Deploying Azure Active Directory Privileged Identity Manager
Recently I got a chance to work on Azure AD Privileged Identity Manager which can enable any enterprise to reduce risks associated with privileged users and their access rights. Azure AD Privileged Identity Management is available as part of the Premium P2 edition of Azure AD.
Before you start planning for Azure PIM, you need to check whether that is already available in your license the SkuPartNumber is “AAD_PREMIUM_P2” or “EMSPREMIUM”
You can login to your office 365 account with the following powershell command and can find the following:
$credential = Get-Credential
$credential
Set-ExecutionPolicy RemoteSigned
Import-Module MsOnline
Get-Module
Connect-MsolService -Credential $credential
You can run the following command to check the available licenses for your tenant
Get-MsolAccountSku
Get-MsolAccountSku | Select-Object -ExpandProperty ServiceStatus
Why Azure AD Premium is a requirement of any organization?
Security Concern
Traditionally, both on-premises and in the cloud, most IT admins have needed to have permanent and unmonitored permissions to high-value resources, in order to do their day to day jobs. This is convenient, but it poses major security concerns because their user accounts become high-value targets for security attacks. In many recent high-profile security breaches around the world, a hacker found a way to use side-ways elevation of privileges until they were able to compromise a user account with permanently assigned privileged roles. Then the attacker used that account to access resources across the organization’s network, in many cases going undetected for months.
How PIM can help?
Azure AD PIM can help any organization by enabling it to reduce risks associated with privileged users and their access rights.
Principle of Identity & Access Management @ PIM
- The PIM can be implemented by using the Role Based Access Control (RBAC) with the principle of least privilege.
- The PIM will have both the modern features of Just-in-time(JIT) and Just-Enough-Administration (JEA) of Access and Identity Control.
- The above features allow an organization to elevate the permissions that a user has on some resources for a predefined amount of time.
- The PIM will have approval workflow.
- MFA (Multi-Factor Authentication) can be implemented for the privilege elevation requests.
- The PIM automatically keeping track of all these actions for audit purposes.
- Easily review role assignments for compliance, internal audit, or general lifecycle management.
- Detect potential risks and fix them with a click of a button via preconfigured alerts and activity logs.
- Provide employees the ability to self-activate administration privileges at any time.
PIM User Process Workflow
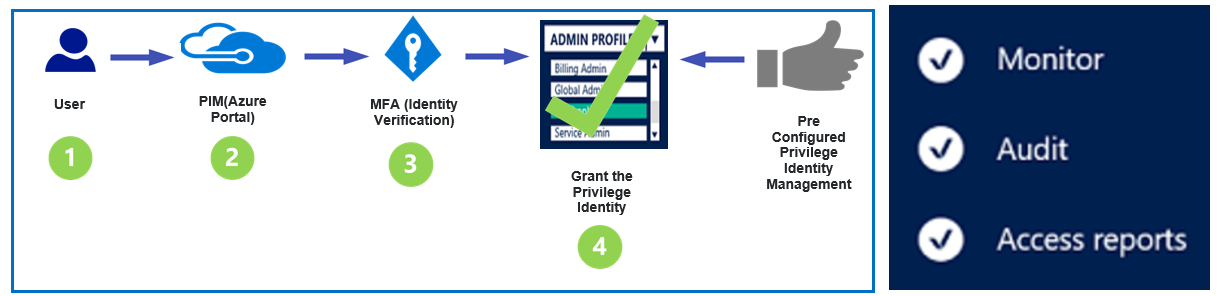
- An admin user who need access to some pre-defined role in O365 login to the Azure portal with his UPN (User Principle Name) and request the access in PIM.
- The user will open the PIM blade in Azure and request the activation of the new role.
- Since we have enforced the requirement for MFA for this role activation, the user first asked to re-validate the identity.
- The user will be requested to provide a reason for the elevation request.
- Once the request is approved (Auto Approved in our case), the user can view the new access level and the duration for which the permissions have been granted.
License Requirement and PIM Admin workflow
The EMSPREMIUM (EMS5) license is required for each users who can use the PIM features.
Azure AD Privileged Identity Management is available as part of the Premium P2 edition of Azure AD.
PIM Admin Workflow
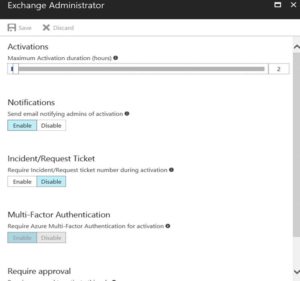
- Azure PIM Administrator 1st step is to configure and define the privileged role. (For Example during our POC we have configured Exchange Administrator role and we have configured a maximum activation duration for 4 hrs, requirement for MFA and no approval and not enabled the admin notifications.)
- The 2nd step will be to add a new user to this role (note that the permission assigned is eligible as opposed to permanent)
- In the 3rd step administrator can track, audit and can review all the actions carried out by users.
Key Roles in PIM
As a Privileged Role Administrator (PRA) you can:
- Enable approval for specific roles
- Specify approver users and/or groups to approve requests
- View request and approval history for all privileged roles
As a designated approver, you can:
- View pending approvals (requests)
- Approve or reject requests for role elevation (single and/or bulk)
- Provide justification for approval/rejection
As an Eligible Role User you can:
- Request activation of a role that requires approval
- View the status of your request to activate
- Complete your task in Azure AD if activation was approved
POC – Findings
A POC has been carried out to test the features of PIM. The following activities has been carried out.
