Create a site to site VPN tunnel from on premise to Azure with very minimal cost for your home or small office.
Dear readers, in my today’s post I will show you how to create a site to site VPN connection for small office from Azure, for this setup I have deployed the VPN router called TPLINK TR-ER604W. There is no information available in the Azure website about the support of this router however I have decided to test this one. This TPLINK router I have bought from Amazon India during the Amazon prime sale and I have got a very good deal of around INR 10K, which come around USD 150.
Step 1: Configure the Azure Side.
In this process the first step is to add your on premise DNS server to Azure, which I have added long time back in the classic portal and here is a screen shot of that time.
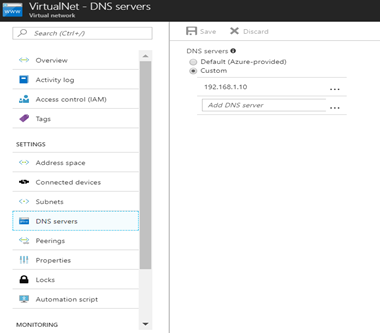
In the new portal it’s showing in my VNET tile once you will click on the DNS servers as you can see below.
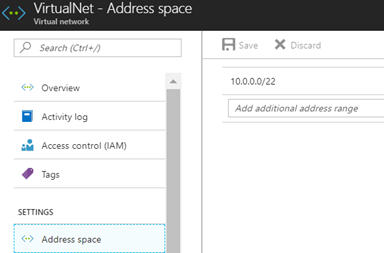
Now I already have a VNET in my resource group and the following address space is attached to that.
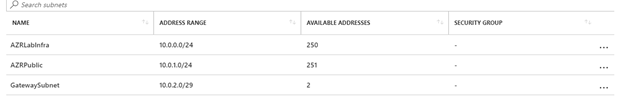
This is the subnet which are the part of the VNET are shown below.
Now I have decided to create a local gateway because without a local gateway my Azure resources will not be able to talk with the on premise VM. In the IP address field I need to add the public IP address of my home router and in the address space I have decided to the address range of 192.168.1.0/24. Please note that my on premise servers are in the same IP subnet.
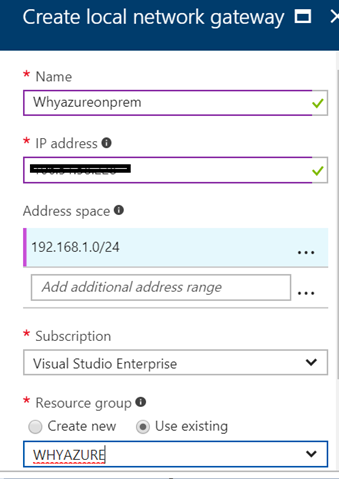
In my next step I have decided to create a VPN gateway as shown below. I have chosen a Policy-based VPN type because my on premise router doesn’t support Route-based policies.
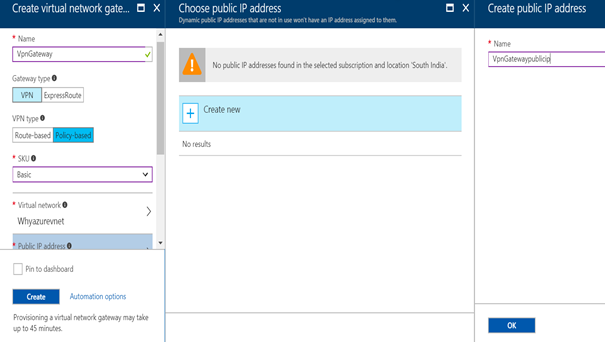
Once I click on create it took almost 20 minutes to provision the VPN gateway as you can see below.
Now in the next step I need to add a connection with the help of this VPN gateway to my on premise VPN router. So I have clicked on the Add Connection tab and chosen the Site-to-site (IPsec) connection.
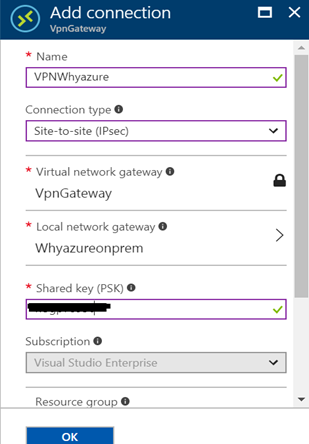
Please note down the shared key (PSK).
Once the VPN gateway is created, it will automatically get a public IP, I have noted down the public IP address which I will use in the configuration of my on premise gateway.
Now the configuration has been completed in the Azure side so I have decided to complete the configuration in the on premise VPN router.
Step 2: Configure the On-Premise VPN router.
First I need to login to my router web console. I will click on the VPN tab.
