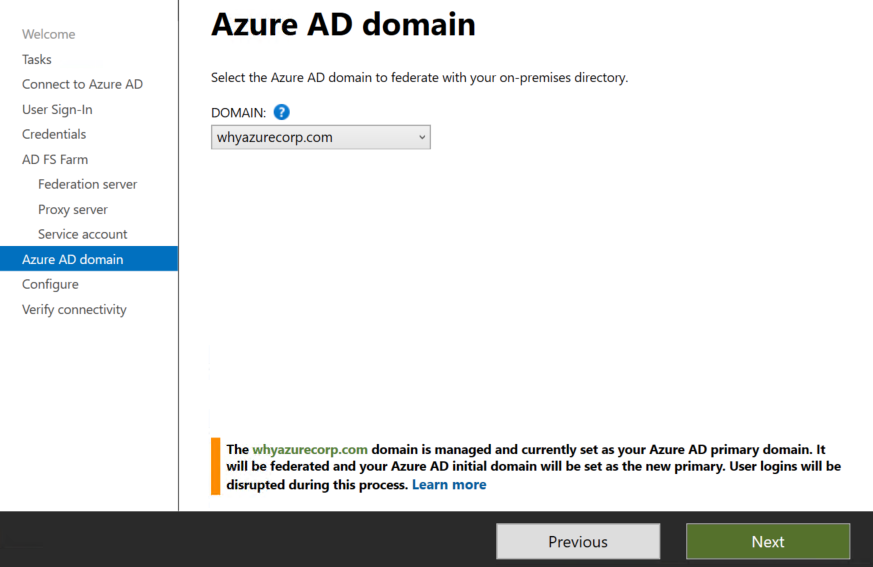
Once everything is done you can click on ready to configure.
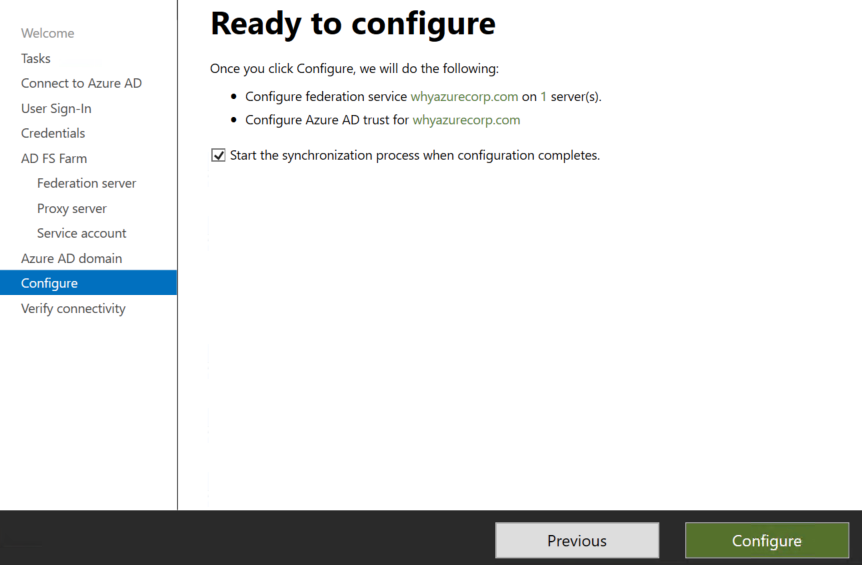
It will take some time to configure
In next step it will show the configuration completed as shown below.