- Assigned the security admin role to one of the Service Account.
- Tested all the security admin workflow with the Exchange Admin Role. And it’s executed successfully.
- End user’s side workflow has been tested successfully.
- JIT and JEA has been tested and verified.
- Bulk License Assignment script tested successfully.
- License removal script tested successfully.
Steps to configure the PIM
There are two types of roles you can assign to a user. One is Permanent and the other is Eligible. Please find the screenshot.
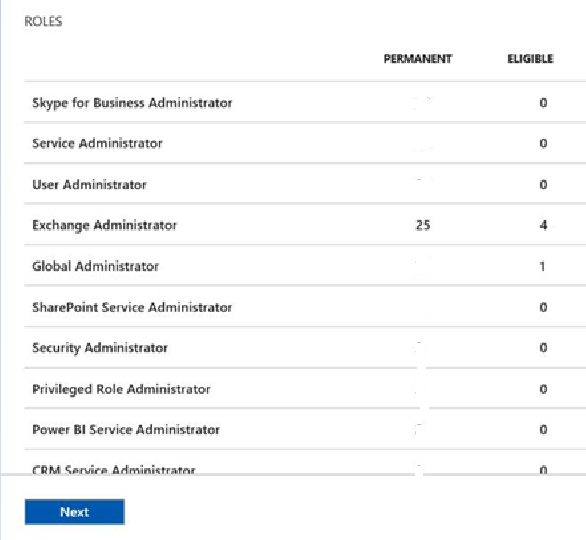
Eligible users are those users who are eligible to apply for the Admin Roles for a fixed duration. As you can see below I have allowed few users who are allowed to request exchange admin roles for a fixed duration which is called Maximum Activation Duration. Here I can see my name is showing as eligible.
There is a tab where you can define the global configuration for all roles. For example I have created Exchange Admins, where I have set maximum activation duration.

Once this configuration is completed and the license is assigned to the users, the user can login to the azure portal and request for the PIM, the user need to take the following steps.
Step 1: Please login to the Azure Portal with your office 365 Account. (http://portal.azure.com)
Step 2: Click on More Services
Step 3: Click on Azure AD Privileged Identity Management
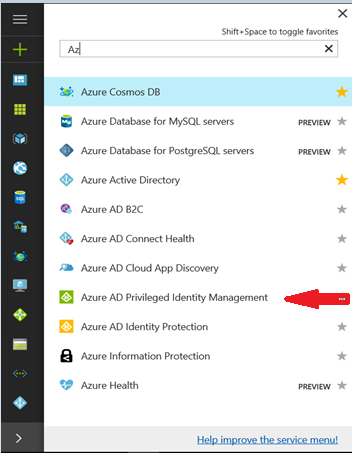
Step 4: Click on the Tasks-My Roles
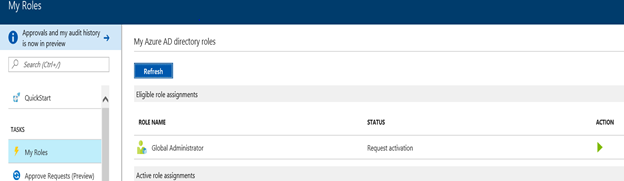
Step 5: Click on the Play Button under Action
Step 6: Click on Verify your identity before proceeding.

Step 7: Your account will be verified with MFA
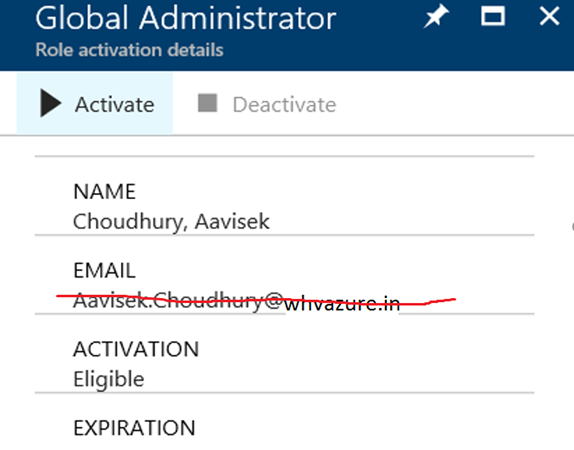
Step 7: Once Verified you can see the following screen. Please click on Activate.
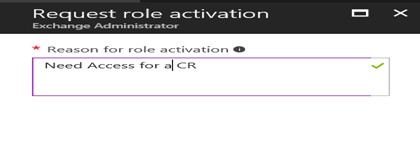
Step 8: Please provide the reason for Access Request and click on OK.
Step 9: Once the role will be activated you can immediately see the message in the right corner of your window.
Also you should receive a mail in your inbox.
Step 10: By default the Exchange Admin permissions has been activated for 2 Hrs. (This is the default policy which has been set by your Company security Administrator)
Note: You can deactivate this role by clicking the deactivate button.
Step 11: Login of the O365 portal and perform the required tasks.
I hope you will like this post. We will discuss more on Azure AD PIM in my future post.