Step-by-step process to configure sign-in frequency for AVD Users with Azure Conditional Access Policy
In March 2024, every time sign-in frequency Conditional Access option for Azure Virtual Desktop released for public preview. In today’s article, I will demonstrate how we can correctly configure the sign in frequency for the Azure Virtual Desktop.

In today’s interconnected digital landscape, ensuring the security of virtual desktop environments is paramount. Azure Virtual Desktop offers unparalleled flexibility, allowing users to access resources from anywhere, using various devices and clients. However, to safeguard both the environment and its users, implementing certain measures is imperative. One such measure is the utilization of Microsoft Entra multifactor authentication (MFA) with Azure Virtual Desktop. By integrating MFA into the sign-in process, users are prompted for an additional form of identification alongside their standard username and password. This additional layer of security significantly reduces the risk of unauthorized access. Enforcing MFA for Azure Virtual Desktop is made seamless through Conditional Access policies. Administrators have the flexibility to dictate the scope of MFA enforcement, whether it applies to web clients, mobile apps, desktop clients, or all client types, ensuring comprehensive protection across the board. When a user initiates a remote session, authentication is required both at the Azure Virtual Desktop service level and the session host level. With MFA enabled, users undergo the familiar process of providing their credentials along with a second form of authentication, enhancing the overall security posture. Moreover, the frequency of reauthentication can be tailored to align with organizational security policies. Microsoft Entra’s session lifetime configuration settings dictate how often users are prompted to reauthenticate. For instance, devices registered with Microsoft Entra ID receive a Primary Refresh Token (PRT) for single sign-on (SSO) functionality, valid for 14 days and continuously renewed with active usage. While the convenience of single sign-on is undeniable, it introduces potential security vulnerabilities, especially in enterprise scenarios involving personal devices. To mitigate this risk, administrators can adjust the authentication frequency, ensuring that users are prompted for MFA credentials more frequently. Conditional Access empowers administrators to fine-tune this behavior according to the organization’s security requirements.
Learn how to enforce MFA for Azure Virtual Desktop and configure sign-in frequency in the following sections.
What is Sign-in Frequency?
Sign-in frequency policies enable you to establish the duration after which a user must reconfirm their identity when accessing Microsoft Entra-based resources. This measure enhances the security of your environment, which is particularly crucial for personal devices, where the local operating system might not mandate multi-factor authentication (MFA) or automatically lock after a period of inactivity.
Below is the step-by-step process to configure the sign in frequency.
Prerequisites
Before you begin, ensure you have the following:
- Assign licenses to users that include Microsoft Entra ID P1 or P2.
- Create a Microsoft Entra group and add your Azure Virtual Desktop users to it.
- Enable Microsoft Entra multifactor authentication.
Here’s how to create a Conditional Access policy that requires multifactor authentication when connecting to Azure Virtual Desktop:
- Sign in to the Azure portal as a global administrator, security administrator, or Conditional Access administrator.
- In the search bar, type Microsoft Entra Conditional Access and select the matching service entry.
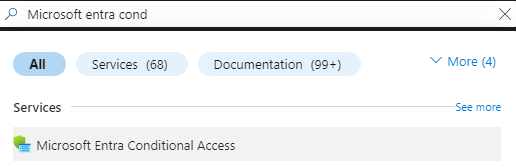
- From the overview, select Create new policy.
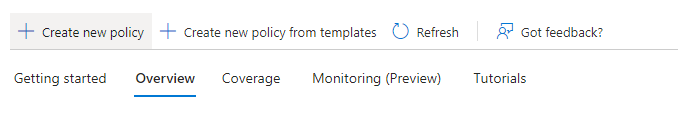
- Give your policy a name. Microsoft recommends that organizations create a meaningful standard for the names of their policies.
- Under Assignments > Users, select 0 users and groups selected.
- Under the Include tab, select Select users and groups and check Users and groups, then under Select, select 0 users and groups selected.
- On the new pane that opens, search for and choose the group that contains your Azure Virtual Desktop users as group members, then select Select.