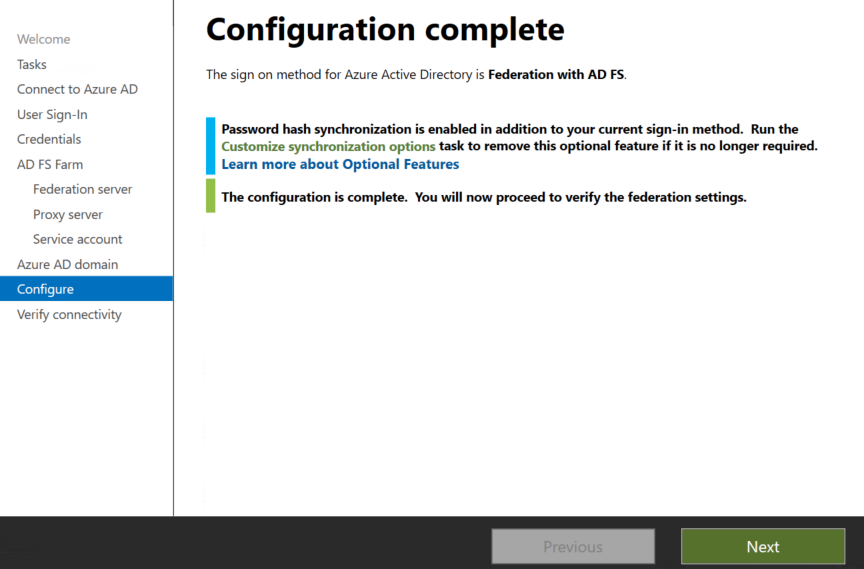
Now in last step we need to verify the federaion connectivity.
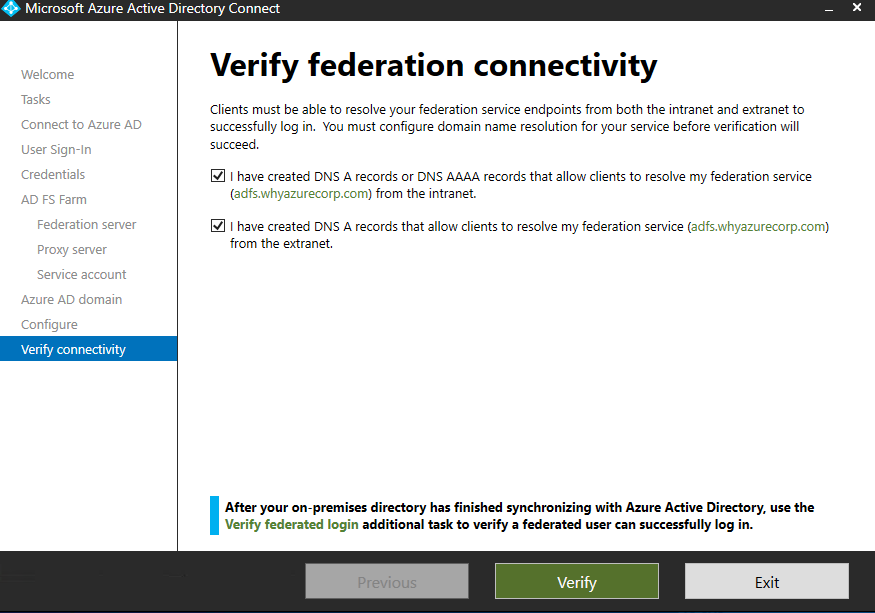
Azure AD Connect verifies the DNS settings when you select the Verify button. It checks the following settings:
- Intranet connectivity
- Resolve federation FQDN: Azure AD Connect checks whether the DNS can resolve the federation FQDN to ensure connectivity. If Azure AD Connect can’t resolve the FQDN, then the verification fails. To complete the verification, ensure that a DNS record is present for the federation service FQDN.
- DNS A record: Azure AD Connect checks whether your federation service has an A record. In the absence of an A record, the verification fails. To complete the verification, create an A record (not a CNAME record) for your federation FQDN.
- Extranet connectivity
- Resolve federation FQDN: Azure AD Connect checks whether the DNS can resolve the federation FQDN to ensure connectivity.
In my first verification test both have failed.
