What is Azure Virtual Desktop (AVD)?
Today I will discuss a beginner’s guide for Azure Virtual Desktop.
Overview
Azure Virtual Desktop is a desktop and app virtualization service that runs on the cloud.
Here’s what you can do when you run Azure Virtual Desktop on Azure:
- Set up a multi-session Windows 10 or Windows 11 deployment that delivers a full Windows 10/11 with scalability.
- Virtualize Microsoft 365 Apps for enterprise and optimize it to run in multi-user virtual scenarios.
- Provide Windows 7 virtual desktops with free Extended Security Updates.
- Bring your existing Remote Desktop Services (RDS) and Windows Server desktops and apps to any computer.
- Virtualize both desktops and apps.
- Manage Windows 10 and Windows 11, Windows Server, and Windows 7 desktops and apps with a unified management experience.
AVD Management Control Plane:
Microsoft manages the following Azure Virtual Desktop services as part of Azure:

Let’s see what are the components of Azure Virtual Desktop (AVD)
Web Access
The Web Access service within Window Virtual Desktop lets user’s access virtual desktops and remote apps through an HTML5-compatible web browser as they would with a local PC, from anywhere on any device. Web Access is secured for Diageo users using OKTA multifactor authentication.
Gateway
The Remote Connection Gateway service connects remote users to Azure Virtual Desktop apps and desktops from any internet-connected device that can run a Azure Virtual Desktop client. The client connects to a gateway, which then orchestrates a connection from a VM back to the same gateway.
Connection Broker
The Connection Broker service manages AVD user connections to virtual desktops and remote apps. The Connection Broker provides load balancing and reconnection to existing sessions.
Diagnostics
Remote Desktop Diagnostics is an event-based aggregator that marks each user and administrator action on the Azure Virtual Desktop deployment as a success or failure. AVD Administrators can query the event aggregation to identify failing components as per requirements.
Extensibility components
Azure Virtual Desktop includes several extensibility components. Azure Virtual Desktop can be managed using Windows PowerShell or with the provided REST APIs, which also enable support from third-party tools. AVD team is using Azure ARM/GUI for AVD management for this deployment.
Components you manage include:
Customers manage these components of Azure Virtual Desktop solutions:
- Azure Virtual Network: Azure Virtual Network lets Azure resources like VMs communicate privately with each other and with the internet. By connecting Azure Virtual Desktop host pools to an Active Directory domain, you can define network topology to access virtual desktops and virtual apps from the intranet or internet, based on organizational policy. You can connect a Azure Virtual Desktop to an on-premises network using a virtual private network (VPN), or use Azure ExpressRoute to extend the on-premises network into the Azure cloud over a private connection.
- Azure AD: Azure Virtual Desktop uses Azure AD for identity and access management. Azure AD integration applies Azure AD security features like conditional access, multi-factor authentication, and the Intelligent Security Graph, and helps maintain app compatibility in domain-joined VMs.
- AD DS: Azure Virtual Desktop VMs must domain-join an AD DS service, and the AD DS must be in sync with Azure AD to associate users between the two services. You can use Azure AD Connect to associate AD DS with Azure AD.
- Azure Virtual Desktop session hosts: A host pool can run the following operating systems:
- Windows 7 Enterprise
- Windows 10 Enterprise
- Windows 10 Enterprise Multi-session
- Windows Server 2012 R2 and above
- Custom Windows system images with pre-loaded apps, group policies, or other customizations
- You can choose VM sizes, including GPU-enabled VMs. Each session host has a Azure Virtual Desktop host agent, which registers the VM as part of the Azure Virtual Desktop workspace or tenant. Each host pool can have one or more app groups, which are collections of remote applications or desktop sessions that users can access.
- Azure Virtual Desktop workspace: The Azure Virtual Desktop workspace or tenant is a management construct to manage and publish host pool resources.