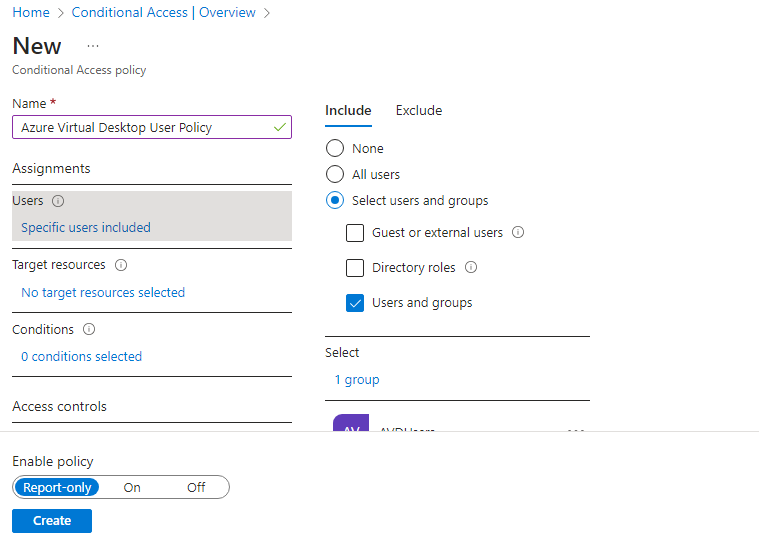
- Under Assignments > Target resources, select No target resources selected.
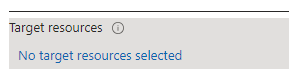
- Under the Include tab, select Select apps, then under Select, select Microsoft Desktop Virtualization.
| App name | App ID | Behavior |
| Azure Virtual Desktop | 9cdead84-a844-4324-93f2-b2e6bb768d07 | When a user subscribes to Azure Virtual Desktop, manually refreshes their list of resources, and authenticates to the Azure Virtual Desktop Gateway during a connection, reauthentication is enforced.After the reauthentication period expires, background feed refresh and diagnostics upload silently fail until the user completes their next interactive sign-in to Microsoft Enterprise |
The above is the App Name and ID which you should look.
If you don’t find the app follow the below steps.
(If it’s not showing anything, that means Microsoft Desktop Virtualization resource is not registered in your Azure Subscription.)
Here, is the step-by-step process to register the resource in Azure Portal.
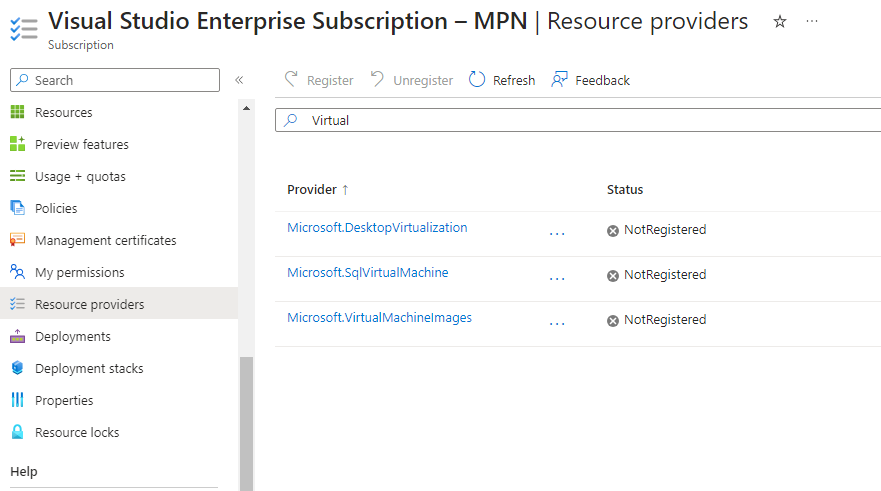
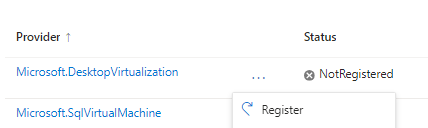
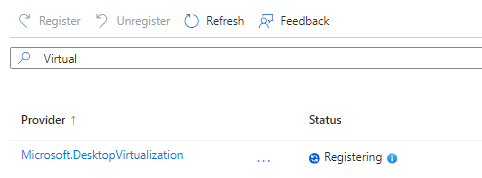
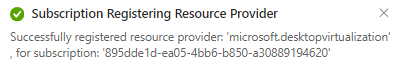
Once you register the resource, you should be able to see the Azure Virtual Desktop application in drop down list.
