Citrix Cloud Workspace – How to configure Ping ID as the secondary IDP (MFA) when the Primary IDP is Azure AD
Hi friends, I hope you are all doing well, IDAM or Identity and Access Management sometimes become very critical and it can make or break an entire VDI design. In today’s post I am going to show you one complex IDAM integration for the Citrix Cloud Workspace. This integration involves working on with the three PaaS platform like Citrix Cloud, Ping One and Microsoft Azure.
The integration for any 3rd party ID provider for MFA for Citrix Workspace was always a challenging task since different teams were involved in an enterprise, but this process is not so difficult if you know how you are going to do this task.
In Citrix cloud one of the most widely used authentication method for Citrix Workspace now a days is Azure AD Authentication. In my demo lab I will show you today, how to enable the MFA for the Azure AD Authenticated VM with Ping ID.
First login to the citrix cloud portal by going to the URL https://us.cloud.com
Once you log in go the hamburger menu and click on Workspace configuration
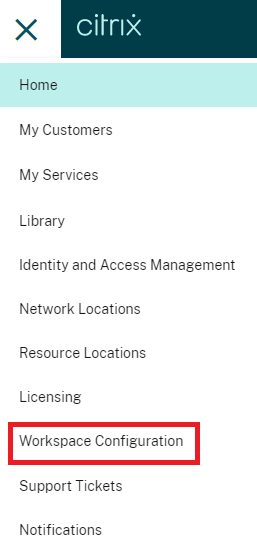
Once you go there navigate to workspace Authentication and you can this below
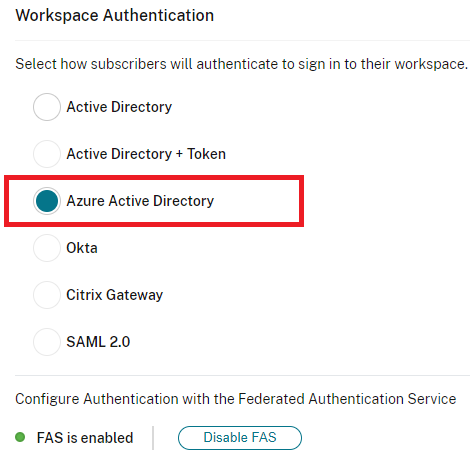
Now in Let’s see how you can configure the PingFederate
Log in to the https://admin.pingone.com/
Once you login to the PingID Portal, you can go to the PingID SDK tab.
Go to integrate with PingID SDK tab
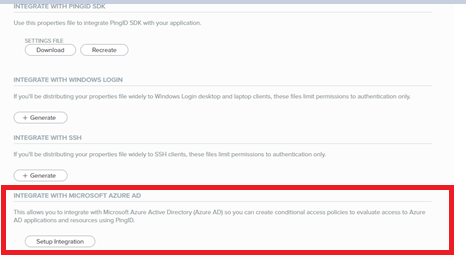
Now, login to Azure Portal at https://portal.azure.com
In the next step you can paste the Azure AD Tenant Id which you can copy from your Azure AD in the Azure Portal.
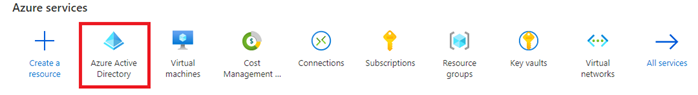
You can get the Tenant ID details below, just copy that.
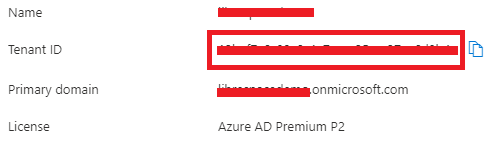
Now, go back to the Ping one portal, and you can paste the Azure ID details.
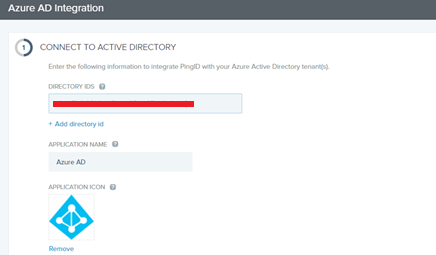
In next step you need to grant the permission to the Azure AD
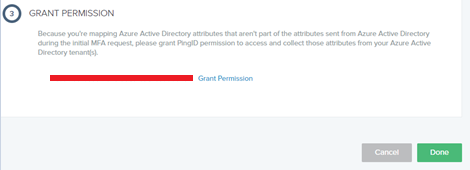
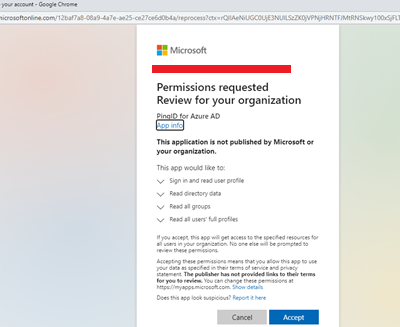
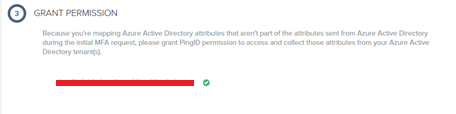
Now, in next step copy the custom conditional access JSON from the PingOne Portal.
Custom Conditional Access
JSON

Now you need to again go back to the Azure Portal and then go the Azure Active Directory. And go to the Security and Conditional Access.