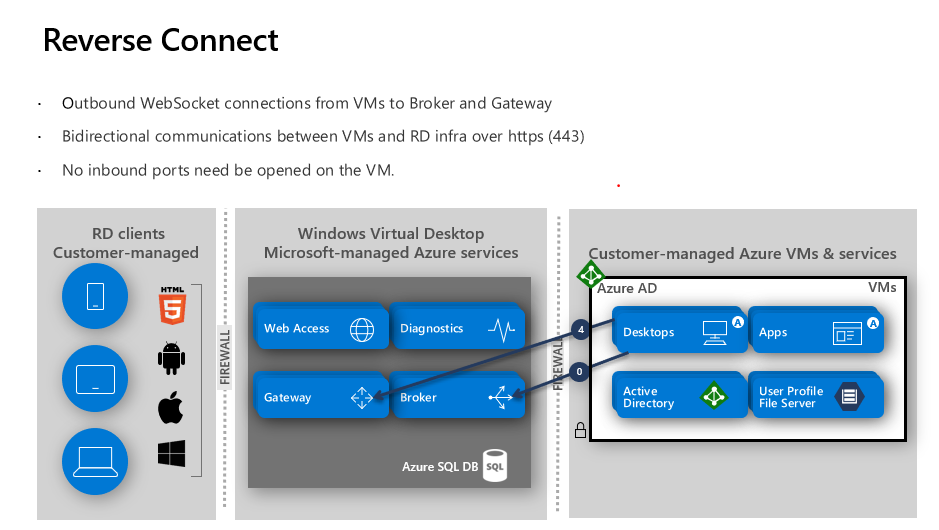
One of the key design features of VWD is reverse connect
Azure Virtual Desktop is using reverse connect transport for establishing the remote session and for carrying RDP traffic. Unlike the on-premises Remote Desktop Services deployments, reverse connect transport doesn’t use a TCP listener to receive incoming RDP connections. Instead, it is using outbound connectivity to the Azure Virtual Desktop infrastructure over the HTTPS connection.
Reverse Connect enables you to access your VMs without having to keep outbound ports open
There is no requirement for any inbound ports to be configured or opened on a VM to setup a RDP connection on AVD. This is essentially a reverse proxy security feature straight out of the box. Communication between the host pool/s and AVD core SaaS components is completed using TCP https (443) only (at time of writing). For those using third party firewall’s/security appliances, you may need to double check rules allowing access to Azure services.
Reverse connect also provides new benefits like setting policies including conditional access policies. For example; Client time of day restrictions via IP address, controlling access via the Client IP address, time and/or other
Additional Security:
Azure Network Security Groups and Azure Firewall allow you to control traffic to/from your virtual network
How Reverse Connect works:
- A user launches the RD Client, they enter in their credentials and authenticate with Azure AD. on successful sign in, Azure AD returns a token to the RD Client.
- The RD Client then presents a token to the Web Access component, the Broker service then query’s the SQL Database to determine the available and authorized resources for that user.
- The user selects and clicks on the chosen resource and connects to the Gateway.
- The broker service then orchestrates the connection from the host agent to the Gateway.
- The User is then able to access and use resources requested (Desktops/Apps).
AVD User Connection Traffic flow
AVD uses Reverse Connect, which means that no inbound ports need to be opened on the VM to set up the RDP connection. Once the connection flow proceeds, bidirectional communication between session hosts/host pools will go over port https (443).
Azure Virtual Desktop is a global load balanced service via Azure front-door. This means that the traffic flow always goes via the nearest management control-plane/service location.