- Under Assignments > Conditions, select 0 conditions select.
- Under Client apps, select Not Configured.
- On the new pane that opens, for Configure, select Yes.
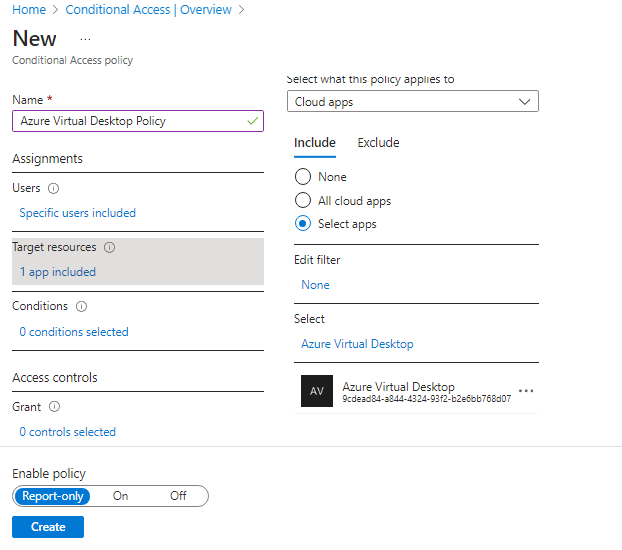
- Select the client apps this policy applies to:
- Select Browser if you want the policy to apply to the web client.
- Select Mobile apps and desktop clients if you want to apply the policy to other clients.
- Select both check boxes if you want to apply the policy to all clients.
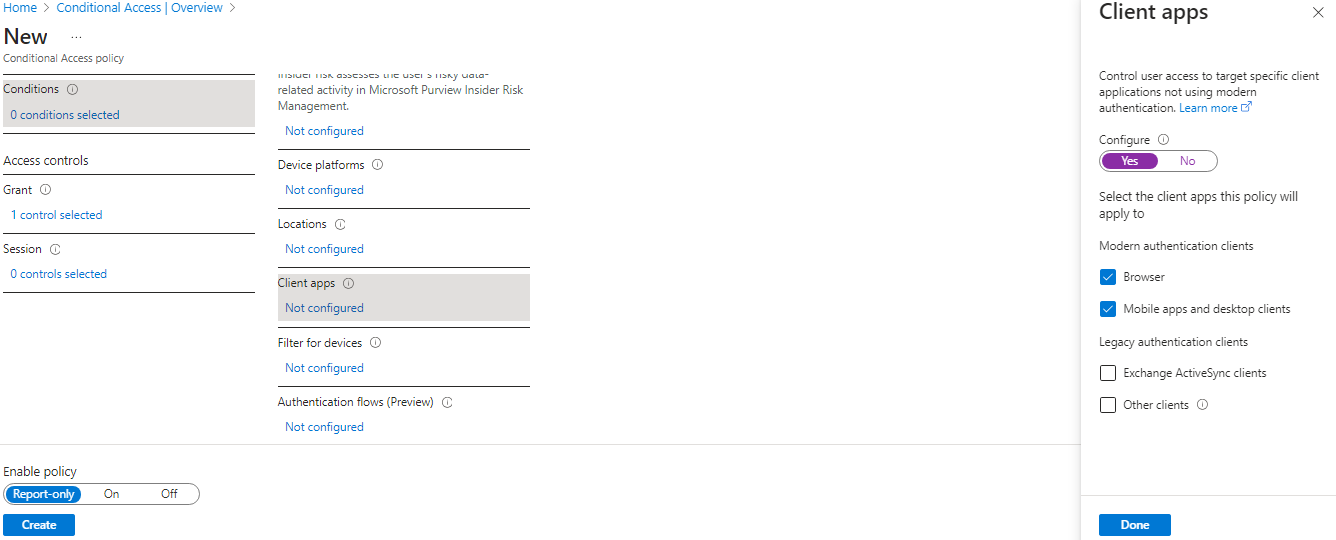
- Deselect values for legacy authentication clients.
- Check Require multifactor authentication, and then select Select.