Next go the conditional access.
In the next step go to the new custom control section in the conditional access policy. Here you just need to paste the code which you have just copied.
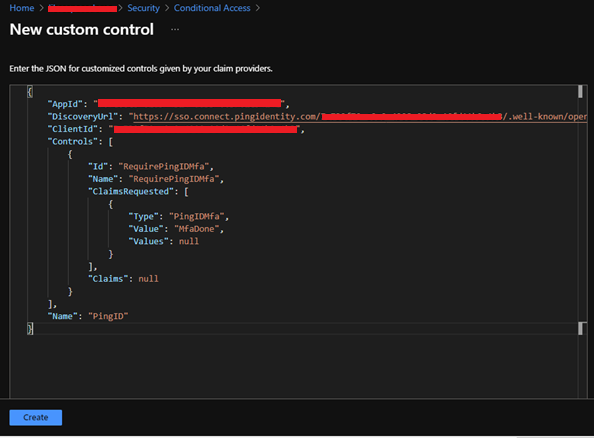
Now click on create.
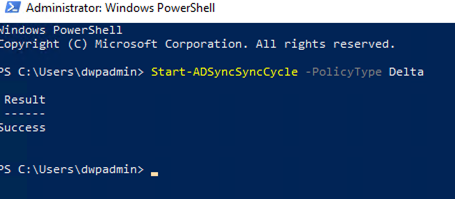
Now let’s create a security group in Active Directory and add few users to it for Ping ID MFA, once the group is created please run the below command for the quick sync of the Active Directory Details with Azure AD. (Please note this is only applicable for the Hybrid Azure AD Scenario).
In my case the group which I have created for this is the PingIDMFA
Next Again go back to the Azure AD. And go to the conditional access and create a new conditional access policy.

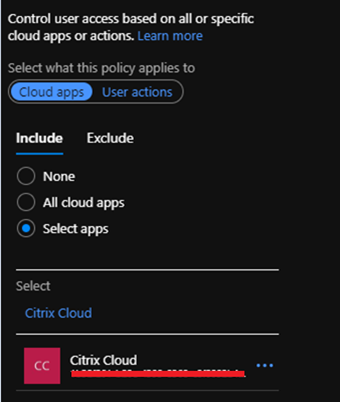
In the select users and groups select the PingIDMFA group, in next step select the Cloud Apps group, here you need to select the correct Citrix Cloud App Group, if you have multiple citrix cloud application registered as Enterprise Application in your Azure AD like I have, please check the application ID first from Enterprise Application list in Azure AD and then come back here and select the right Application for the Citrix Cloud registered in your Azure AD as shown below.

Now select the Cloud Apps
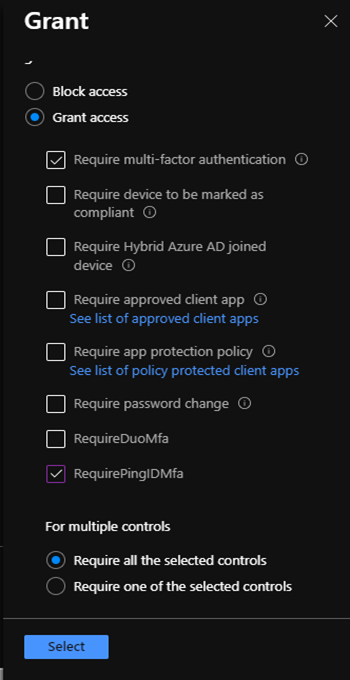
And Grant the required multi factor authentication as shown below
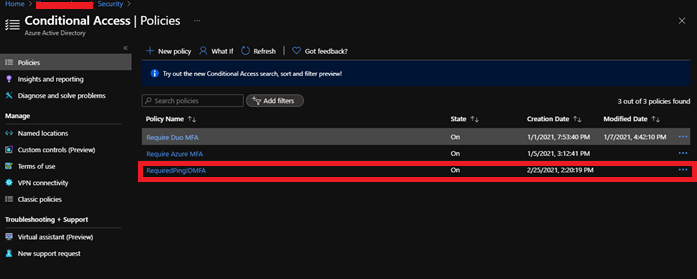
Once the Policy is created you can see below
That’s it, you are all set, now download the PingID mobile app from the google play store if you are using Android mobile devices and configure the MFA, you will see a prompt like this.

Once you scan it will do the azure AD authentication.
Now go to the citrix workspace portal or workspace app and enter your UPN of Azure AD and pass the authentication prompt for the PingID MFA and you can get inside your workspace.
That’s all for today, although it’s little complex since we have to work with multiple cloud providers, but this will be real good experience. I hope you will like this post. You have a good day ahead.