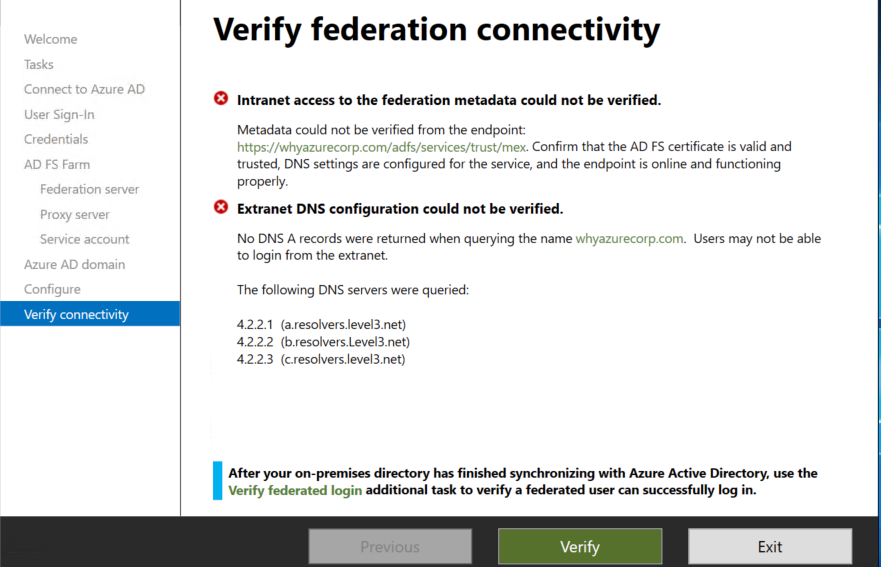
I have login to the local on-premises DNS server and created the A record for ADFS server.
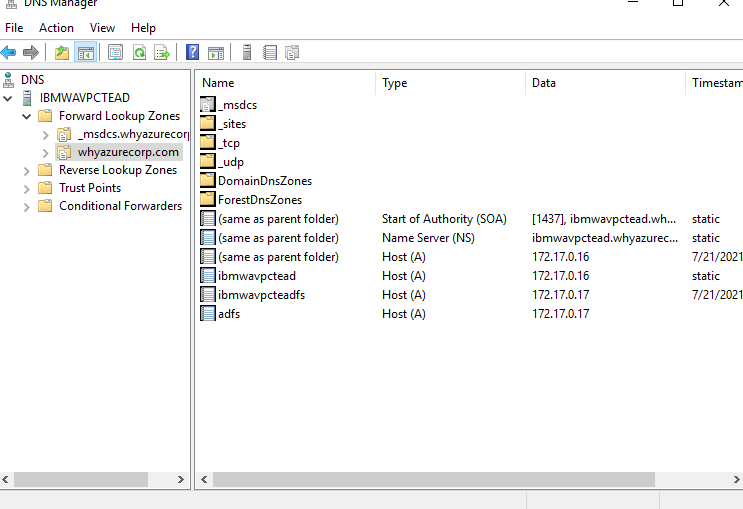
Similarly I have created the A record in the external DNS server by going to the DNS zone in Azure. In our case the record name is adfs.whyazurecorp.com

Go to Add Records
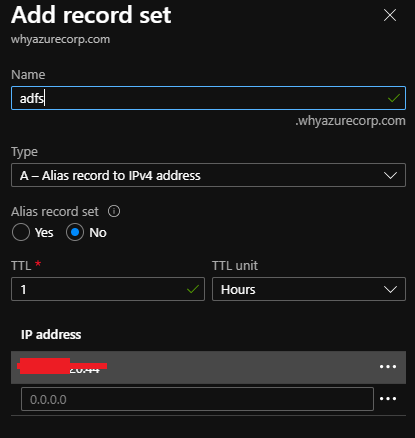
Once you add the records it will show like in the DNS zone in the Azure console

Now again go back to the AD Sync server and verify the connectivity.

The connectivity looks good with a warning.
Up to this all looks good and I able to login to portal.office.com with my UPN which is going through the federation page.
That’s all you for today, this post is divided in two parts and I have covered Step 1 to step 8 in the part 1 of this blog , to read about the next part of the blog please click here. The next part will cover from step 9 to step 15.