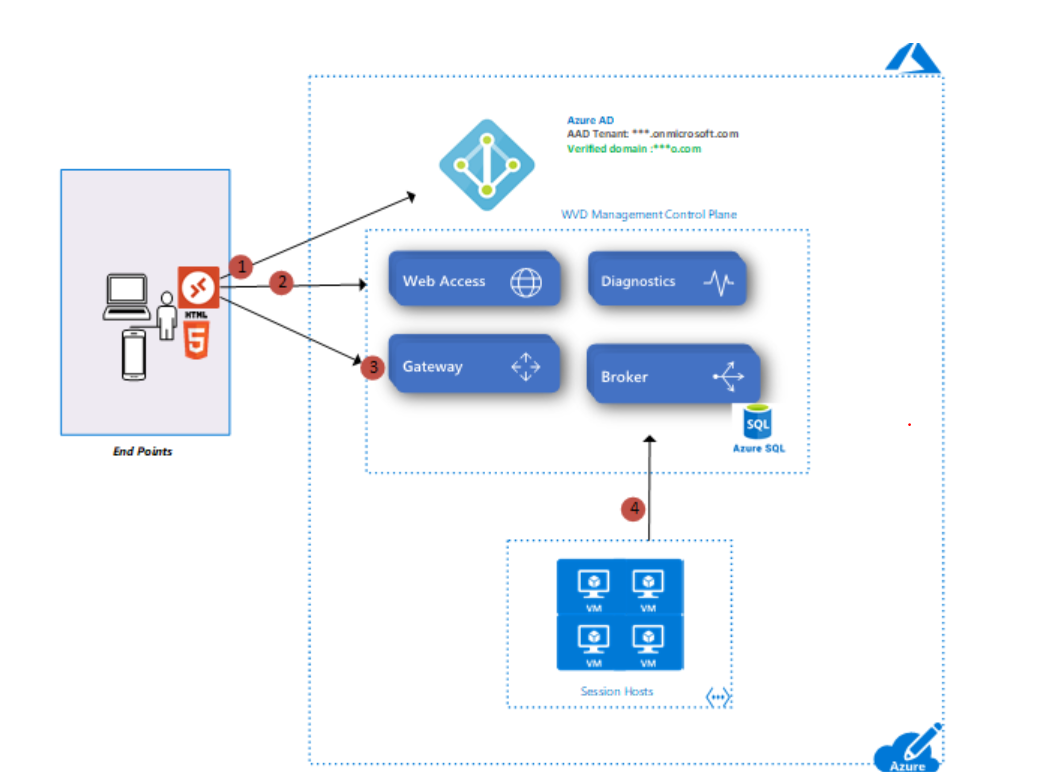
Connection flow:
-
- User connects to Web URL (browser/native client).
- If they do not have their Azure AD token -> redirect to their Azure AD tenant for sign in (MFA, conditional, etc) -> get token, present to Web URL
- Web Access -> Broker: does this user have any resources?
- Broker queries DB -> returns list of apps / desktops
- User clicks on an icon -> client connects to global gateway URL, which goes to Broker
- Broker orchestrates connection. This is done via connection marked 0. This is a heartbeat coming from every VM – bidirectional socket connection.
- First, we need to go through load balancing, then broker connects to the VM -> VM connects to the gateway so that the user can access the resource (connection 4).
- Now Gateway will route traffic between two end points in the secure fashion…
General Hierarchy
Host Pools
Host pools are a collection of one or more identical virtual machines within Azure Virtual Desktop tenant environments. Each host pool can be associated with multiple RemoteApp groups, one desktop app group, and multiple session hosts. Host Pools can be one of two types:
Personal, where each session host is assigned to individual users.
Pooled, where session hosts can accept connections from any user authorized to an application group within the host pool. You can set additional properties on the host pool to change its load-balancing behavior, how many sessions each session host can take, and what the user can do to session hosts in the host pool while signed in to their Azure Virtual Desktop sessions. You control the resources published to users through application groups.
Application Groups
An Application group is a logical grouping of applications installed on session hosts in the host pool. An application group can be one of two types:
RemoteApp, where users access the RemoteApps you individually select and publish to the application group.
Desktop, where users access the full desktop By default, a desktop application group (named “Desktop Application Group”) is automatically created whenever you create a host pool. You can remove this application group at any time. However, you can’t create another desktop application group in the host pool while a desktop application group already exists. To publish RemoteApps, you must create a RemoteApp application group. You can create multiple RemoteApp application groups to accommodate different worker scenarios. Different RemoteApp application groups can also contain overlapping RemoteApps.
Workspaces
A workspace is a logical grouping of application groups in Azure Virtual Desktop. Each Azure Virtual Desktop application group must be associated with a workspace for users to see the remote apps and desktops published to them.
End users
After you’ve assigned users to their application groups, they can connect to a Azure Virtual Desktop deployment with any of the Azure Virtual Desktop clients.
That’s all for today, I hope you have a very good idea now for Azure Virtual Desktop. You have a great day ahead.