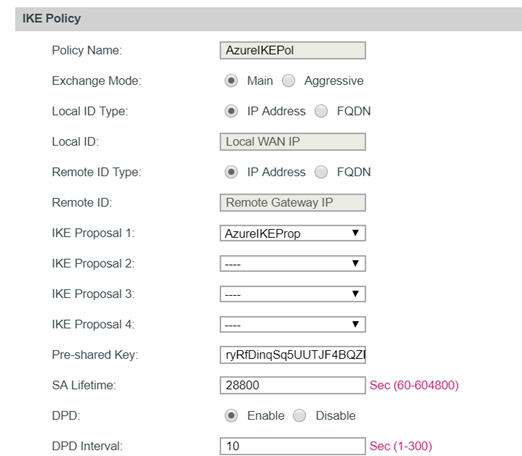
The next step is to go the IKE tile and create an IKE policy
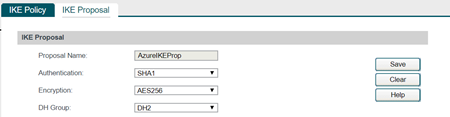
The next step is to go to create a proposal. Please note that you can create multiple policy however only one proposal can be associated with a policy.
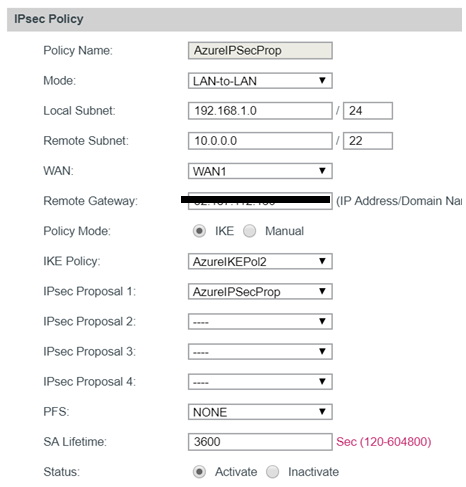
Once the proposal is created I will go the IPSec tab and I will create an IPSec policy.
The next step is to create the IPSec Proposal
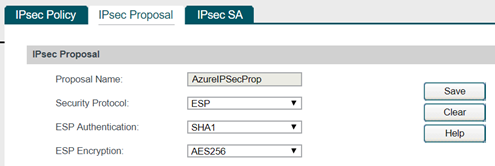
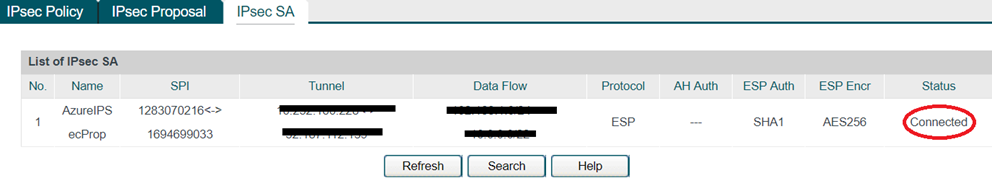
Once this is create I will go the IPsec SA tab and after waiting for few minutes I can see the VPN tunnel between Azure and on premise network has been established as you can see below. As you can see the status is connected as below.
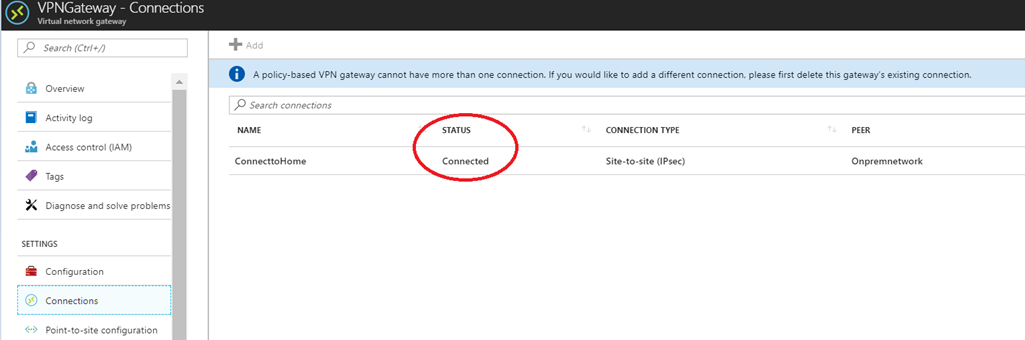
Now I went to the Azure portal to see what is going on there. When I click on the connection tab under VPN gateway connection settings it is showing connected.
That’s all what we have to do, now I can ping my VM which is on Azure from my on premise VM.
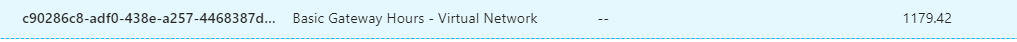
So looks like it’s very cool to setup a site to site VPN with Azure, however there is a catch here. Once you setup a VPN tunnel you can’t switch it off until unless you delete it complete. And it will cost you INR 2K or USD 30 approximately to run full month. As you can see below.
So how it is? I hope you like this post, I will bring more on Azure Networking in my future posts. Thank you and have a nice day.


good information
thanks for sharing