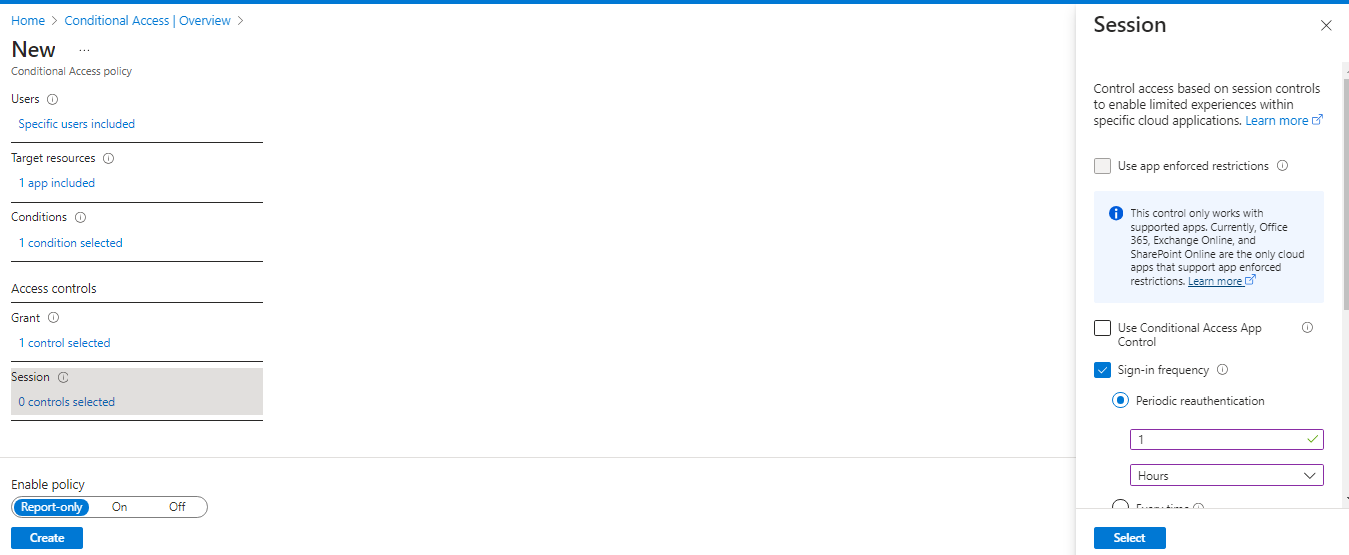
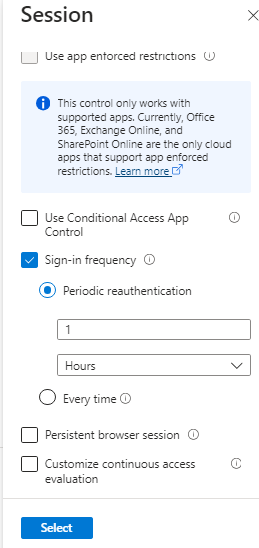
- In the last step select the session, select the sign in frequency, If you select Periodic reauthentication, set the value for the time period after which a user is asked to sign-in again, and then select Select. For example, setting the value to 1 and the unit to Hours, requires multifactor authentication if a connection is launched more than an hour after the last one.
- At the bottom of the page, set Enable policy to On and select Create.

Please note the following points.
Reauthentication occurs solely when a user needs to authenticate access to a resource. Once a connection is established, users are not prompted for reauthentication, even if the connection persists beyond the sign-in frequency you’ve set.
However, users will be required to reauthenticate if a network disruption necessitates the session to be re-established after the configured sign-in frequency. This may result in more frequent authentication requests, particularly on unstable networks.
Also, Every time option is currently available in public preview and is only supported when applied to the Microsoft Remote Desktop and Windows Cloud Login apps when single sign-on is enabled for your host pool. If you select Every time, users are prompted to reauthenticate after a period of 5 to 15 minutes after the last time they authenticated for the Microsoft Remote Desktop and Windows Cloud Login apps.
In conclusion, safeguarding Azure Virtual Desktop environments requires a proactive approach to security. By implementing Microsoft Entra multifactor authentication and fine-tuning authentication frequency through Conditional Access policies, organizations can fortify their defenses against evolving cyber threats while enabling seamless user access.
That’s all for today, I hope you will like this article.


